Mpls log auditing, Configuration guide, Security policy management – H3C Technologies H3C SecCenter Firewall Manager User Manual
Page 65: Figure 58
59
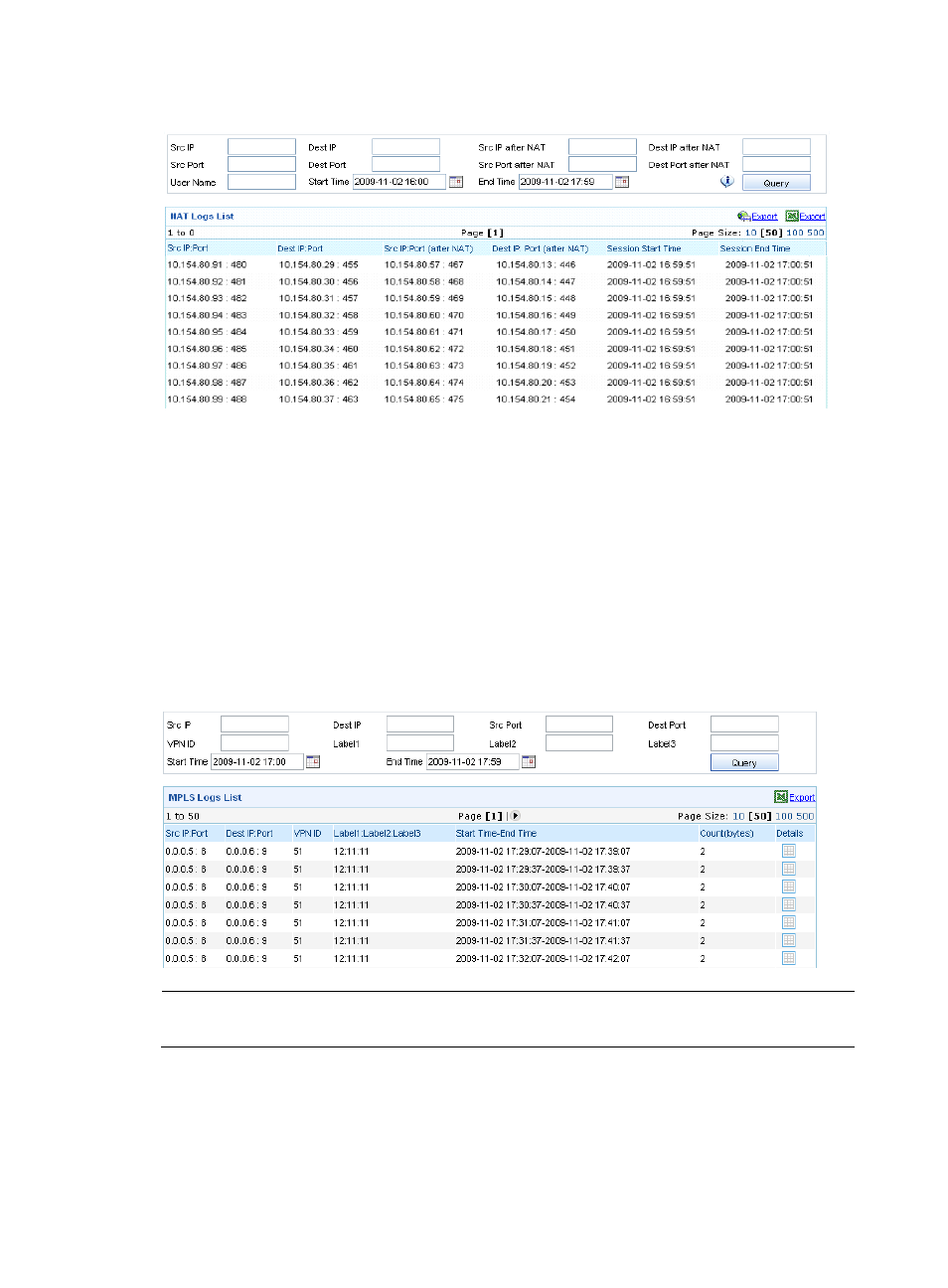
Figure 58 NAT log auditing
MPLS log auditing
Configuration guide
From the navigation tree of the firewall management component, select MPLS Logs under Event Auditing
to enter the MPLS log auditing page, as shown in
. This page lists MPLS logs in detail. Each log
records such information as source IP address and source port, destination IP address and port, VPN ID,
time, and byte count.
MPLS log auditing allows you to query MPLS logs by source IP, destination IP, source port, destination
port, VPN ID, labels, start time, and end time, helping you know the information of MPLS logs.
Figure 59 MPLS log auditing
NOTE:
If the IP address/port number is null in the database, NA will be displayed in the IP address or port field.
Security policy management
The security policy management function allows you to configure security policies for firewall devices and
deploy them to multiple devices and virtual devices for security policy consistency. This function allows