Displaying and maintaining public keys, Public key configuration examples, Configuring the public key of a peer manually – H3C Technologies H3C S7500E Series Switches User Manual
Page 200: Network requirements
11-5
In this task, you can configure the RSA server public key of the peer. However, the public key
configured cannot be used for identity authentication in SSH applications, which use the RSA
host public key. For more information about SSH, see SSH2.0 Configuration in the Security
Configuration Guide.
Follow these steps to import the host public key of a peer from the public key file:
To do…
Use the command…
Remarks
Enter system view
system-view
—
Import the host public key of a
peer from the public key file
public-key peer keyname
import sshkey filename
Required
Displaying and Maintaining Public Keys
To do…
Use the command…
Remarks
Display the public keys of the
local key pairs
display public-key local
{ dsa | rsa } public
Display the public keys of the
peers
display public-key peer
[ brief | name
publickey-name ]
Available in any view
Public Key Configuration Examples
Configuring the Public Key of a Peer Manually
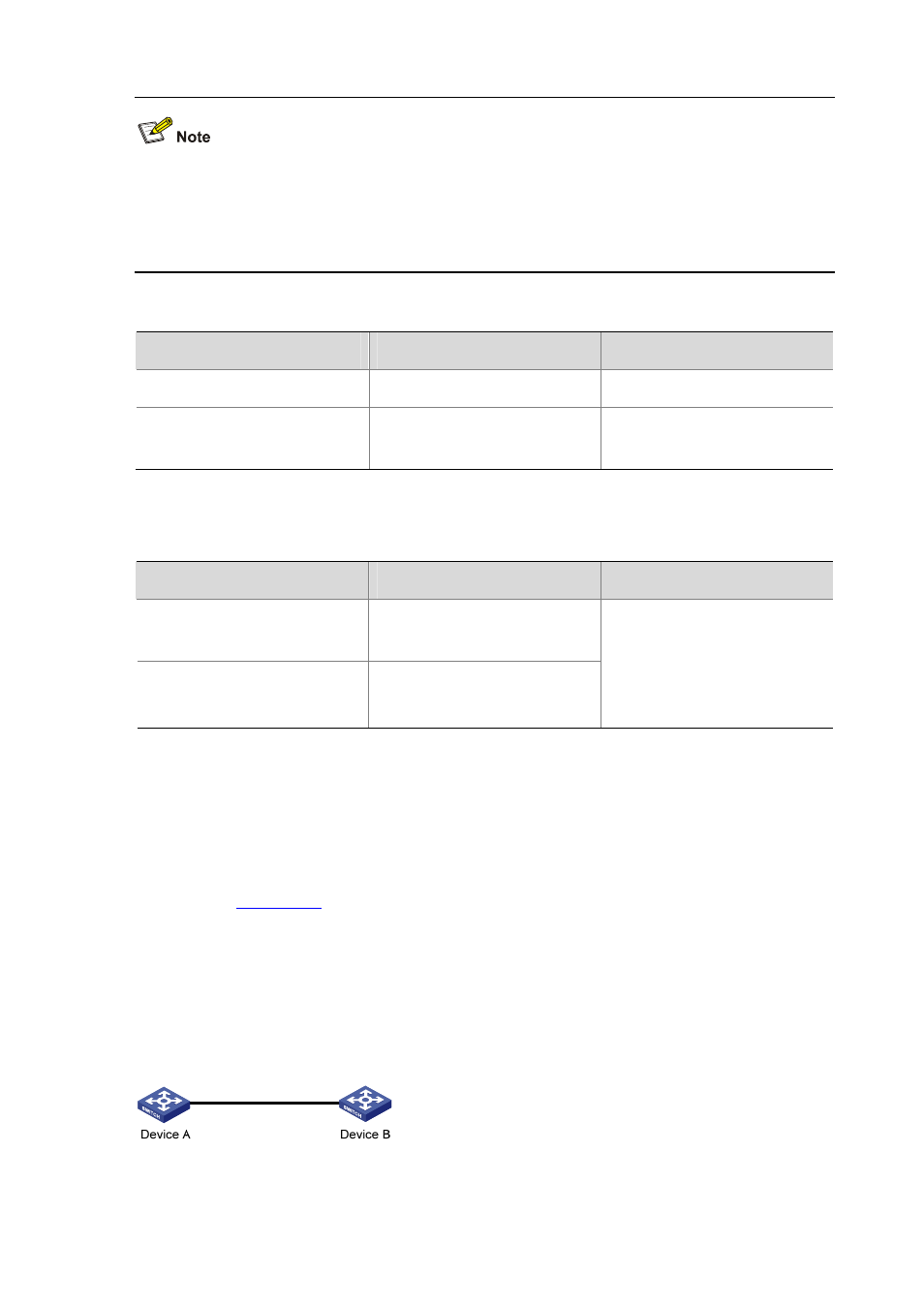
Network requirements
As shown in
, to prevent illegal access, Device B authenticates Device A through
digital signature. Before configuring authentication parameters on Device B, configure the
public key of Device A on Device B. More specifically,
z
Configure Device B to use the asymmetric key algorithm of RSA for identity authentication
of Device A.
z
Manually configure the host public key of Device A on Device B.
Figure 11-2 Network diagram for manually configuring the public key of a peer