Verilink Red Zone Encryption (REMS) (880-502423-001) Product Manual User Manual
Page 37
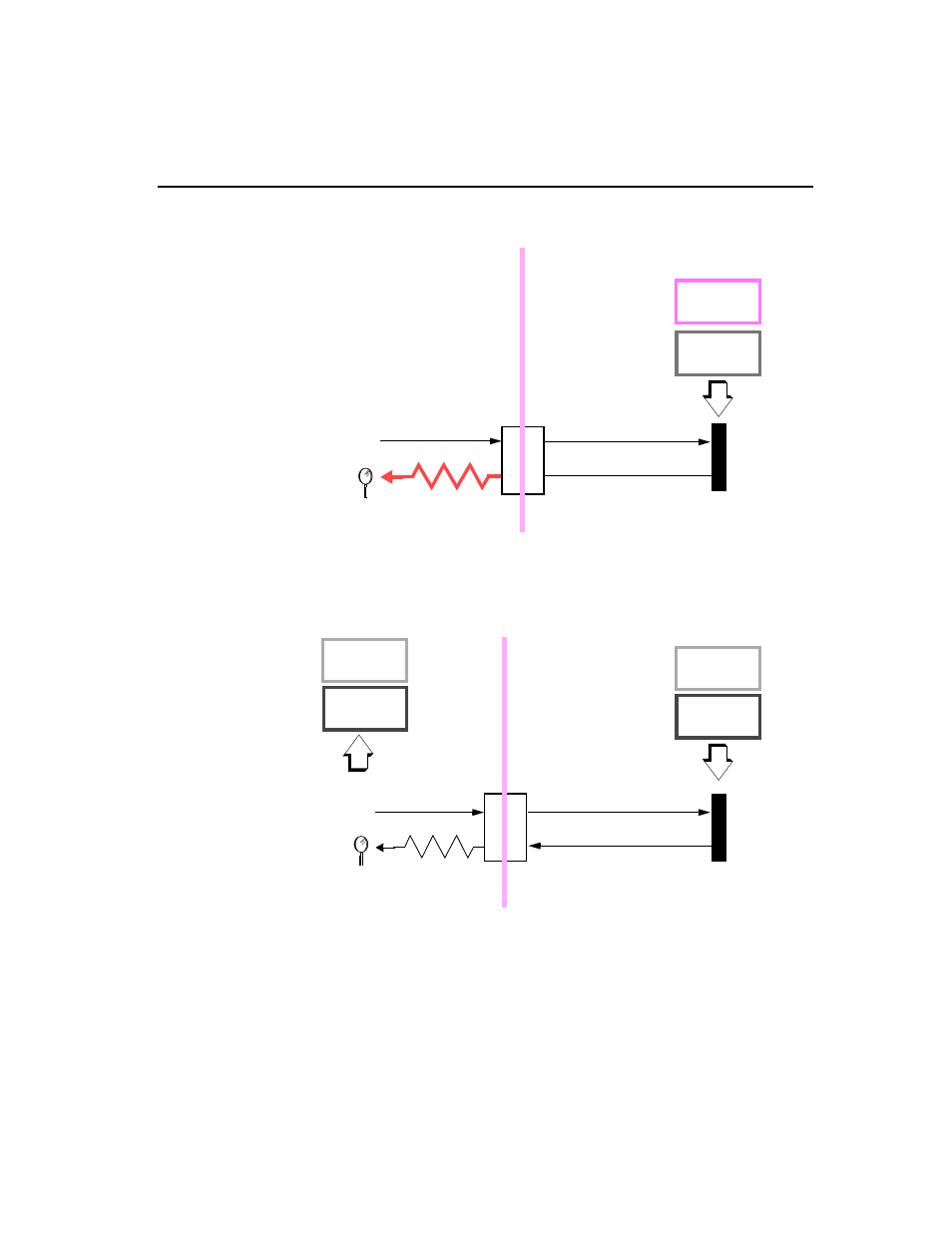
How performance data is distributed
Red Zone Encryption Management System (REMS) User Manual
3-11
Figure 3-5
The FBR receives the information
At the encryptor, the FBR code containing the BRC performance message is
decrypted. The FBR does know what FBR code it was expecting from the other end
and can compare the received code with the expected code.
Figure 3-6
The FBR decodes information and rebuilds registers
Using an algorithm, the FBR extracts the BRC performance message from the
received code. It then uses these extracted BRC performance messages to
reconstruct the Black Zone performance registers.
Red Zone
B
R
C
F
B
R
Black Zone
Near-End
Near-End
Performance
Registers
Far End
Performance
Registers
Decrypted FBR code
(with BRC performance
Encryptor
message
KG81
KG94
Red Zone
B
R
C
Black Zone
Near-End
Near-End
Performance
Registers
Far End
Performance
Registers
Near-End
Performance
Registers
Far End
Performance
Register
F
B
R
KG81
Encryptor
KG94