How ssh works, Configuring arp filtering, Configuration example – H3C Technologies H3C S12500-X Series Switches User Manual
Page 243: Configuration guidelines
231
319B
Configuration example
541B
Network requirements
As shown in
934H
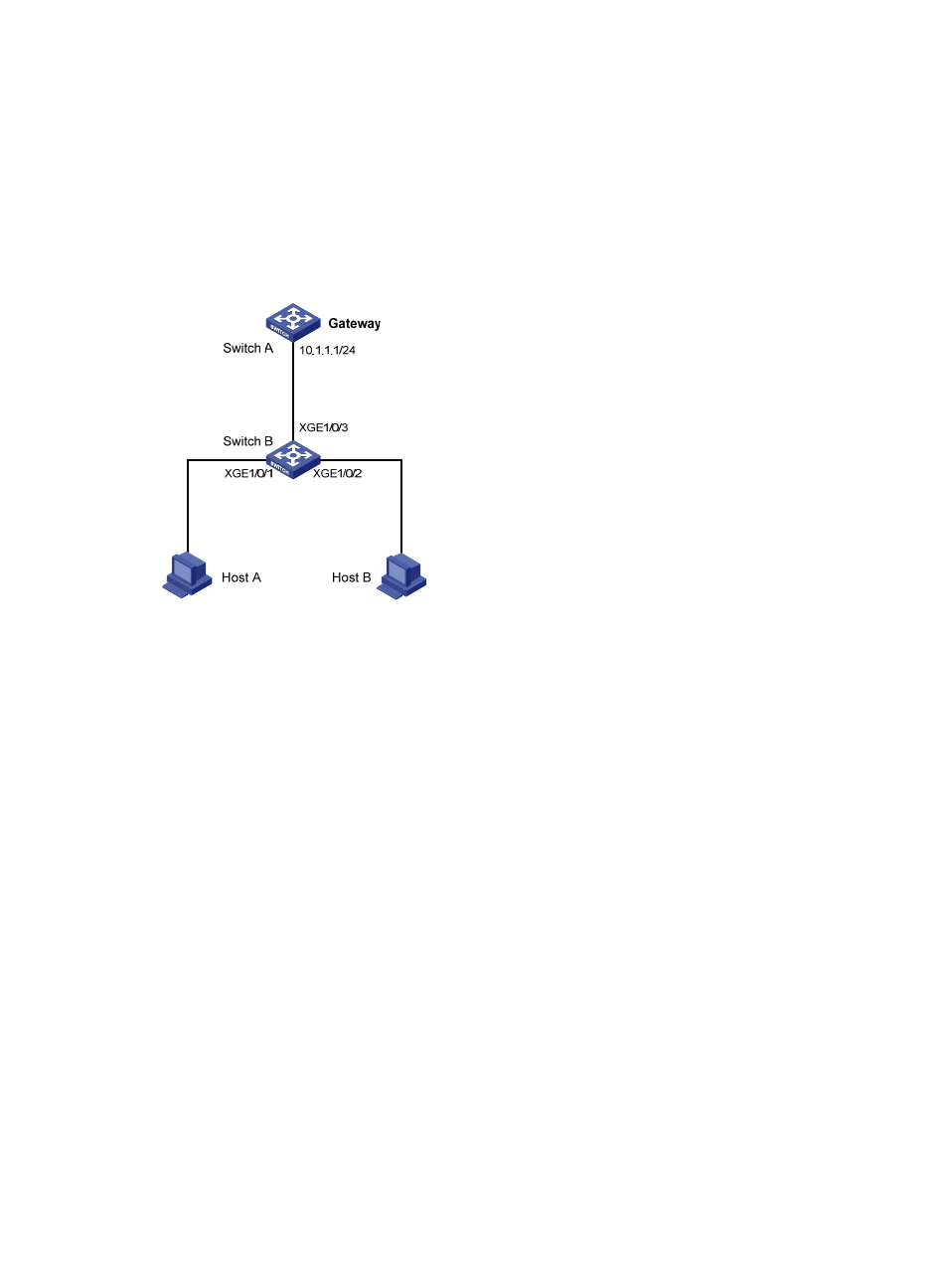
Figure 73
, Host B launches gateway spoofing attacks to Switch B. As a result, traffic that
Switch B intends to send to Switch A is sent to Host B.
Configure Switch B to block such attacks.
Figure 73 Network diagram
542B
Configuration procedure
# Configure ARP gateway protection on Switch B.
<SwitchB> system-view
[SwitchB] interface ten-gigabitethernet 1/0/1
[SwitchB-Ten-GigabitEthernet1/0/1] arp filter source 10.1.1.1
[SwitchB-Ten-GigabitEthernet1/0/1] quit
[SwitchB] interface ten-gigabitethernet 1/0/2
[SwitchB-Ten-GigabitEthernet1/0/2] arp filter source 10.1.1.1
After the configuration is complete, Ten-GigabitEthernet 1/0/1 and Ten-GigabitEthernet 1/0/2 discard
the incoming ARP packets whose sender IP address is the IP address of the gateway.
141B
Configuring ARP filtering
The ARP filtering feature can prevent gateway spoofing and user spoofing attacks.
An interface enabled with this feature checks the sender IP and MAC addresses in a received ARP packet
against permitted entries. If a match is found, the packet is handled correctly. If not, the packet is
discarded.
320B
Configuration guidelines
When you configure ARP filtering, follow these guidelines:
•
You can configure a maximum of eight permitted entries on an interface.
- H3C S5560 Series Switches H3C WX6000 Series Access Controllers H3C WX5000 Series Access Controllers H3C WX3000 Series Unified Switches H3C LSWM1WCM10 Access Controller Module H3C LSWM1WCM20 Access Controller Module H3C LSQM1WCMB0 Access Controller Module H3C LSRM1WCM2A1 Access Controller Module H3C LSBM1WCM2A0 Access Controller Module H3C S9800 Series Switches H3C S5130 Series Switches H3C S5120 Series Switches