Remote Processing RPC-52 User Manual
Page 16
RAM MEMORY
CHAPTER 5
Page 14
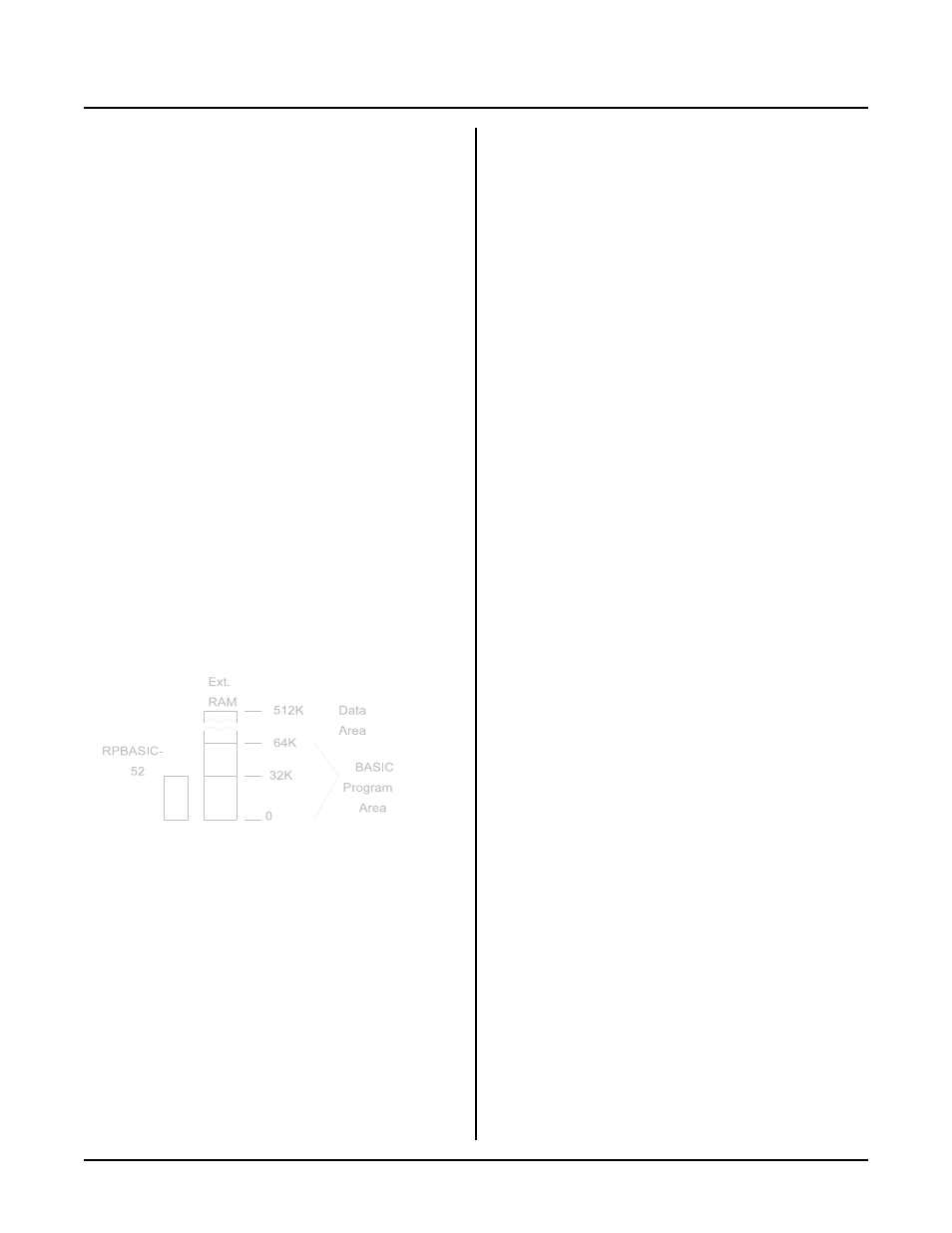
Figure 5-2 RPBASIC-52 m emory map
RESERVING MEMORY
Norm ally, RPBASIC -52 uses the first 30K of RAM for
program and variable storage. However, additional
memory can be reserved for PE EK and POKE variables
using RP BASIC -52' s CON FIG MT OP state ment.
When only a small number of variables need to be stored
(or a small assembly language program run), a 32K
RAM system may be adequate. If the combined
program and data size exceed 30K, a 128K or 512K
RAM is necessary. The additional RAM may be
necessary if your program has large arrays and/ or string
storage req uirements.
The CON FIG MT OP statement is not necessary when
you do not use RPBA SIC-52 m emor y for var iable
storage. This is possible w hen a 128K o r 512K R AM is
installed. However, you may want to set MTO P to the
top of RAM using the CON FIG M TOP com mand.
Highest MTO P value is 65535.
STORING VARIABLES IN RAM
The term "var iables" in this context includes numb ers,
strings, arr ays, recipes, or formulas as applied to your
application.
Program s and RPBASIC-52 var iables reside in segment
0. Var iables are generally stored in segment 1 and
higher (a segment is 64K of memory). See mem ory map
figure 5-2. "Extended memory" is segment 1 or higher.
PEEK and PO KE commands store and retrieve values
from memor y. For example:
20 POKE B1,12,A
puts the value of A into segment 1, address 12.
Use the PEEK statement to retrieve the variable:
50 B = PEEKB(1,12)
You can store and retrie ve strings a nd variab les in this
way. Ther e are many variations of PEEK and POKE
statements. Refer to the RPBASIC-52 Software
Supplement in this manual for additional information and
examp les. A list of comm ands appea rs at the end of this
chapter.
CORRUPTED VARIABLES
The RPC -52' s RAM is automatically battery backed up.
User defined data c an be saved when the b oard is
power ed off then on . W hen your application m ust rely
on the accuracy of this data after power up, cor rupted
variables becomes a possibility.
The nature of RAM is it is easily written to. Any
POK E' d data is susceptib le to corr uption. This is
especially true when the board is powered down. The
RPC-52 has an intelligent reset circuit which minimizes
data corruption. However, when POKEing long data,
such as strings, a reset could interr upt a saving process.
The result is information is corrupted.
Since it is impossible to predict or delay a reset, a work
around is to duplicate or triplicate POKEd values. That
is, you would have to save the same information in two
or three different places. F or purposes of discussion,
POKE d variables are called sets because data can consist
of a mixture of va riables and strings.
On power up, your program should compare values from
one set to the other one or two. If the two (or three)
agree, then there was no corruption and the program can
reliably use the values. At run time, you would read
information from set 1, but would save data to all two or
three.
The use of duplicate or triplicate sets depends upon what
the system must or can do if data is corrupted. W hen
using a duplicate set, a corrupted set indicates that
d e fa u lt va l ue s (f r om s e ri a l E E P R O M o r t he p r og r a m )
should be used, since it is uncertain if the first or second
set is corrupted. Both data sets are then re-initialized.
A triplica te set is used to r ecover the last set or ind icate
that the data in the first set is valid.
Data is written to each set in a specific and consistent
order (data to an entire set does not have to be written
to, just that element). For example, a calibration
constant is saved (POK E' d) in three different place s.
Assume that the constant was assigned address 0, 100,
and 200 in segment 1. The data is PO KEd to addr ess 0
first, then 100, then 200.
Upon reset, the calibration value is checked. If the value
at address 0 agrees with address 100 and 200, then no
corruption occurred. When address 0 and 100 agree but
not 200, then this indicates tha t a reset occ urre d at while
updating the third set. The first data set can be trusted.
The third data set simply needs to be updated.
When the first two sets do not agree, then you know that
the first data is corrupted. If the second and third set
agree, then, depe nding upon the system r equireme nts,
the first set could be "corrected" using the old data. The
user or other device could be alerted that a calibration
(or whatever) must be performed again. When all three