Configuring dhcpv6 snooping, Overview – H3C Technologies H3C S12500 Series Switches User Manual
Page 201
187
Configuring DHCPv6 snooping
A DHCPv6 snooping device does not work if it is between a DHCPv6 relay agent and a DHCPv6 server.
The DHCPv6 snooping device works when it is between a DHCPv6 client and a DHCPv6 relay agent or
between a DHCPv6 client and a DHCPv6 server.
You can configure only Layer 2 Ethernet interfaces or Layer 2 aggregate interfaces as DHCPv6 snooping
trusted ports. For more information about aggregate interfaces, see Layer 2—LAN Switching
Configuration Guide.
Overview
As a DHCPv6 security feature, DHCPv6 snooping can:
•
Ensure DHCPv6 clients to obtain IPv6 addresses from authorized DHCPv6 servers.
•
Record IP-to-MAC mappings of DHCPv6 clients.
Ensuring DHCPv6 clients to obtain IPv6 addresses from
authorized DHCPv6 servers
If there is an unauthorized DHCPv6 server on a network, DHCPv6 clients might obtain invalid IPv6
addresses and network configuration parameters, and cannot communicate with other network devices.
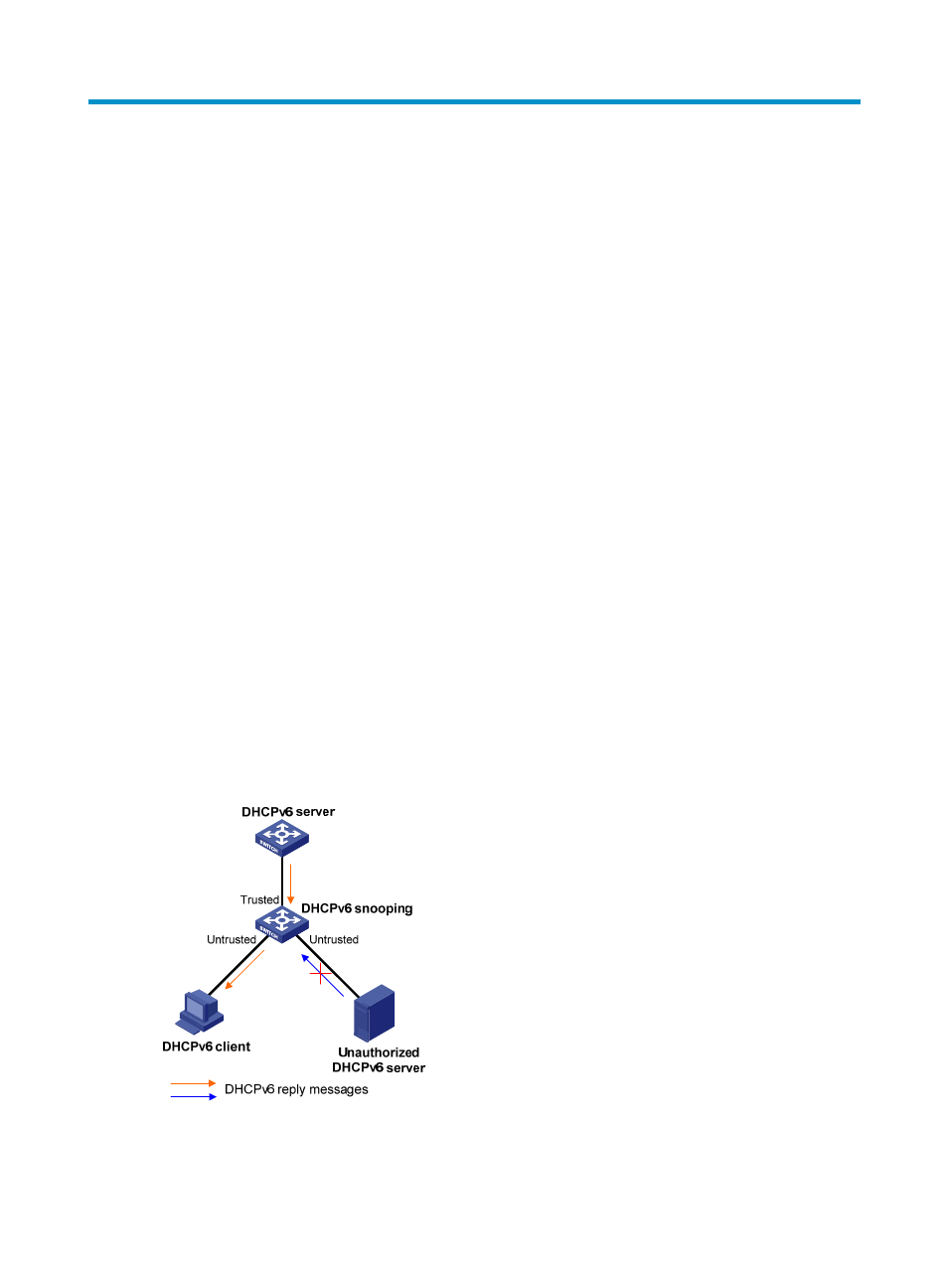
With DHCPv6 snooping, the ports of a switch can be configured as trusted or untrusted, ensuring the
clients to obtain IPv6 addresses from authorized DHCPv6 servers.
•
Trusted—A trusted port forwards DHCPv6 messages correctly.
•
Untrusted—An untrusted port discards the reply messages from any DHCPv6 server.
Figure 77 Trusted and untrusted ports
A DHCPv6 snooping device's port that is connected to an authorized DHCPv6 server, DHCPv6 relay
agent, or another DHCPv6 snooping device should be configured as a trusted port to forward reply