A.4.3.6, A.4.3.7, A.4.3.8 – BECKHOFF IPC-Security User Manual
Page 54
Value
Description
0x1
Disables Autorun on drives of unknown type
0x4
Disables Autorun on removable devices
0x8
Disables Autorun on fixed drives
0x10
Disables Autorun on network drives
0x20
Disables Autorun on CD-ROM drives
0x40
Disables Autorun on RAM disks
0x80
See 0x1
0xFF
Disables Autorun on all kinds of drives
If you would like to configure a mix of the settings shown above, you only need to add the corresponding
hexadecimal values, for example 0x4 + 0x10 = 0x14.
A.4.3.6. Deactivating the webserver
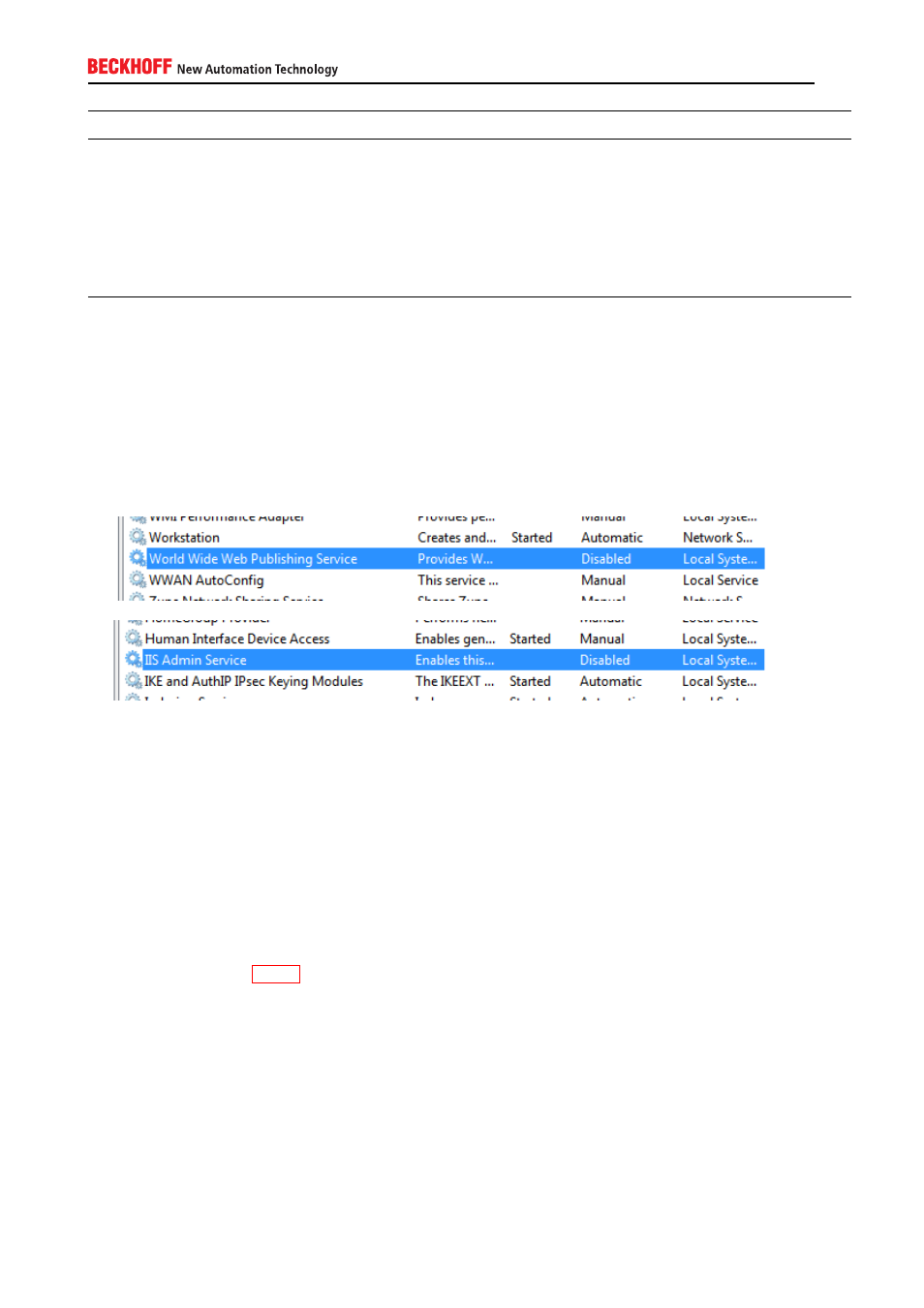
To deactivate the IIS Webserver, please open the Windows Service MMC, for example, by going to Start →
Run → services.msc and pressing Enter. Deactivate the World Wide Web Publishing Service and IIS Admin
Service.
Please keep in mind that all services that depend on the Webserver won’t work afterwards!
A.4.3.7. Deactivating the Windows registry
Blocking access to Windows Registry tools like regedit.exe or regedt32.exe can be achieved by adding the
DWORD value DisableRegistryTools to the following registry key:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\
Setting this value to 1 results in an error message as soon as one of the registry editors is started. Please
note that you could also block access to these tools by creating a corresponding Software Restriction Policy,
as described in chapter 3.2.3.5.
A.4.3.8. Deactivating the Windows command prompt
To block access to the Windows command line, just add the DWORD value DisableCMD to the following
registry key:
HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\System\
54