Tcp proxy configuration example, Network requirements, Configuration procedure – H3C Technologies H3C SecPath F1000-E User Manual
Page 44
36
TCP proxy configuration example
Network requirements
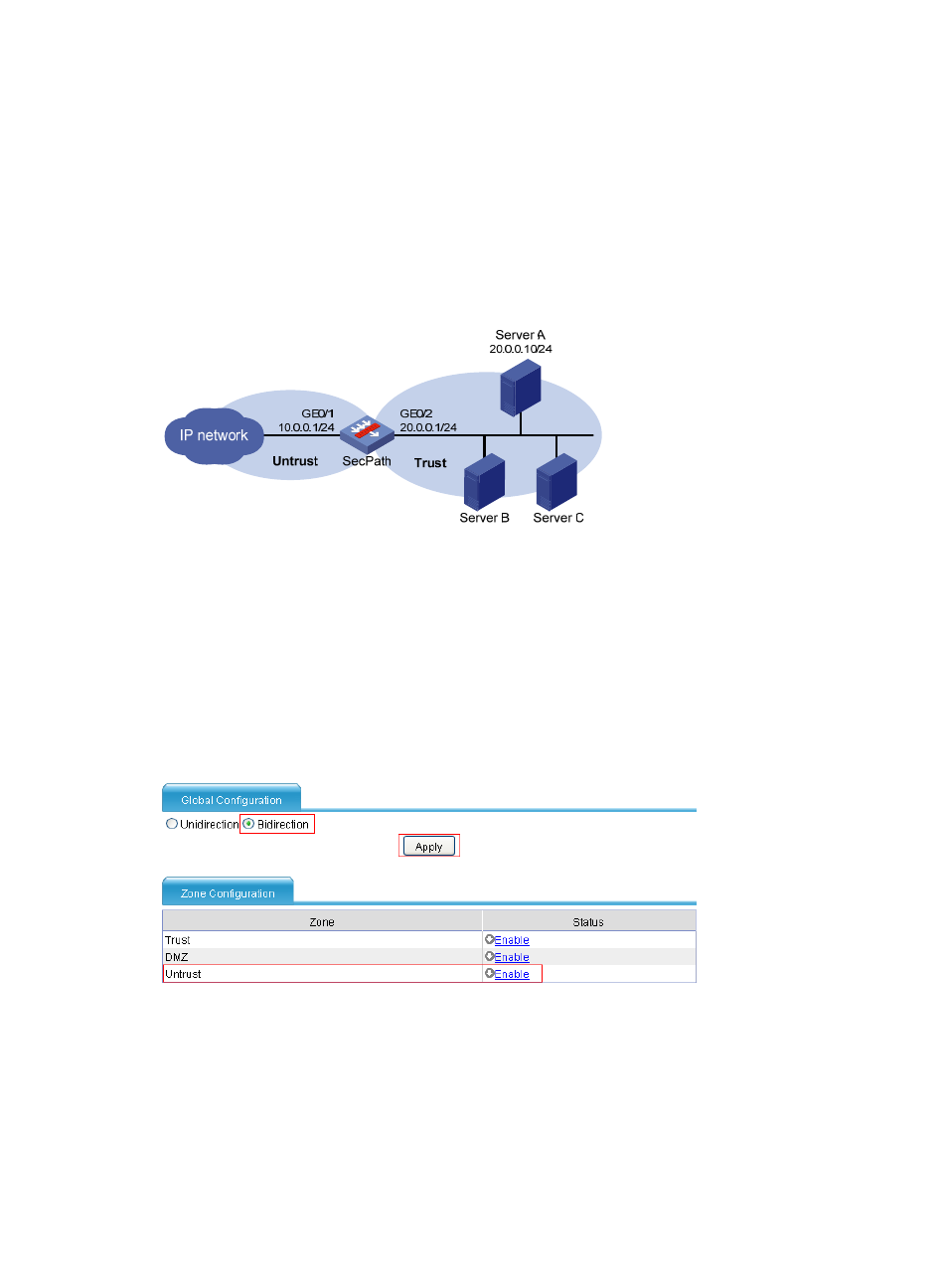
As shown in
, configure bidirectional TCP proxy on SecPath to protect Server A, Server B, and
Server C against SYN flood attacks. Add a protected IP address entry for Server A and configure
dynamic TCP proxy for the other servers.
Figure 42 Network diagram
Configuration procedure
# Assign IP addresses for the interfaces and then add interface GigabitEthernet 1/1 to zone Untrust, and
GigabitEthernet 1/2 to zone Trust. (Details not shown.)
# Set the TCP proxy mode to bidirectional and enable TCP proxy for zone Untrust.
•
Select Intrusion Detection > TCP Proxy > TCP Proxy Configuration from the navigation tree. Select
the bidirectional mode and enable TCP proxy for zone Untrust as shown in
.
Figure 43 Selecting the bidirectional mode and enabling TCP proxy for zone Untrust
•
Select Bidirection for the global setting.
•
Click Apply.
•
In the Zone Configuration area, click Enable for the Untrust zone.
# Add an IP address entry manually for protection.
•
Select Intrusion Detection > TCP Proxy > Protected IP Configuration from the navigation tree. Then
on the right pane, click Add. Add an IP address entry for protection as shown in
.
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS