Features, Roaming authentication, Application scenarios – H3C Technologies H3C Intelligent Management Center User Manual
Page 28
10
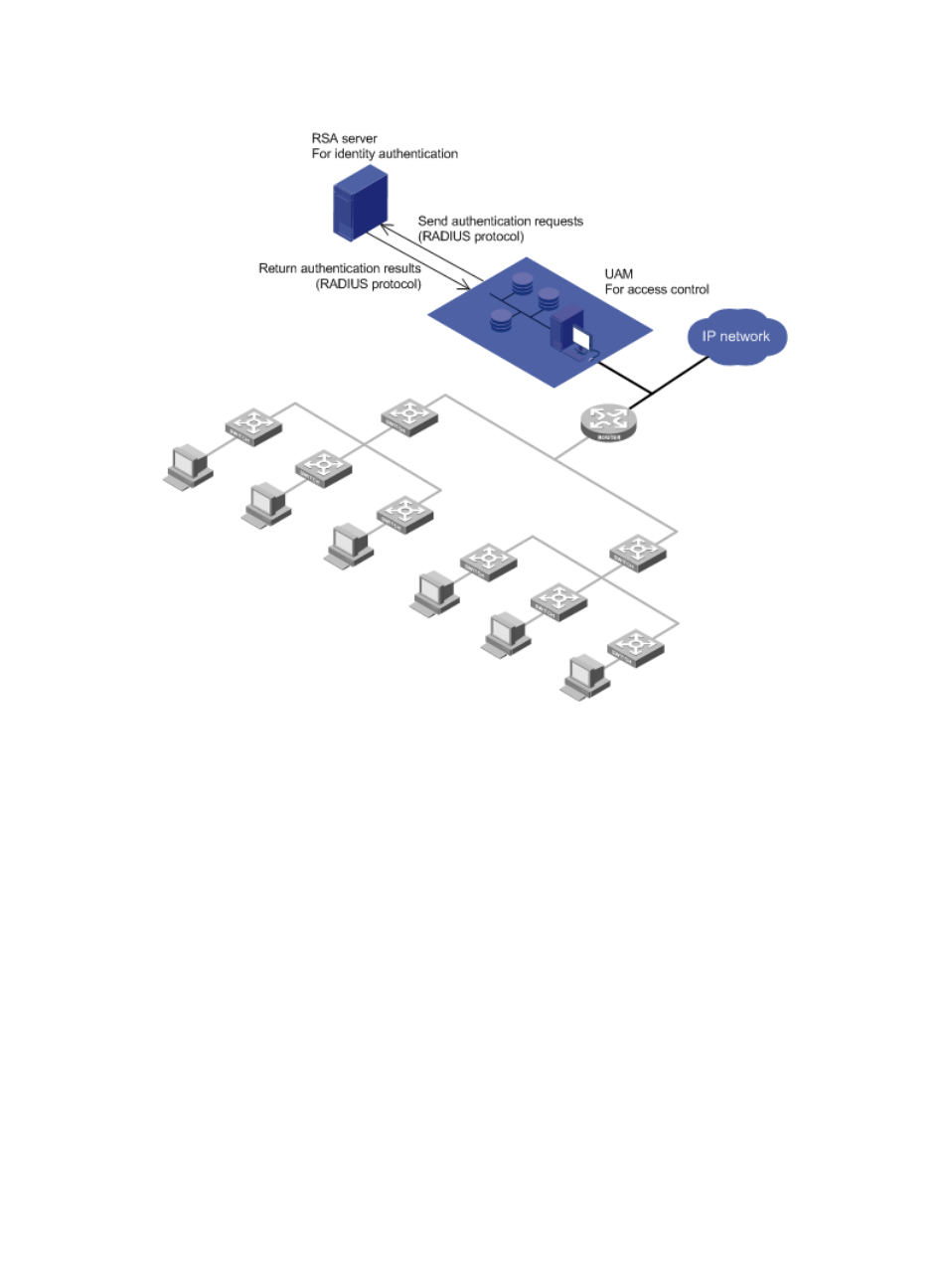
Figure 7 Network diagram of RSA authentication
Features
RSA authentication has the following features:
•
After UAM receives an authentication request from an endpoint user, UAM uses the RADIUS
protocol to forward the request to the RSA server. The RSA server authenticates the user identity.
•
After the user passes identify authentication, UAM checks the binding information. If the user passes
the check, UAM tells the access device to permit network access, and assigns access control
policies to the access device. The access device then controls user access to the network according
to the policies.
Roaming authentication
Application scenarios
Roaming authentication, as shown in
, is typically used in a large-scale network that has
deployed multiple UAM servers. Each server performs access control in an area, and a user needs to
access the network in different areas.