Security check flow chart, Security check for smart devices, Configuration procedure – H3C Technologies H3C Intelligent Management Center User Manual
Page 31
Advertising
15
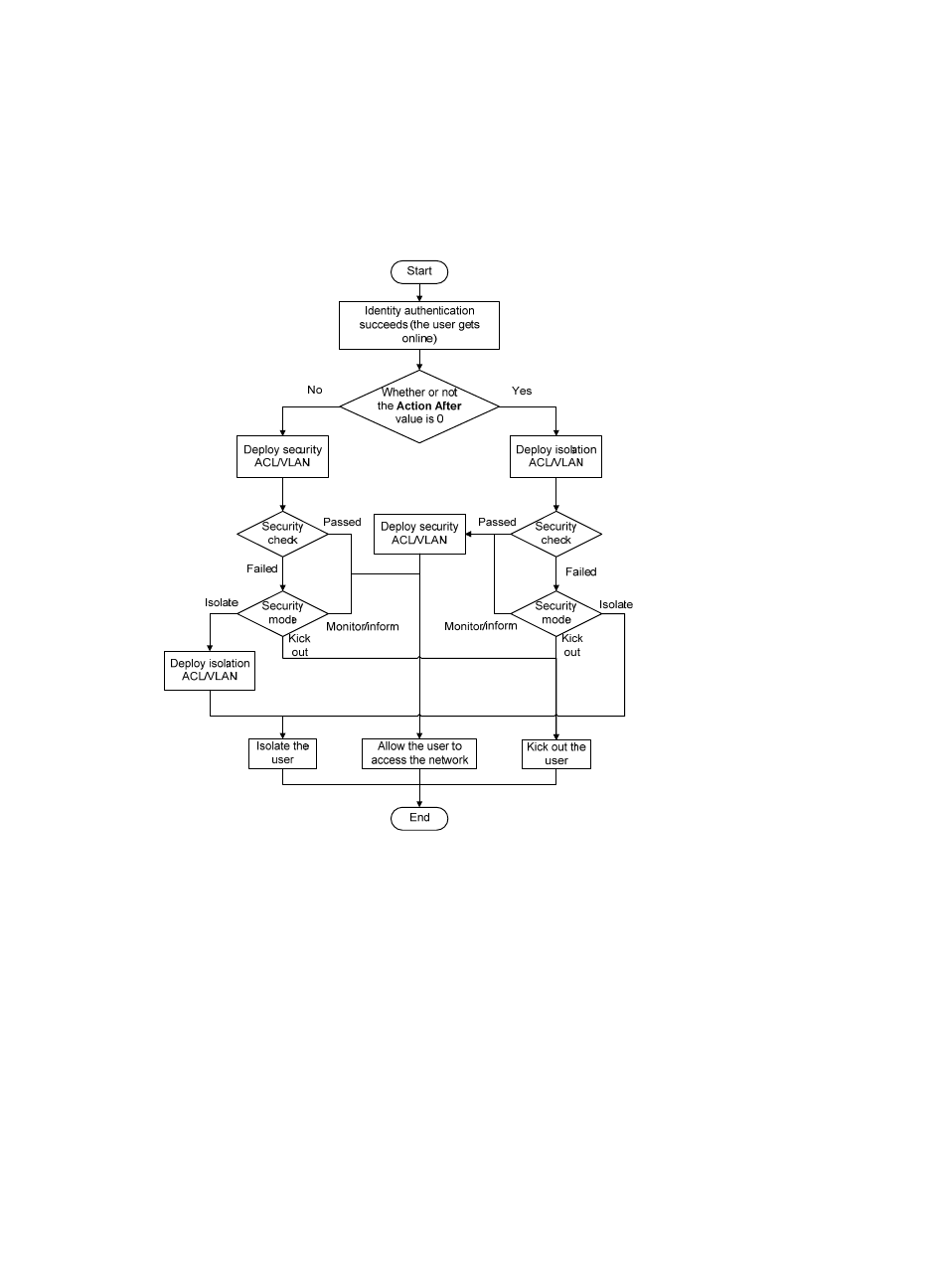
Security check flow chart
PC security check procedures depend on the security mode and isolation mode configured in the User
Security Policy module.
shows the process by which the EAD server performs a security check for
PCs.
Figure 6 PC security check procedures
Security check for smart devices
EAD can cooperate with a third-party MDM server and client to perform a security check on Android or
iOS smart devices.
Configuration procedure
To configure security checking for smart devices:
1.
Obtain the MDM vendor information and permissions to use the MDM API. EAD supports Citrix
and MobileIron.
2.
Configure the MDM vendor in the User Security Policy service parameter settings.
Advertising