Sample network topology – Grass Valley iControl V.4.43 User Manual
Page 308
Access Control
Sample Network Topology
298
from opening critical Web pages. Access control also associates user names with events, so
that you can see, for example, who acknowledged a specific alarm or reset a latch.
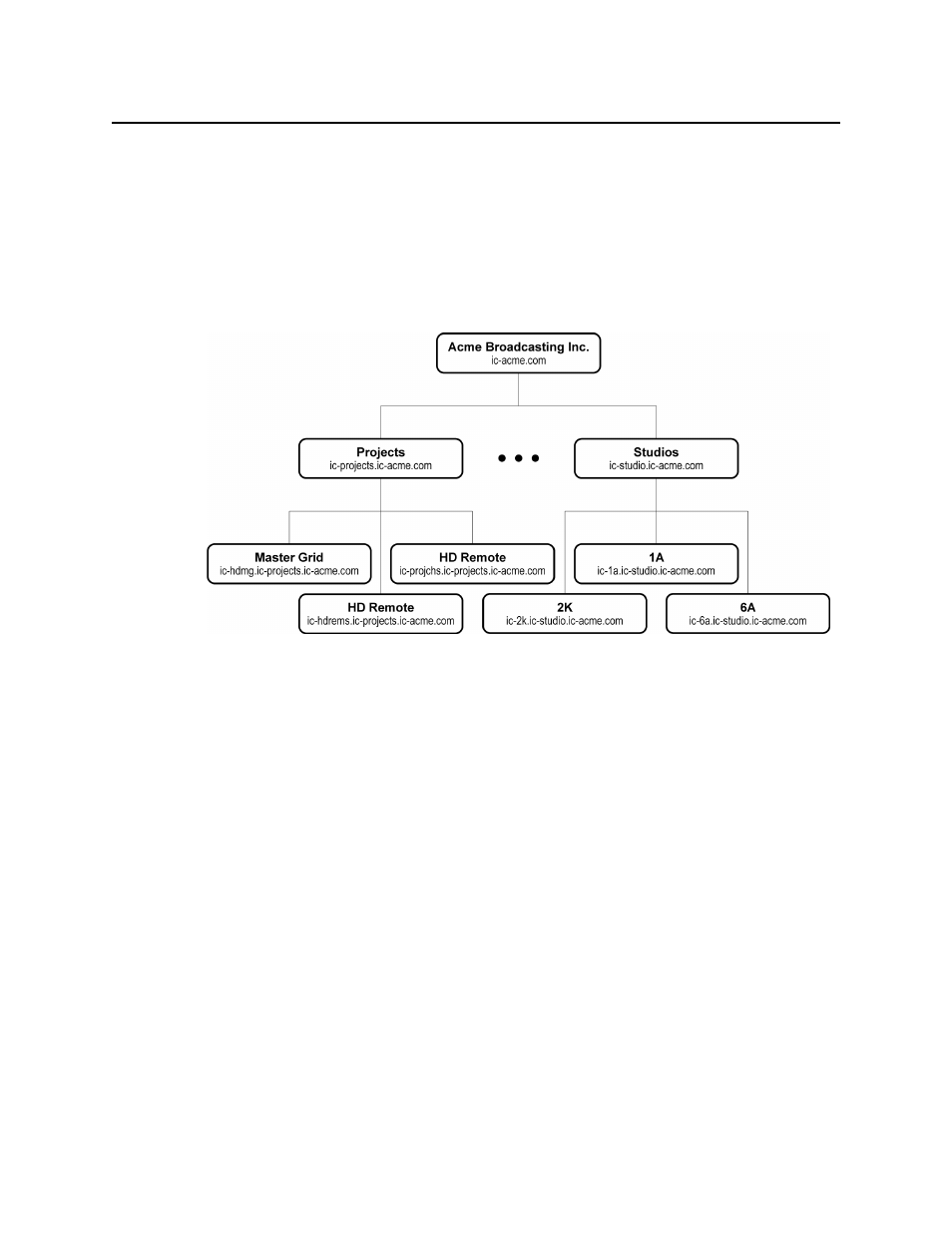
A typical iControl configuration consists of multiple rooms, areas or groups for processing and
distributing content. Each room/area/group has its own hardware equipment including
Miranda Densité and Imaging (Symphonie/Quartet) cards and various third-party equipment.
Each room/area/group also has its own private local area network (LAN). It is convenient to
map these rooms to iControl domains for security considerations. The figure below illustrates
a typical domain architecture.
Figure 6-1
iControl provides multiple domain- and role-based authentication based on the Lightweight
Directory Access Protocol (LDAP). In a typical system, each domain has one LDAP server
(i.e. LDAP running as a service on an iControl Application Server), and manages its own
accounts with top down referrals. In such a configuration, users from a higher level domain
can log on to a lower level one, and vice-versa. For example, in the architecture shown above,
users from the
ic‐projects.ic‐acme.com
or
ic‐acme.com
domains can login directly to
ic‐hdmg.ic‐projects.ic‐acme.com
.
Users from a higher level domain log on to a lower level one with role inheritance. For example,
a user registered as an operator at the top level
ic‐acme.com
could log on to
ic‐projects.ic‐acme.com
as an operator, but would inherit the permissions from the
operator role in the lower-level domain.
Sample Network Topology
The figure below illustrates a general network topology with some sample domains. All
domains are configured with their own private local LAN (192.168) connected to a second
iControl Application Server NIC (eth1). A client PC is configured on the LAN for maintenance
engineers to configure and control equipment in the room. All equipment in the room is also
configured on the local LAN for private access. External PCs on the public network cannot
access any equipment directly.