Aaa across vpns – H3C Technologies H3C SecPath F1000-E User Manual
Page 168
158
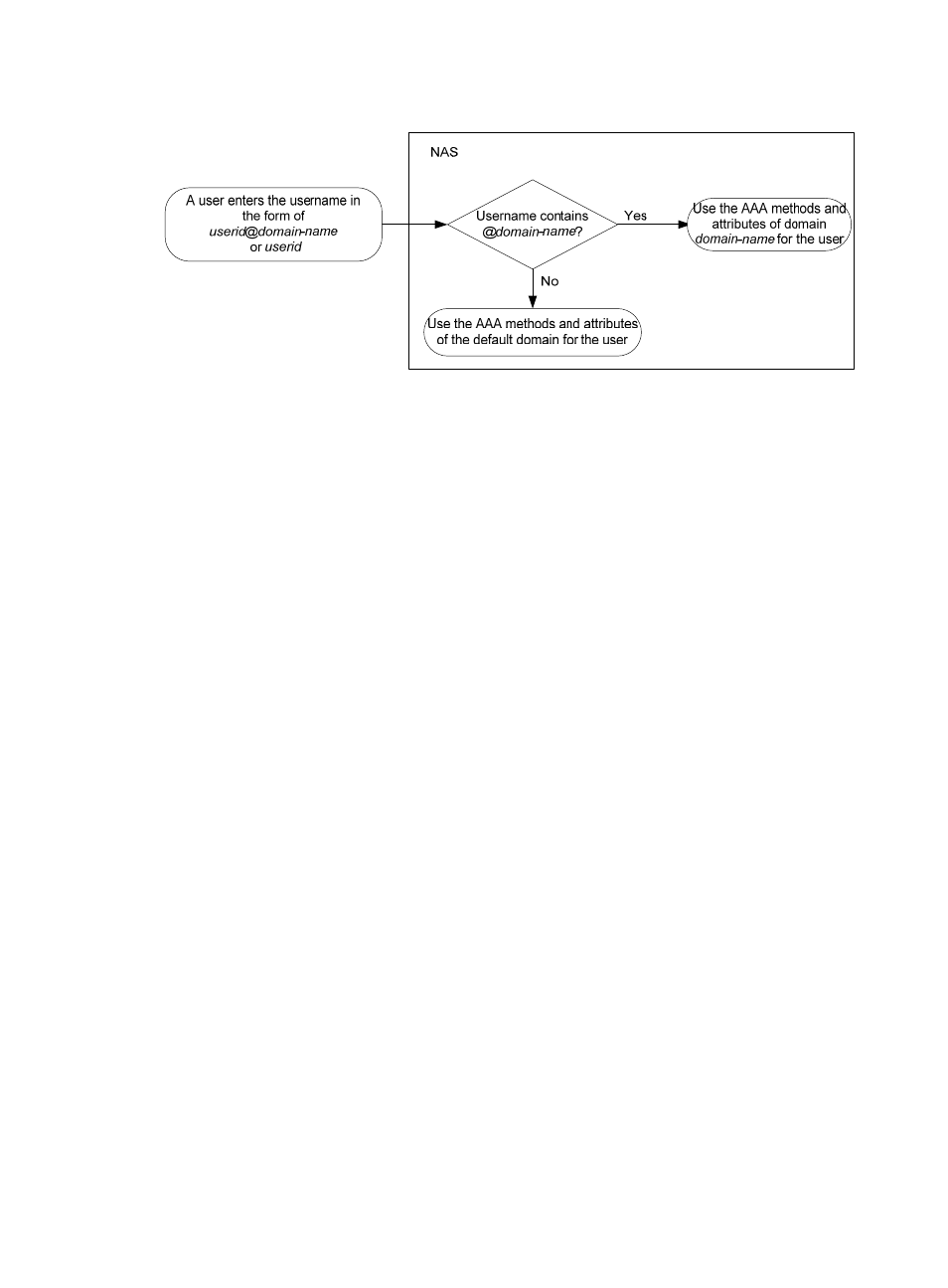
Figure 135 Determining the ISP domain of a user by the username
The authentication, authorization, and accounting process of a user depends on the AAA methods
configured for the domain to which the user belongs. If no specific AAA methods are configured for the
domain, the default methods are used. By default, a domain uses local authentication, local
authorization, and local accounting.
AAA allows you to manage users based on their access types:
•
Login users—Users who want to log in to the NAS, including SSH users, Telnet users, Web users,
FTP users, and terminal users.
•
DVPN users.
•
Portal users—Users who must pass portal authentication to access the network.
•
PPP users—Users who access through PPP.
•
SSL VPN users—Users who access through SSL VPN.
In addition, AAA provides the following services for login users to enhance device security:
•
Command authorization—Enables the NAS to defer to the authorization server to determine
whether a command entered by a login user is permitted for the user, making sure that login users
execute only commands they are authorized to execute. For more information about command
authorization, see Getting Started Guide.
•
Command accounting—Allows the accounting server to record all commands executed on the NAS
or all authorized commands successfully executed. For more information about command
accounting, see Getting Started Guide.
•
Level switching authentication—Allows the authentication server to authenticate users who perform
privilege level switching. As long as passing level switching authentication, users can switch their
user privilege levels, without logging out and disconnecting current connections. For more
information about user privilege level switching, see Getting Started Guide.
You can configure different authentication, authorization, and accounting methods for different users in
a domain. See "
Configuring AAA methods for ISP domains
AAA across VPNs
In a VPN scenario where clients in different VPNs are centrally authenticated, you can deploy AAA
across VPNs to enable forwarding of RADIUS and HWTACACS packets across VPNs. As shown
in
, the PE at the left side of the MPLS backbone serves as a NAS and transparently delivers
the AAA packets of private users in VPN 1 and VPN 2 to the AAA servers in VPN 3 for centralized
authentication. Authentication packets of private users in different VPNs do not affect each other.
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS