Network configuration, 22 ultralink 2 installation and operations manual – Rose Electronics UltraLink 2 User Manual
Page 26
22
UltraLink 2 Installation and Operations Manual
Use the arrow keys to set the time (24 hour base) and date. If you wish to use NTP
(Network Time Protocol) to set the time, check the box next to Use NTP, enter the NTP
Server IP address, and then click on Set Time from NTP Server.
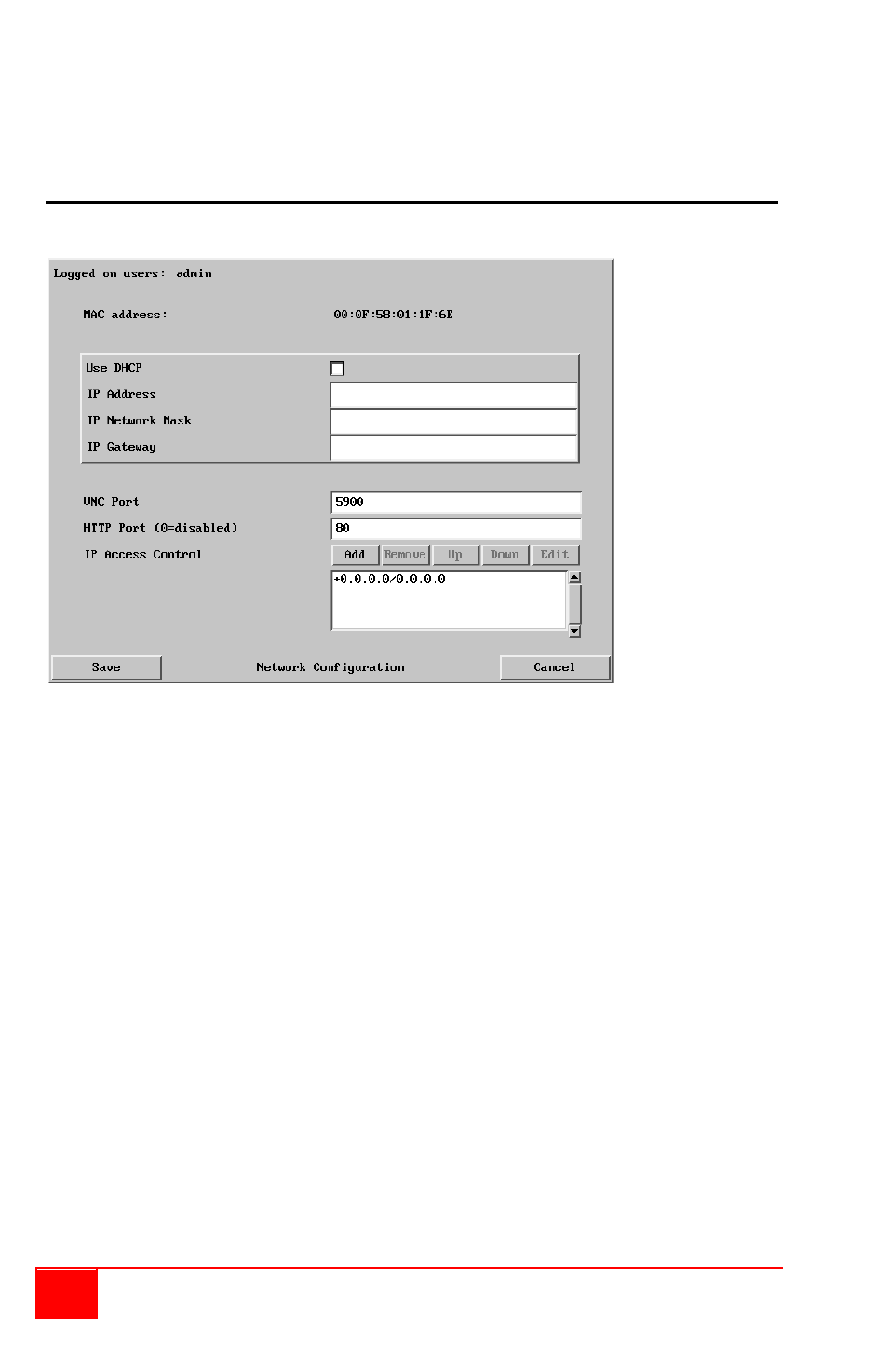
Network Configuration
Click on the “Network Configuration” tab brings up the below configuration menu.
Figure 12. Remote Network Configuration
The UltraLink 2 is designed to use either a static IP address or an IP address that is
assigned by your DHCP server. If you choose to use the DHCP feature, check the box
adjacent to “Use DHCP”.
NOTE: If you choose the option “Use DHCP” the IP address will change to whatever IP
address your DHCP server assigns it. Once the IP address is changed the connection to
UltraLink 2 will be lost. Also, if it is changed by the DHCP server the user must determine
the new IP address in order to connect to the computer to access.
If you choose to use a static IP address, change the IP address, IP network mask, and IP
Gateway as needed to be compatible with your network. The UNC port (5900) and HTTP
Port (80) should only be changed if they conflict with existing network settings or
equipment. .
The IP Access Control feature allows you to specify a range of IP address that will or will
not be granted access to the UltraLink 2 unit. This additional feature adds to the security of
the UltraLink 2. The default IP access control is +0.0.0.0/0.0.0.0 which grants all IP
addresses access to the UltraLink 2. Click on the “Add” tab to add an IP range to grant or
deny access.
NOTE: The IP Access Control list should have all granted access IP addresses added first
and all denied access IP address added last. This is because of the position of the entries
in the list. Once a range of addresses is denied access, it is not possible to grant access to
a particular address within the denied range down the list. Below is an example of the
correct and incorrect way to control access.