Advanced tab – equinux VPN Tracker 8.1.1 User Manual
Page 50
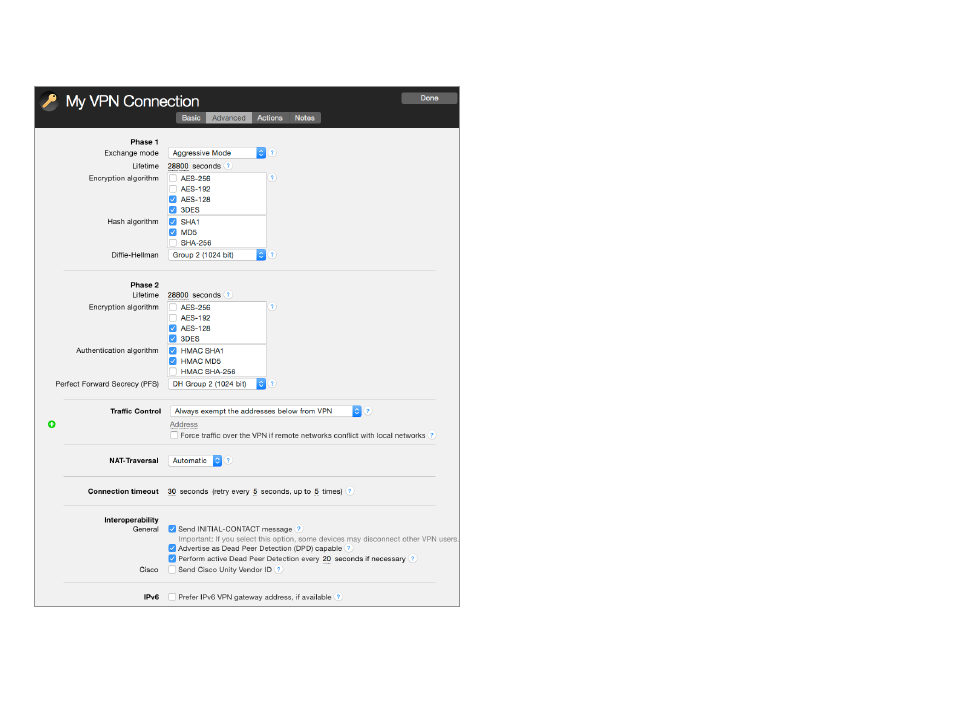
Advanced Tab
Establishing the VPN: Phases, Proposals and Device Profiles
An IPsec VPN connection is established in two phases. In phase 1, VPN Tracker
and the VPN gateway verify each other’s identity and negotiate encryption
keys through which the actual setup of the VPN, phase 2, will be secured.
‣ In each phase, VPN Tracker sends the algorithms it is willing to use, as well
as a few other settings to the VPN gateway (the “proposals”). The algorithms
that VPN Tracker sends are determined by the settings for Phase 1 and 2 on
the Advanced tab.
‣ The VPN gateway then selects one set of algorithms, or responds with an
error (typically something like “no proposal chosen”) if it does not agree to
use any of the proposed algorithms.
At first glance, it would seem a good idea to simply propose all possible algo-
rithms to the VPN gateway, hoping that it will agree with at least one pro-
posal. However, there are several problems with this approach:
‣ Selecting too many algorithms causes data packets on the network to be
so large they need to be split up ("fragmented"). Many VPN gateways out-
right refuse these fragmented VPN packets, and intermediate routers often
have difficulties with fragmented VPN data packets as well.
‣ Some VPN gateways refuse connection attempts altogether that contain
many proposals or algorithms unsupported by the VPN gateway, most
likely to serve as an intrusion prevention measure.
‣ It is desirable to offer only those algorithms providing a very high level of
security.
In the device profiles shipping with VPN Tracker, two or three algorithms that
are most commonly used with a given device have been selected.
This increases the chance of a successful connection, even if the exact con-
figuration is not known (while still keeping the data packets small enough to
not be fragmented). However, if you know your VPN gateway’s exact configu-
ration, it is best to select exactly one proposal (combination of encryption,
authentication/hash algorithm, and DH group) that your VPN gateway is set
up to use.
50