Example, Uam and access device cooperation – H3C Technologies H3C Intelligent Management Center User Manual
Page 29
11
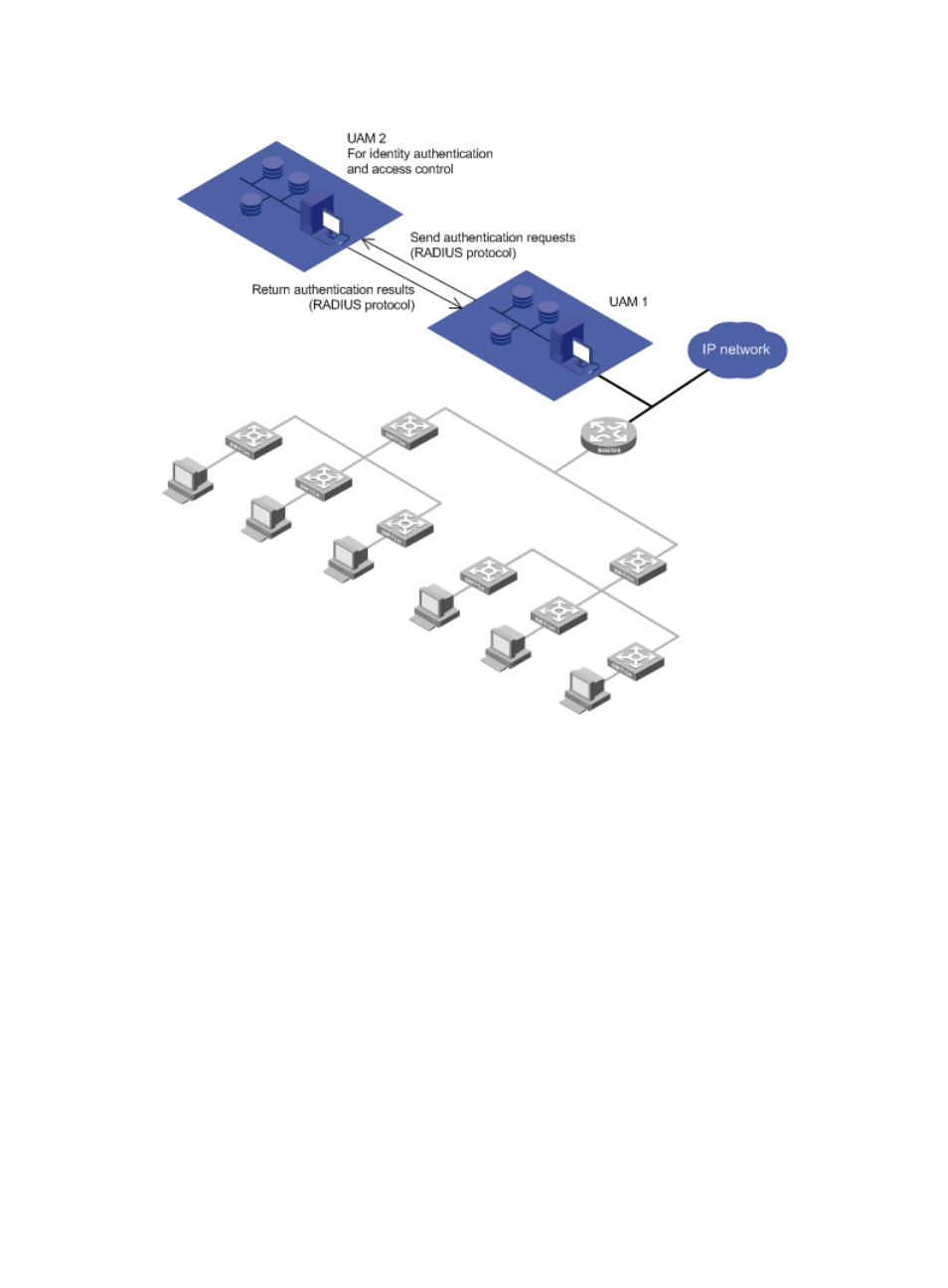
Figure 8 Network diagram of roaming authentication
Example
In a roaming authentication scenario:
•
Each endpoint user has a local UAM server, which is the server that saves the user's information.
•
Each endpoint user also has a roaming UAM server, which is the server through which the user is
connected to the network.
Assume that UAM 2 is the local UAM server of a user, and UAM 1 is the roaming UAM server of the user.
1.
After UAM 1 receives an authentication request from the user, UAM 1 forwards the request to
UAM 2 through the RADIUS protocol. UAM 2 authenticates the user identity.
2.
If the user is valid, UAM 2 returns the authentication success message and the access control
policies for the user to UAM 1. UAM 1 informs the access device to permit network access and
control network access according to the policies.
UAM and access device cooperation
An access device forwards packets between endpoint users and UAM. It controls user network access
according to the policies assigned by UAM.