Airlink RTW026 User Manual
Page 41
Chapter 4: Web Configuration
31
C
C
o
o
n
n
f
f
i
i
g
g
u
u
r
r
e
e
W
W
E
E
P
P
192.168.1.10
∗∗∗
802.1x: IEEE
802.1x is a port based authentication protocol. It can be used in *any* scenario
where one can abstract out the notion of a port. It requires entitie(s) to play three roles in
the authentication process: that of an supplicant, an authenticator and an authentication
server. The diagram below shows the basic scenario.
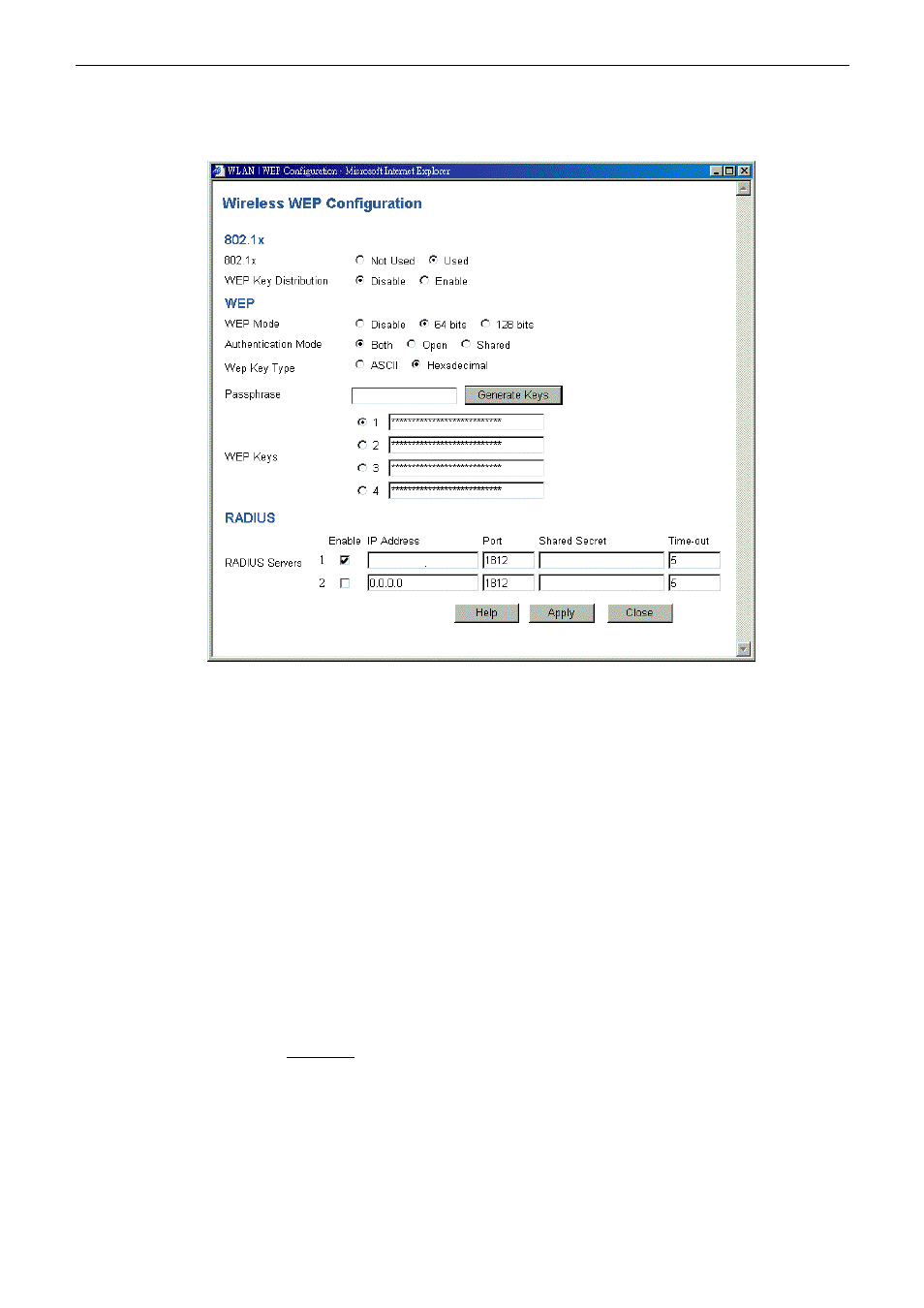
Choose Used to indicate that the system will use this function.
Choose Not Used if this function has not been opened.
WEP Key Distribution: Choose Enable to activate the WEP key’s function.
WEP Mode:
Disable
If choose Disable, data is NOT encrypted before being transmitted.
64 Bit Encryption
If selected, data is encrypted, using the default key, before being transmitted. The
receiving station must be set to use 64 Bit Encryption, and have the same Key value in
the same position in its key table. Otherwise, it will not be able to decrypt the data.
Default key – select the key you wish to be the default.
Transmitted data is ALWAYS encrypted using the Default Key; the other keys are for
decryption only.
Key Table:
This table is used when Encrypting and Decrypting data. All stations, including this
Access Point, always transmit data encrypted using their default key. The key number
(1,2,3,4) is also transmitted. The receiving station will use the key number (1,2,3,4) to
determine which key value to use for decryption. If the key value does not match the
transmitting station, decryption will fail.
The easiest way to ensure there are no problems is to have every Station, including the
Access Point, use the same key table (all entries identical)