Gre encapsulation and de-encapsulation processes, Encapsulation process, De-encapsulation process – H3C Technologies H3C SecPath F1000-E User Manual
Page 14: Gre security options
2
•
GRE over IPv4—The transport protocol is IPv4, and the passenger protocol is any network layer
protocol.
•
GRE over IPv6—The transport protocol is IPv6, and the passenger protocol is any network layer
protocol.
GRE encapsulation and de-encapsulation processes
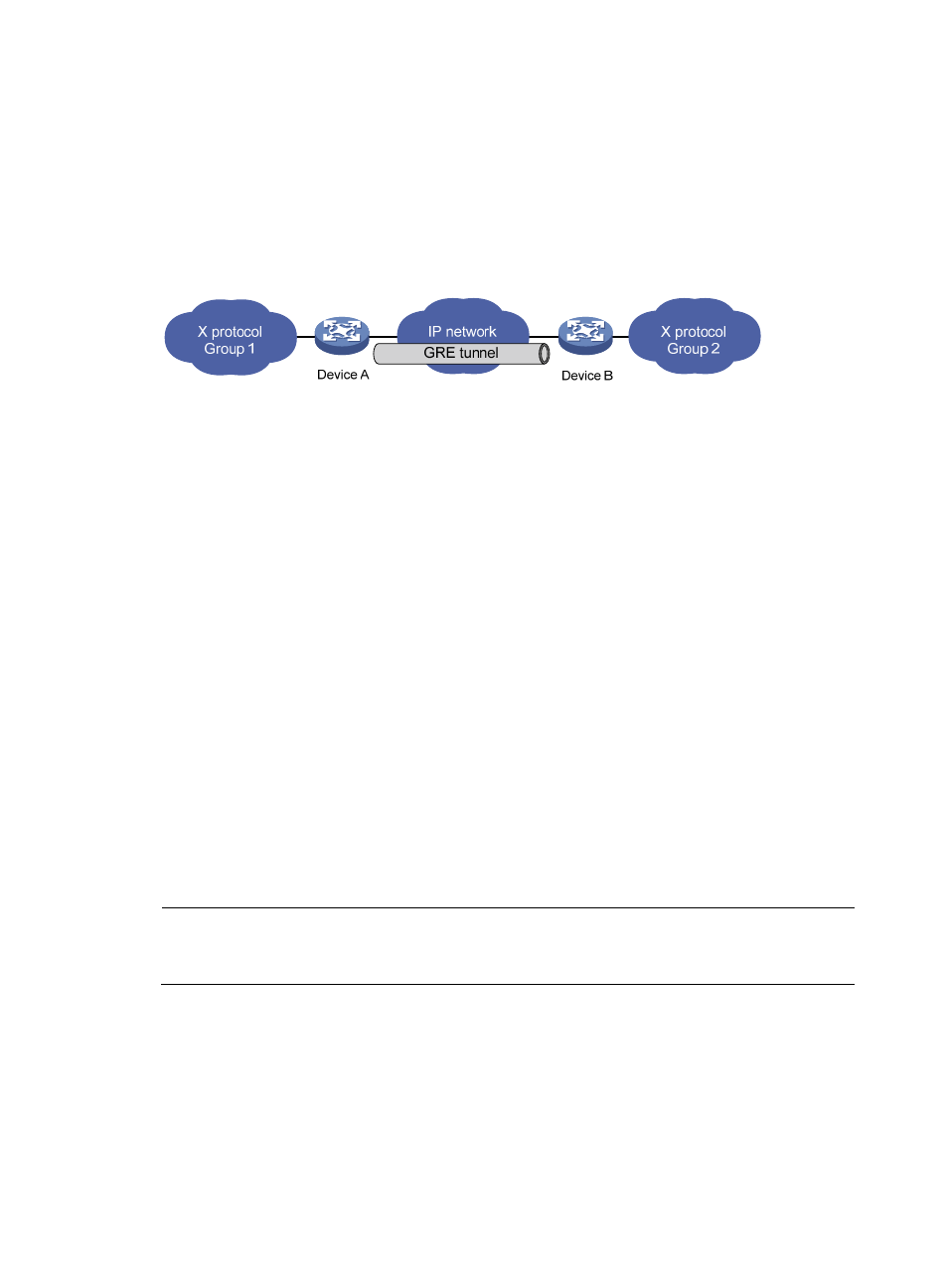
Figure 3 X protocol networks interconnected through a GRE tunnel
The following sections use
to describe how an X protocol packet traverses the IP network through
a GRE tunnel.
Encapsulation process
1.
After receiving an X protocol packet through the interface connected to Group 1, Device A submits
it to the X protocol for processing.
2.
The X protocol checks the destination address field in the packet header to determine how to route
the packet.
3.
If the packet must be tunneled to reach its destination, Device A sends it to the tunnel interface.
4.
Upon receipt of the packet, the tunnel interface encapsulates it in a GRE packet. Then, the system
encapsulates the packet in an IP packet and forwards the IP packet based on its destination
address and the routing table.
De-encapsulation process
De-encapsulation is the reverse of the encapsulation process:
1.
Upon receiving an IP packet from the tunnel interface, Device B checks the destination address.
2.
If the destination is itself and the protocol number in the IP header is 47 (the protocol number for
GRE), Device B strips off the IP header of the packet and submits the resulting packet to the GRE
protocol.
3.
The GRE protocol checks the key, checksum and sequence number in the packet, and then strips
off the GRE header and submits the payload to the X protocol for forwarding.
NOTE:
Encapsulation and de-encapsulation processes on both ends of the GRE tunnel and the resulting increase
in data volumes will degrade the forwarding efficiency of a GRE-enabled device to some extent.
GRE security options
For the purpose of tunnel security, GRE provides two options: tunnel interface key and end-to-end
checksum.
According to RFC 1701,