U s e r, D e m o – Datatek DT-4180 User Manual
Page 75
9 4 8 0 , 4 1 8 0 , 4 2 8 0 , 4 2 8 4 4 0 0 0 X A U s e r
M a n u a l
04/09/09
75
1 2 C L O S E D
U S E R
G R O U P
D E M O
The xxxx supports the notion of Closed User Groups (CUGs) for IP networking
applications. A CUG applies to sessions being established to endpoints on the xxxx.
This is an important feature for protecting sensitive endpoints in a corporate-wide
network without the burden of special “security servers”.
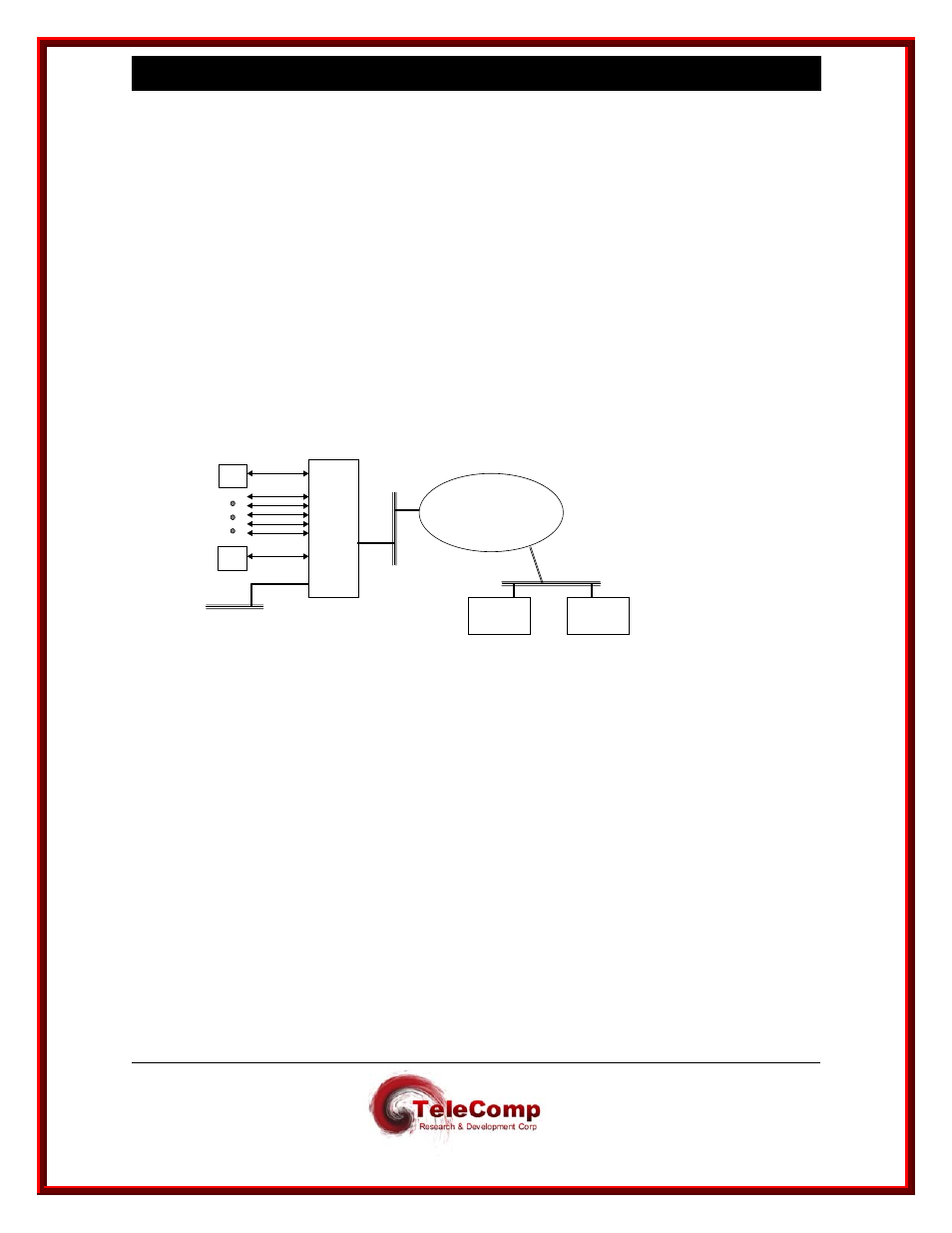
The following diagram depicts a corporate IP network infrastructure which may be
accessed by endpoints throughout the network. Some endpoints require access to the
Network Elements (NEs) reachable via IP-type ports on the xxxx, and some endpoints
are not to be allowed such access. IP network endpoints, which are allowed to access
the NEs, are placed in a CUG to be associated with the appropriate user ports. (The
same CUG may be associated with any number of user ports. Any one-user port may
belong to up to 16 CUGs.)
NE
NE
4180
10BaseT
Corporate IP Network
10BaseT
IP-GATE
RS232
Endpoint “A”
Endpoint “B”
Referring to the previous diagram, Endpoint A must be allowed access to all the NEs,
but Endpoint B is not allowed such access. The xxxx is configured with CUG 1 with the
address of Endpoint A, as follows:
cug 1 ipaddr=135.17.59.5 submask=255.255.255.255
Each protected user port (i.e., those connected to the NEs) is set up with CUG 1
assigned to it, as follows:
port 1 type=rcv hport=26 cug=+1
When Endpoint A calls the xxxx and TCP port number 26, access to the NE connected
to port 1 on the xxxx is granted, and everything proceeds transparently. If an endpoint
outside CUG 1 (e.g., Endpoint B) attempts to call the same TCP port, however, the
following happens:
1. The call is terminated during authentication without any data being transported in
either direction.
2. An
authentication alarm is generated and sent to an attached Starkeeper, an
attached Telnet Console (if any) and the SNMP Trap Manager (if any). The Alarm
contains the IP address of the remote endpoint that attempted the unauthorized
access.