Configuring aaa, Overview – H3C Technologies H3C S12500-X Series Switches User Manual
Page 13
1
0B
Configuring AAA
15B
Overview
Authentication, Authorization, and Accounting (AAA) provides a uniform framework for implementing
network access management. It specifies the following security functions:
•
Authentication—Identifies users and verifies their validity.
•
Authorization—Grants different users different rights and controls their access to resources and
services. For example, you can use this function to grant a user who has successfully logged in to the
device read and print permissions to the files on the device, and prevent a guest from reading or
printing the files.
•
Accounting—Records network usage details of users, including the service type, start time, and
traffic. This function enables time-based and traffic-based charging and user behavior auditing.
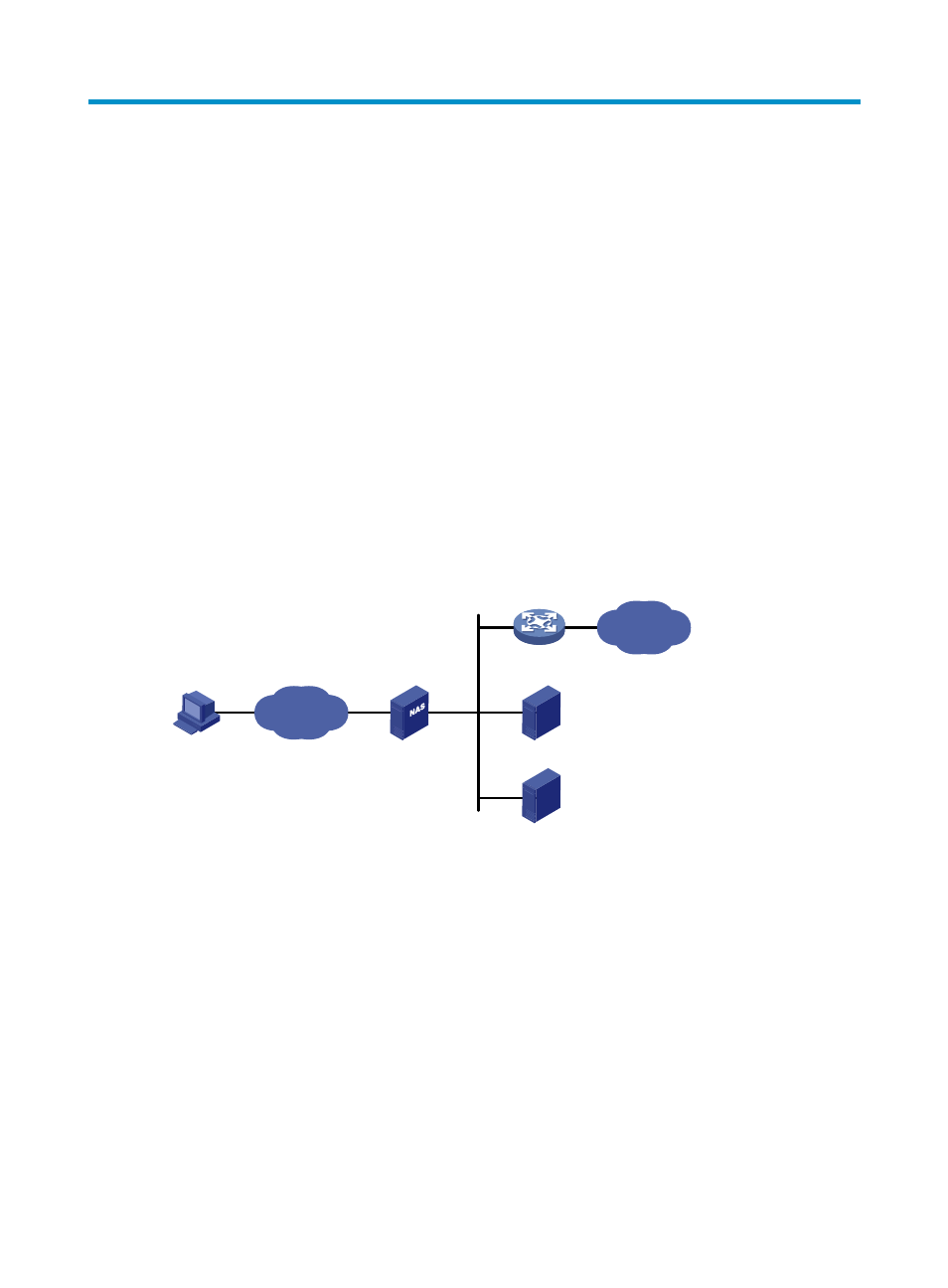
Typically, AAA uses a client/server model. The client runs on the access device, or the network access
server (NAS), which authenticates user identities and controls user access. The server maintains user
information centrally. See
674H
Figure 1
.
Figure 1 AAA network diagram
A user who wants to access networks or resources beyond the NAS sends its identity information to the
NAS, which transparently passes the user information to the servers. The servers perform user
authentication, authorization, and accounting and return the result to the NAS. Based on the result, the
NAS determines whether to permit or deny the access request.
AAA has various implementations, including RADIUS, HWTACACS, and LDAP, and RADIUS is most
often used.
The network in
675H
Figure 1
has one RADIUS server and one HWTACACS server. You can use different
servers to implement different security functions. For example, you can use the HWTACACS server for
authentication and authorization, and use the RADIUS server for accounting.
You can choose the security functions provided by AAA as needed. For example, if your company wants
employees to be authenticated before they access specific resources, you would deploy an
authentication server. If network usage information is needed, you would also configure an accounting
server.
Remote user
NAS
RADIUS server
HWTACACS server
Internet
Network
- H3C S5560 Series Switches H3C WX6000 Series Access Controllers H3C WX5000 Series Access Controllers H3C WX3000 Series Unified Switches H3C LSWM1WCM10 Access Controller Module H3C LSWM1WCM20 Access Controller Module H3C LSQM1WCMB0 Access Controller Module H3C LSRM1WCM2A1 Access Controller Module H3C LSBM1WCM2A0 Access Controller Module H3C S9800 Series Switches H3C S5130 Series Switches H3C S5120 Series Switches