Remote control overview – Linx Technologies LICAL-ENC-HS001 User Manual
Page 6
– –
– –
6
7
Remote Control Overview
Wireless remote control is growing in popularity and finding its way into
more unique applications. Remote Keyless Entry (RKE) systems for
unlocking cars or opening garage doors quickly come to mind, but how
about a trash container that signals the maintenance office when it needs
to be emptied? The idea behind remote control is simple: a button press or
contact closure on one end causes some action to be taken at the other.
Implementation of the wireless RF stage has traditionally been complicated,
but with the advent of simpler discrete solutions and modular products,
such as those from Linx, implementation has become significantly easier.
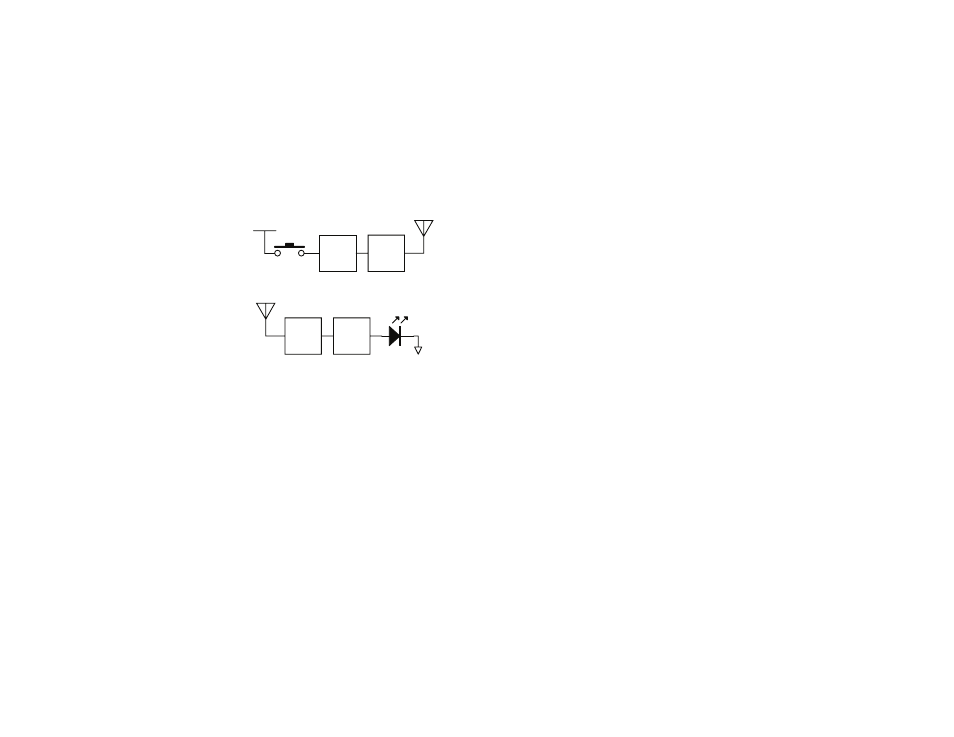
Encoder and decoder ICs are generally
employed to maintain the security
and uniqueness of a wireless RF or IR
link. These devices encode the status
of inputs, usually button or contact
closures, into a data stream suitable for
wireless transmission. Upon successful
recovery and validation, the decoder’s
outputs are set to replicate the states
of the encoder’s inputs. These outputs
can then be used to control the circuitry
required by the application.
Prior to the arrival of the Linx HS Series, encoders and decoders
typically fell into one of two categories. First were older generation,
low-security devices that transmitted a fixed address code, usually set
manually with a DIP switch. These products were easy to use, but had
significant security vulnerabilities. Since they sent the same code in every
transmission, they were subject to code grabbing. This is where an
attacker records the transmission from an authorized transmitter and then
replays the transmission to gain access to the system. Since the same
code is transmitted every time, the decoder has no way to validate the
transmission.
These concerns resulted in the development of a second type of encoder
and decoder that focused on security and utilized a changing code to
guard against code grabbing. Typically, the contents of each transmission
changes based on complex mathematical algorithms to prevent someone
from reusing a transmission. These devices gained rapid popularity
due to their security and the elimination of manual switches; however,
they imposed some limitations of their own. Such devices typically offer
a limited number of inputs, the transmitter and receiver can become
desynchronized, and creating relationships and associations among groups
of transmitters and receivers is difficult.
The HS Series offers the best of all worlds. The HS Series uses an
advanced high security encryption algorithm called CipherLinx™ that
never becomes desynchronized or sends the same packet twice. It is
easily configured without production programming and allows for “button
level” permissions and unique encoder and decoder relationships. Eight
inputs are available, allowing a large number of buttons or contacts to be
connected.
To learn more about different encoder and decoder methodologies, please
refer to Application Note AN-00310.
DEC
Rx
GND
HS
Series
ENC
VCC
Tx
HS
Series
LR
Series
LR
Series
Figure 8: Remote Control Block Diagram