PLANET WNAP-6308 User Manual
Page 67
User Manual of WNAP-6308
-57-
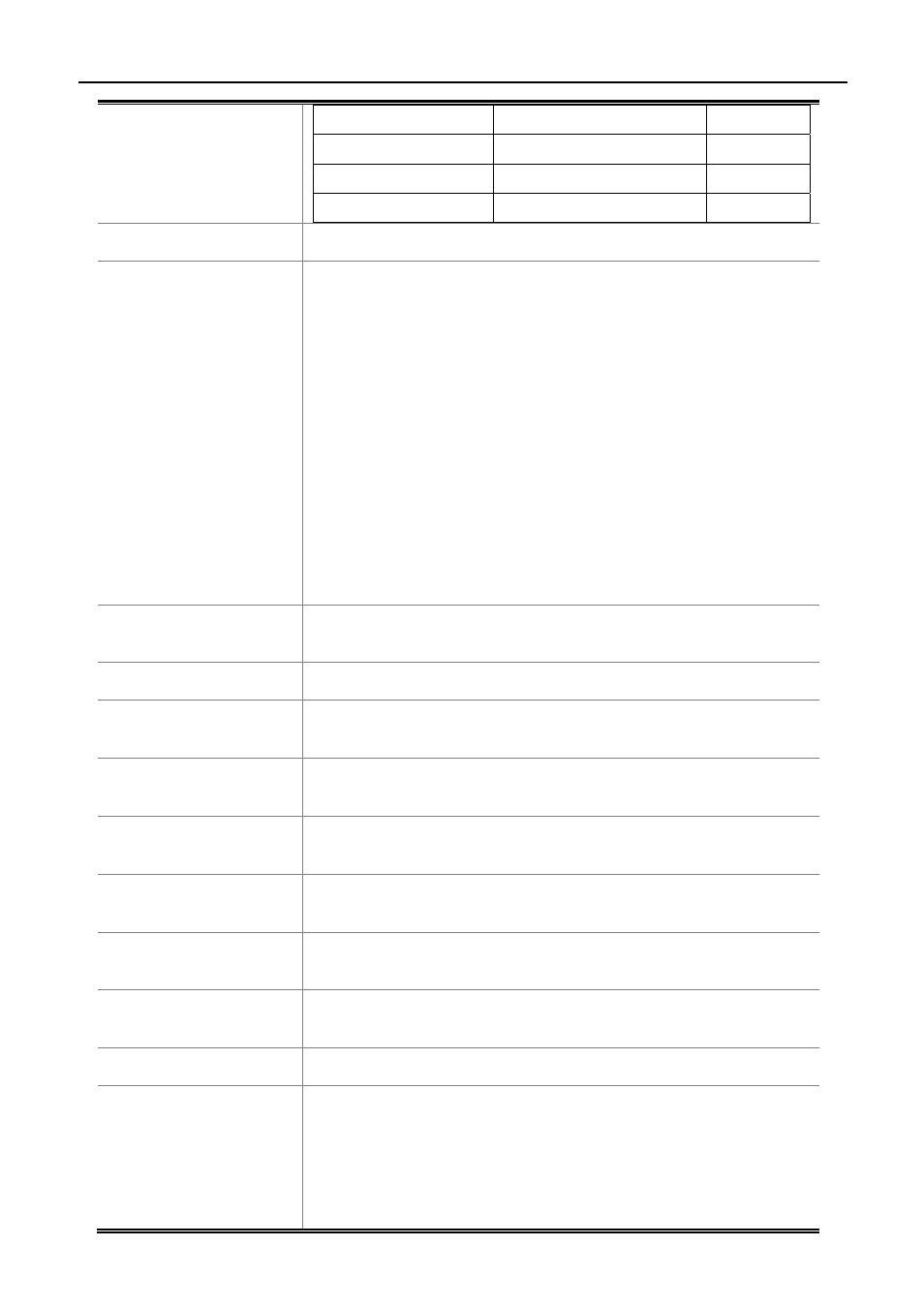
Group 2
1024 bits MODP group
Group 3
EC2N group on GP(2^155)
Group 4
EC2N group on GP(2^185)
Group 5
1536 bits MODP group
IPSec Authentication
The AP supports SHA1 & MD5 authentication algorithms.
IPSec Encryption
The AP supports DES, 3DES, AES, Blowfish, Twofish, Camellia
Encryption methods.
DES - 56-bit DES-CBC encryption algorithm
3DES - 168-bit DES encryption algorithm
AES - 128, 192 and 256-bit key AES-CBC encryption algorithm
Blowfish - a symmetric block cipher that can be used as a drop-in
replacement for DES or IDEA. It takes a variable-length key, from 32 bits
to 448 bits.
Twofish - Twofish has a 128-bit block size, a key size ranging from 128 to
256 bits, and is optimized for 32-bit CPUs.
Camellia - 128, 192 and 256-bit key Camellia encryption algorithm
SA connection Life
Time
This value describes the timeframe in hours for which the IKE SA is valid
and when the next rekeying should take place.
IKE Key Tries
The field is used to specify the retry times of IKE Key.
Local IP Address
This field is used to configure the IP address of the Untangle server on
the network configured in the Local Network field.
Peer IP Address
This field should contain the public IP address of the host to which the
IPSec VPN will be connected.
Local Subnet
This field is used to configure the local network that will be reachable
from hosts on the other side of the IPSec VPN.
Peer Subnet
This field is used to configure the remote network that will be reachable
from hosts on the local side of the IPSec VPN.
Local Gateway
This field is used to configure the Gateway of the Untangle server on the
network configured in the Local Network field.
Peer Gateway
This field should contain the public Gateway of the host to which the
IPSec VPN will be connected.
IPSec Tunnel Name
This field should contain a short name or description.
IPSec Secret Key
This field should contain the shared secret or PSK (pre-shared key) that
is used to authenticate the connection, and must be the same on both
sides of the tunnel for the connection to be successful. Because the PSK
is actually used as the encryption key for the session, using long strings
of a random nature will provide the highest level of security.