Verifying the configuration, Network requirements, Configuring secpath b – H3C Technologies H3C SecPath F1000-E User Manual
Page 49
42
<SecPathC> system-view
[SecPathC] ipv6
# Configure a static route to the subnet with the NAT-PT prefix.
[SecPathC] ipv6 route-static 3001:: 16 2001::1
Verifying the configuration
If you carry out the ping ipv6 3001::0800:0002 command on SecPath C after completing the
configurations, response packets can be received.
You can see on SecPath B the established NAT-PT session.
<SecPathB>display session table verbos
Initiator:
Source IP/Port : 2001::0002/32768
Dest IP/Port : 3001::0800:0002/43984
VPN-Instance/VLAN ID/VLL ID:
Responder:
Source IP/Port : 8.0.0.2/0
Dest IP/Port : 9.0.0.10/12289
VPN-Instance/VLAN ID/VLL ID:
Pro: ICMPv6(58) App: unknown State: ICMP-CLOSED
Start time: 2011-07-20 18:41:29 TTL: 26s
Root Zone(in):
Zone(out):
Received packet(s)(Init): 5 packet(s) 520 byte(s)
Received packet(s)(Reply): 5 packet(s) 420 byte(s)
Configuring static mappings on the IPv4 side and the IPv6 side
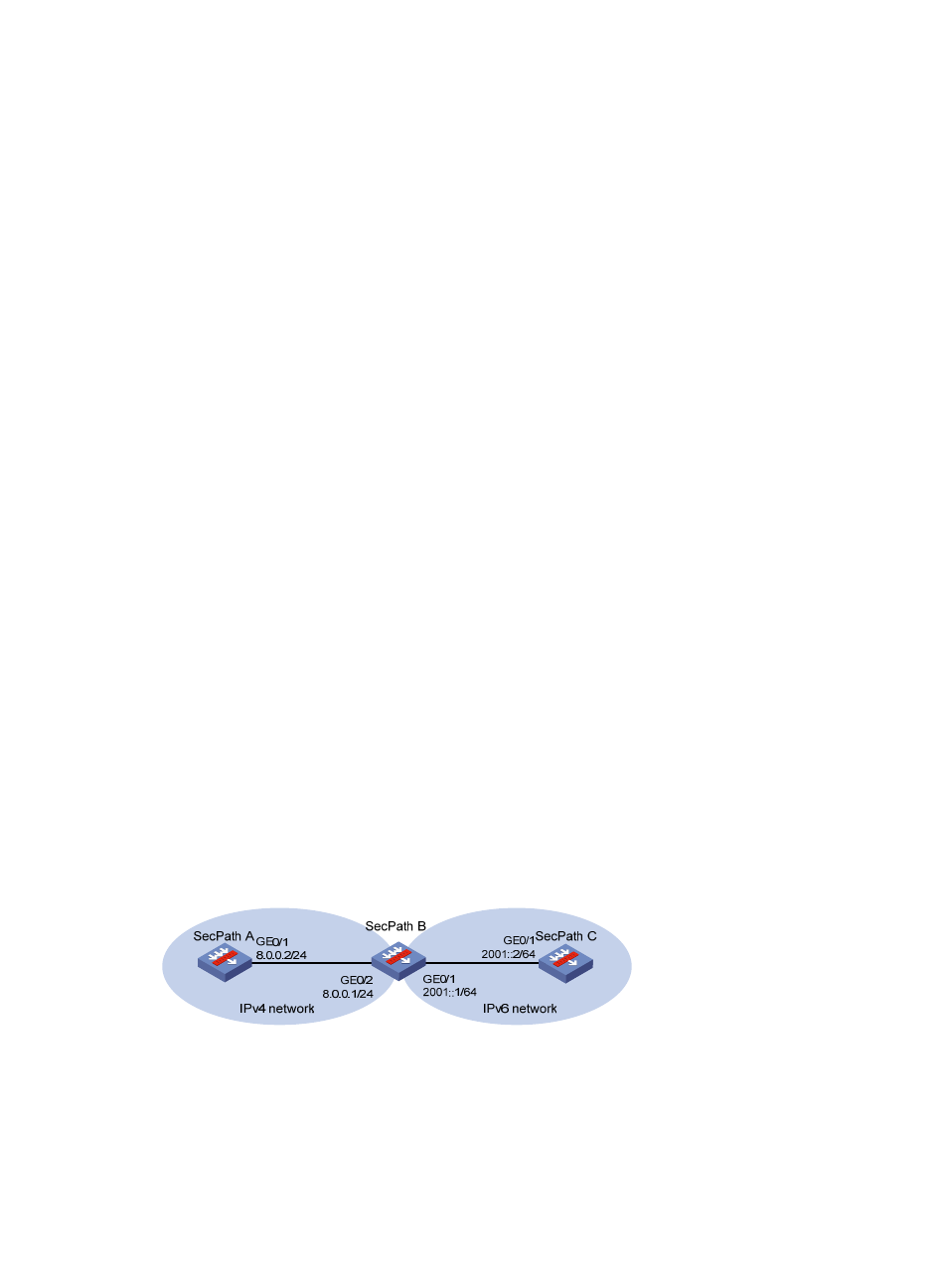
Network requirements
As shown in
, SecPath C with IPv6 address 2001::2/64 on an IPv6 network can communicate
with SecPath A with IPv4 address 8.0.0.2/24 on an IPv4 network.
To meet the preceding requirement, you need to configure SecPath B that is deployed between the IPv4
network and IPv6 network as a NAT-PT device, and configure static mappings on the IPv4 side and IPv6
side on SecPath B, so that SecPath A and SecPath C can communicate with each other.
Figure 32 Network diagram
Configuring SecPath B
# Configure interface addresses and enable NAT-PT on the interfaces.
<SecPathB> system-view
[SecPathB] ipv6
[SecPathB] interface GigabitEthernet 0/1