Setting user group password control parameters, Ike security mechanism – H3C Technologies H3C S12500-X Series Switches User Manual
Page 164
152
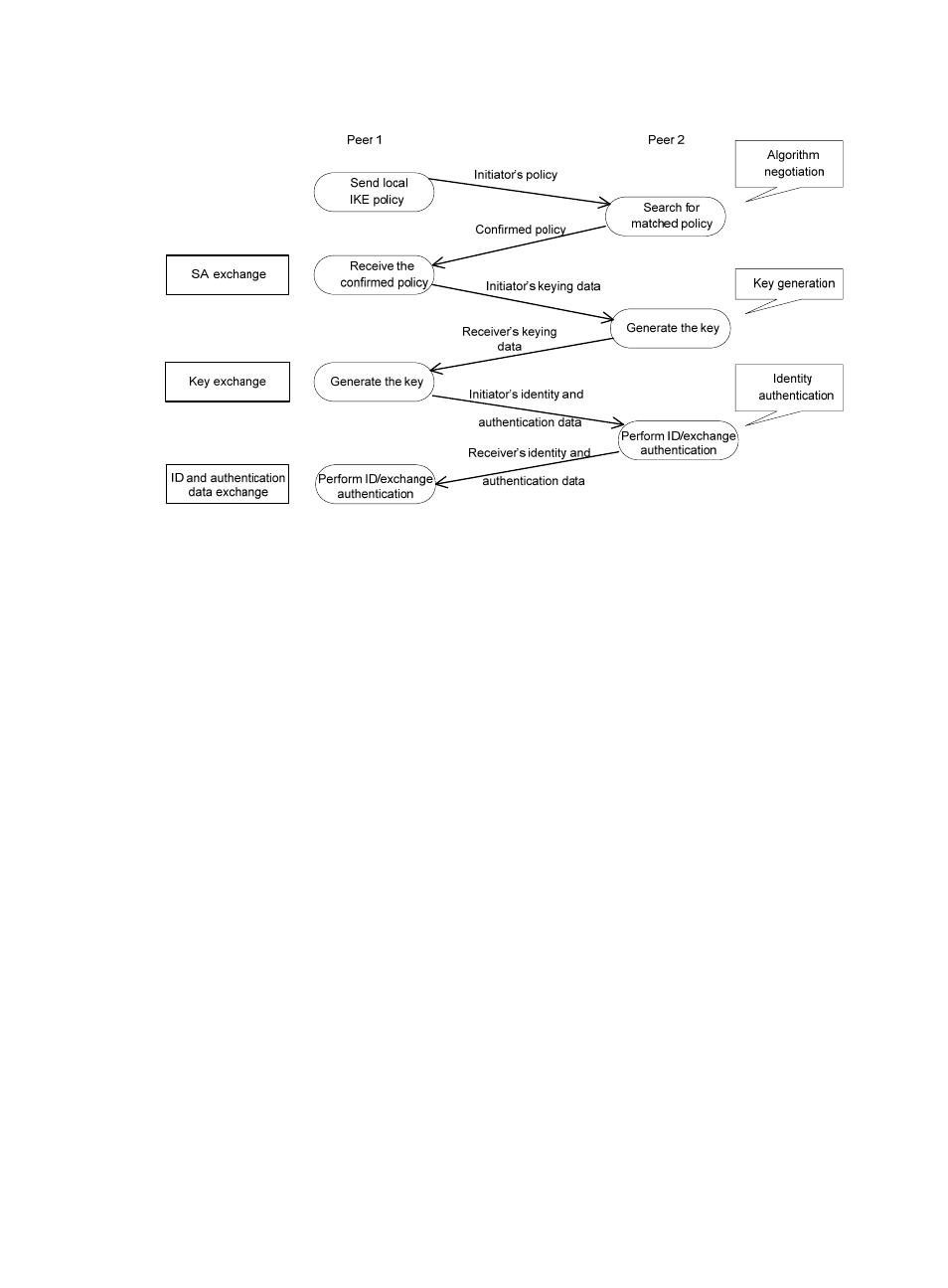
Figure 46 IKE exchange process in main mode
As shown in
859H
Figure 46
, the main mode of IKE negotiation in phase 1 involves three pairs of messages:
•
SA exchange—Used for negotiating the IKE security policy.
•
Key exchange—Used for exchanging the DH public value and other values, such as the random
number. The two peers use the exchanged data to generate key data and use the encryption key
and authentication key to ensure the security of IP packets.
•
ID and authentication data exchange—Used for identity authentication.
The main difference between the main mode and the aggressive mode is that the aggressive mode does
not provide identity information protection and exchanges only three messages, rather than three pairs.
The main mode provides identity information protection but is slower.
252B
IKE security mechanism
IKE has a series of self-protection mechanisms and supports secure identity authentication, key
distribution, and IPsec SA establishment on insecure networks.
477B
Identity authentication
The IKE identity authentication mechanism is used to authenticate the identity of the communicating
peers. The device supports the pre-shared key authentication method that two communicating peers use
the pre-configured shared key for identity authentication.
The pre-shared key authentication method does not require certificates and is easy to configure. It is
usually deployed in small networks.
478B
DH algorithm
The DH algorithm is a public key algorithm. With this algorithm, two peers can exchange keying material
and then use the material to calculate the shared keys. Due to the decryption complexity, a third party
cannot decrypt the keys even after intercepting all keying materials.
- H3C S5560 Series Switches H3C WX6000 Series Access Controllers H3C WX5000 Series Access Controllers H3C WX3000 Series Unified Switches H3C LSWM1WCM10 Access Controller Module H3C LSWM1WCM20 Access Controller Module H3C LSQM1WCMB0 Access Controller Module H3C LSRM1WCM2A1 Access Controller Module H3C LSBM1WCM2A0 Access Controller Module H3C S9800 Series Switches H3C S5130 Series Switches H3C S5120 Series Switches