KBC Networks ESML6-P3 User Manual
Page 44
Ethernet Switch User Manual
Manual_web_mgt_sw-ESML6-P3-Rev 1107
Copyright © KBC Networks Ltd. 2011
Page 43 of 51
www.kbcnetworks.com
d.
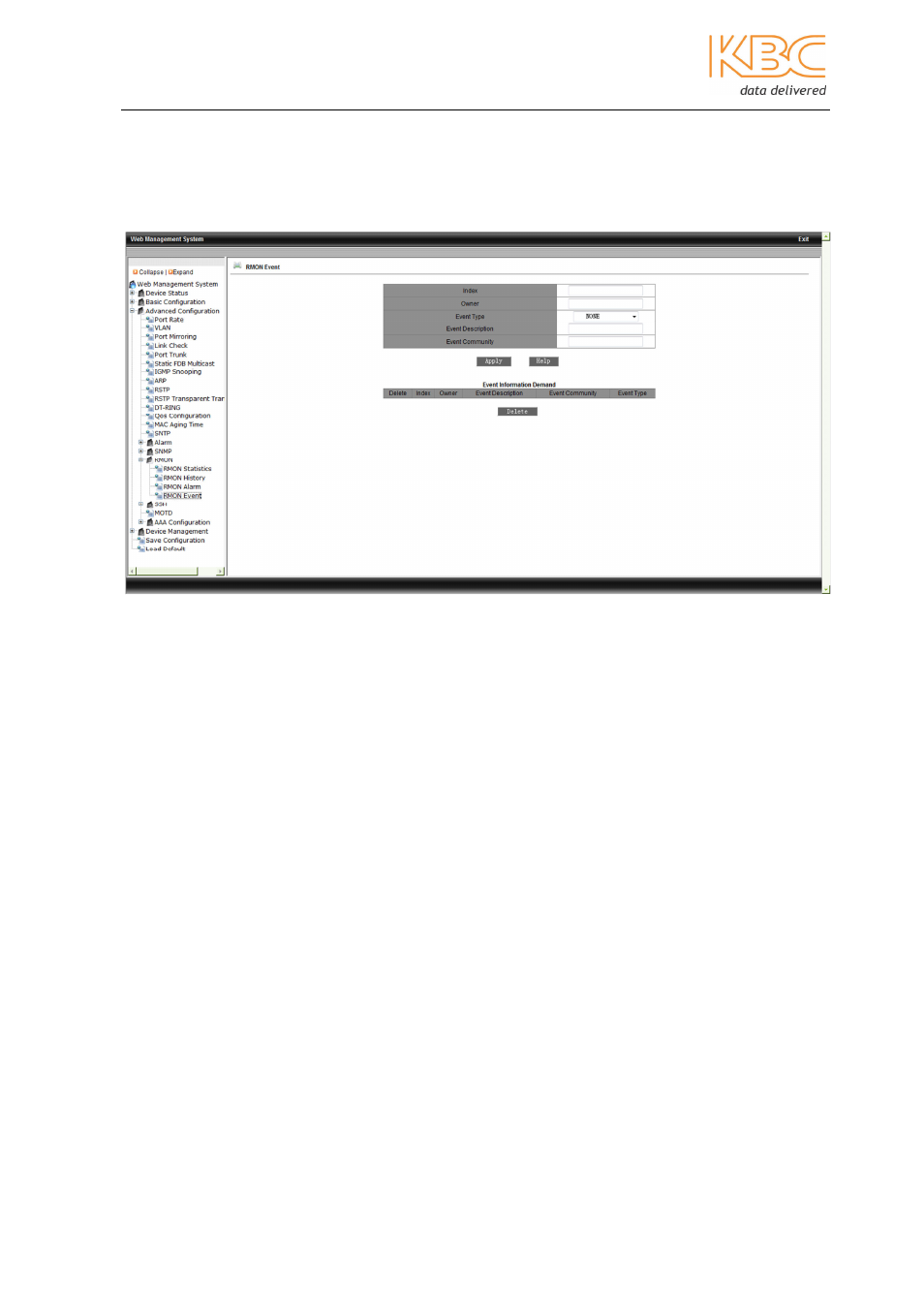
RMON Event
Fill in index no. (range: 1-65535), owner name (range: 1-32), event type (LOG/SNMP-
Trap/Log and Trap), event description (range: 1-127), event community (event trap
receiving community: 1-127). Select <Apply> to save any changes.
Fig 3-55 RMON Event
3.1.3.18
SSH
Secure Shell (SSH) is the standard remote login shell protocol used with TCP/IP where
both authentication and the session are encrypted. It is used to encrypt the transmission
data, stop data being intercepted during transmission, prevent DNS and IP spoofing and
improve the transmission rate as the data is compressed. SSH can replace Telnet and
can provide a secure channel for FTP, POP and PPP. SSH is made up of server and client
software.
Two methods of authentication are supported: password authentication and public key
authentication.
a.
SSH Server Configure
Enable the SSH state, set the authentication retry times to between 1 and 10 this is the
maximum retry times before the SSH server refuses to connect. The Time Out can be set
to between 60 and 300, this is how long the SSH Client will maintain a connection when
there is no data input. The Local Key Pair must be set to create or destroy, this has to be
set to create before the SSH server is enabled.