H3C Technologies H3C SecPath F1000-E User Manual
Page 26
18
security zone, all TCP connection requests to the IP address will be processes by the TCP proxy
until the protected IP entry gets aged out. If you select this option, configure the TCP proxy
feature on the page you can enter after selecting Intrusion Detection > TCP Proxy.
2.
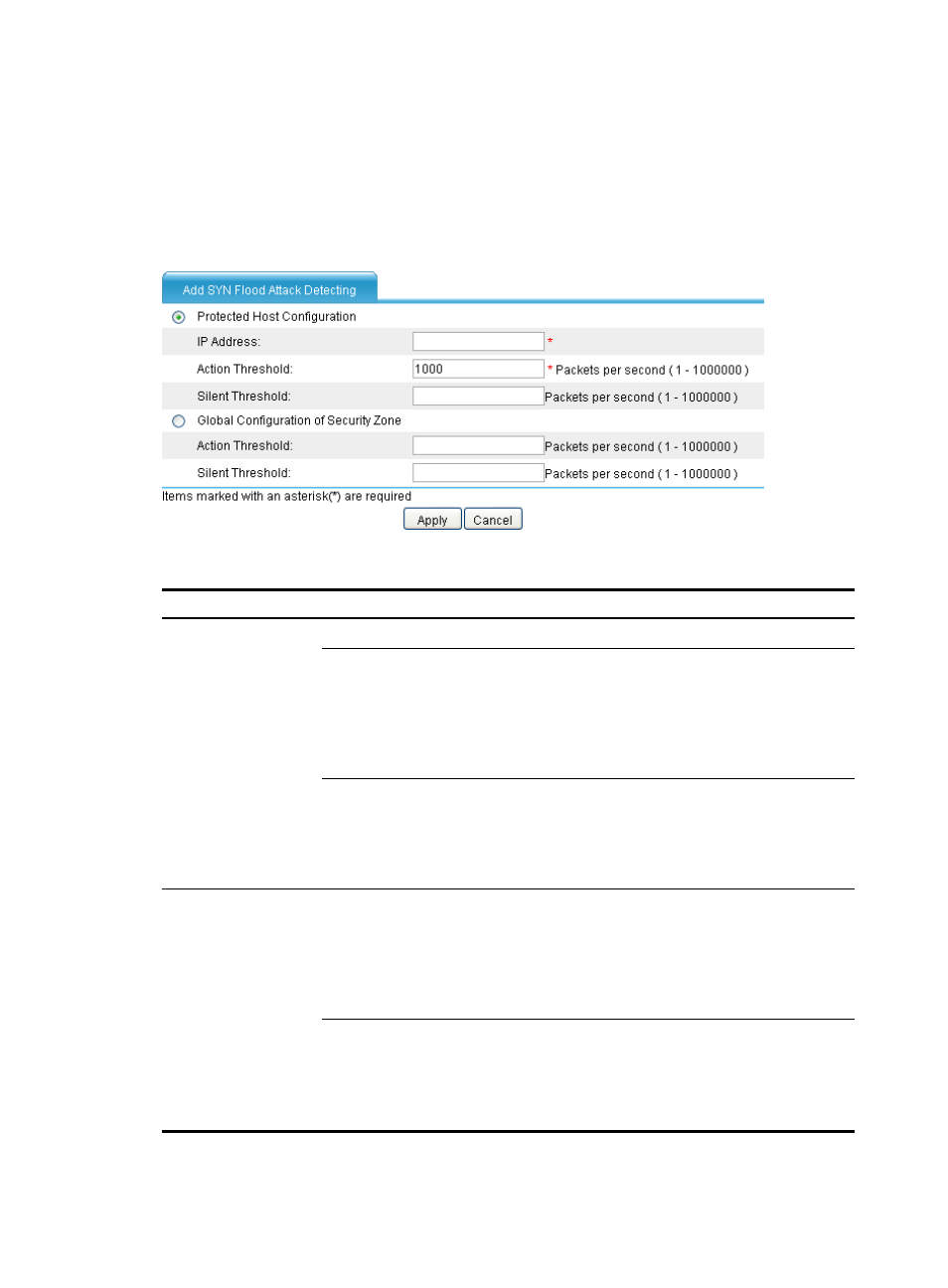
In the SYN Flood Configuration area, view the configured SYN flood detection rules, or click Add
to enter the page shown in
to configure a SYN flood detection rule.
describes
the configuration items.
Figure 18 Adding a SYN flood detection rule
Table 8 Configuration items
Item
Description
Protected Host
Configuration
IP Address
Specify the IP address of the protected host.
Action Threshold
Set the protection action threshold for SYN flood attacks that
target the protected host.
If the sending rate of SYN packets destined for the specified IP
address constantly reaches or exceeds this threshold, the
firewall enters the attack protection state and takes attack
protection actions as configured.
Silent Threshold
Set the silent threshold for actions that protect against SYN
flood attacks targeting the protected host.
If the sending rate of SYN packets destined for the specified IP
address drops below this threshold, the firewall returns to the
attack detection state and stops the protection actions.
Global Configuration
of Security Zone
Action Threshold
Set the protection action threshold for SYN flood attacks that
target a host in the protected security zone.
If the sending rate of SYN packets destined for a host in the
security zone constantly reaches or exceeds this threshold, the
firewall enters the attack protection state and takes attack
protection actions as configured.
Silent Threshold
Set the silent threshold for actions that protect against SYN
flood attacks targeting a host in the protected security zone.
If the sending rate of SYN packets destined for a host in the
security zone drops below this threshold, the firewall returns to
the attack detection state and stops the protection actions.
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS