Packet inspection configuration example, Network requirements, Configuration procedure – H3C Technologies H3C SecPath F1000-E User Manual
Page 16
8
Item
Description
Enable WinNuke Attack Detection
Enable or disable detection of WinNuke attacks.
Enable TCP Flag Attack Detection
Enable or disable detection of TCP flag attacks.
Enable ICMP Unreachable Packet Attack Detection
Enable or disable detection of ICMP unreachable
attacks.
Enable ICMP Redirect Packet Attack Detection
Enable or disable detection of ICMP redirect attacks.
Enable Tracert Packet Attack Detection
Enable or disable detection of Tracert attacks.
Enable Smurf Attack Detection
Enable or disable detection of Smurf attacks.
Enable IP Packet Carrying Source Route Attack
Detection
Enable or disable detection of source route attacks.
Enable Route Record Option Attack Detection
Enable or disable detection of route record attacks.
Enable Large ICMP Packet Attack Detection
Enable detection of large ICMP attacks and set the
packet length limit, or disable detection of such
attacks.
Max Packet Length
Packet inspection configuration example
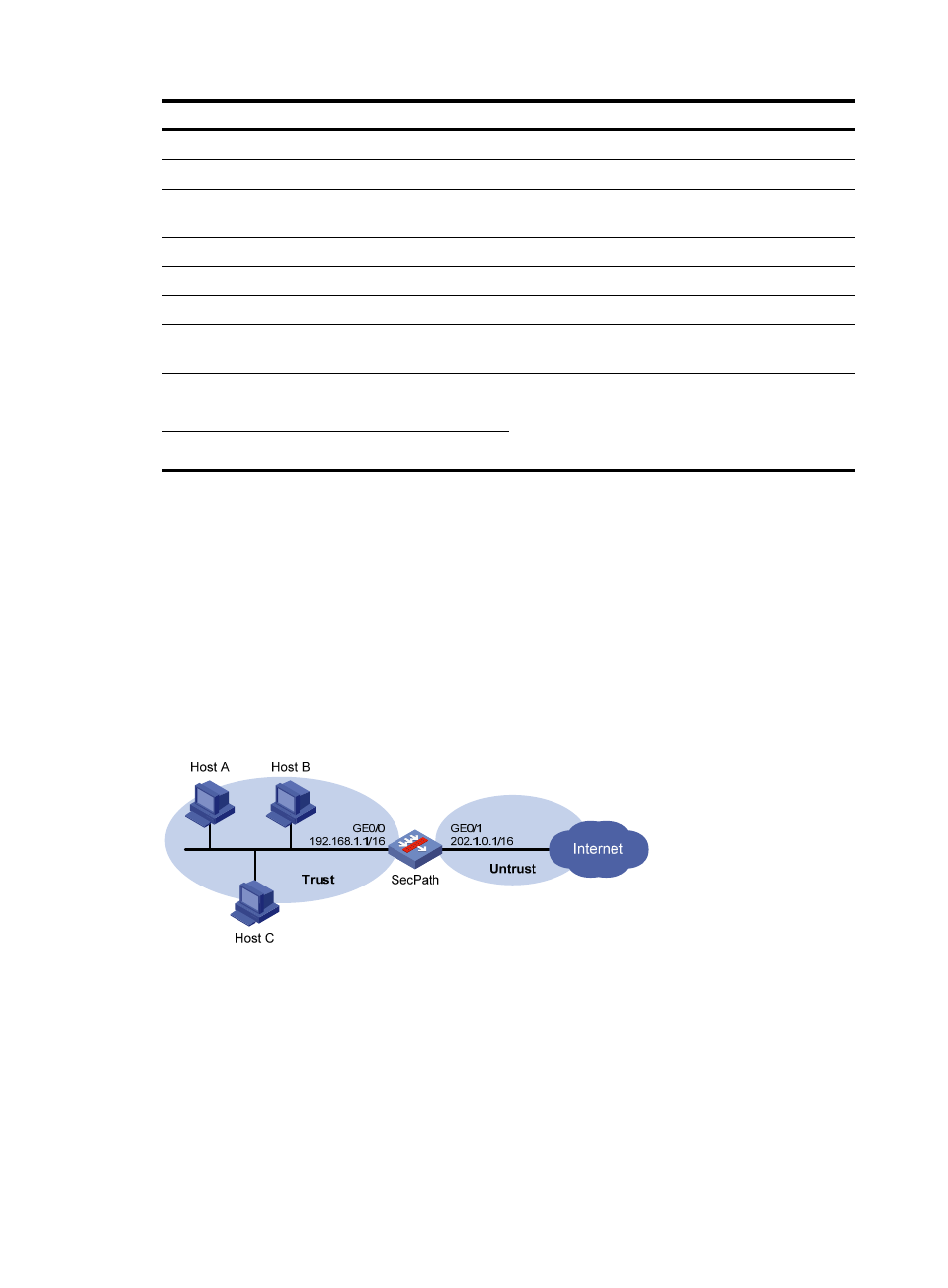
Network requirements
As shown in
, the internal network is the trusted zone and the external network is the untrusted
zone.
Configure SecPath to protect the trusted zone against Land attacks and Smurf attacks from the untrusted
zone.
Figure 9 Network diagram
Configuration procedure
1.
Assign IP addresses to interfaces. (Details not shown.)
2.
From the navigation tree, select Intrusion Detection > Packet Inspection.
The packet inspection configuration page appears.