Configuring isolate-user-vlans, Configuration restrictions and guidelines – H3C Technologies H3C WX5500E Series Access Controllers User Manual
Page 149
138
Configuring isolate-user-VLANs
An isolate-user-VLAN uses a two-tier VLAN structure. In this approach, both an isolate-user-VLAN and
secondary VLANs are configured on the same device.
The isolate-user-VLAN implementation delivers the following benefits:
•
Isolate-user-VLANs are mainly used for upstream data exchange. An isolate-user-VLAN can be
associated with multiple secondary VLANs. Because the upstream device identifies only the
isolate-user-VLAN and not the secondary VLANs, network configuration is simplified and VLAN
resources are saved.
•
You can isolate Layer 2 traffic from different users by assigning ports connected to them to different
secondary VLANs. To enable communication between secondary VLANs associated with the same
isolate-user-VLAN, you can enable local proxy ARP on the upstream device (such as Device A
in
) to realize Layer 3 communication between the secondary VLANs.
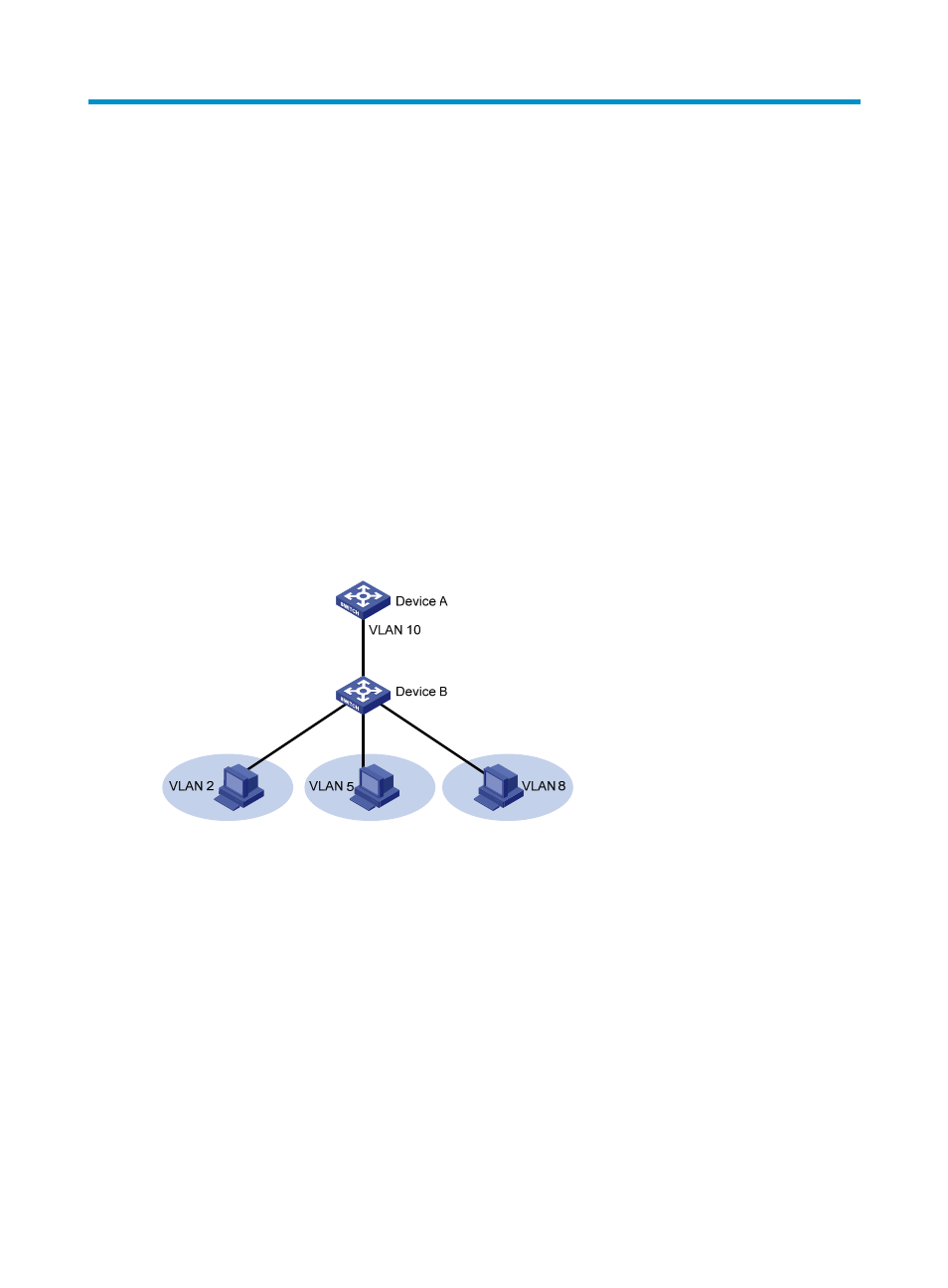
, the isolate-user-VLAN function is enabled on Device B. VLAN 10 is the
isolate-user-VLAN. VLAN 2, VLAN 5, and VLAN 8 are secondary VLANs associated with VLAN 10 and
are invisible to Device A.
Figure 41 An isolate-user-VLAN example
Configuration restrictions and guidelines
When you configure an isolate-user-VLAN, follow these guidelines:
•
To enable users in the isolate-user-VLAN to communicate with other networks at Layer 3, configure
VLAN interfaces for the isolate-user-VLAN and the secondary VLANs, and configure the gateway IP
address for the isolate-user-VLAN interface (you do not need to configure IP addresses for the
secondary VLAN interfaces).
•
You cannot configure the member port of a service loopback group as the uplink or downlink port
of an isolate-user-VLAN. For more information about the service loopback group, see "Configuring
•
The port isolate-user-vlan vlan-list trunk promiscuous command and the port isolate-user-vlan
vlan-id promiscuous command are mutually exclusive. The two commands are different as follows:
{
The former configures a port to permit packets from multiple isolate-user-VLANs to pass through.