Ipsec rri configuration example, Network requirements, Configuring secpath a – H3C Technologies H3C SecPath F1000-E User Manual
Page 223
211
IPsec RRI configuration example
Network requirements
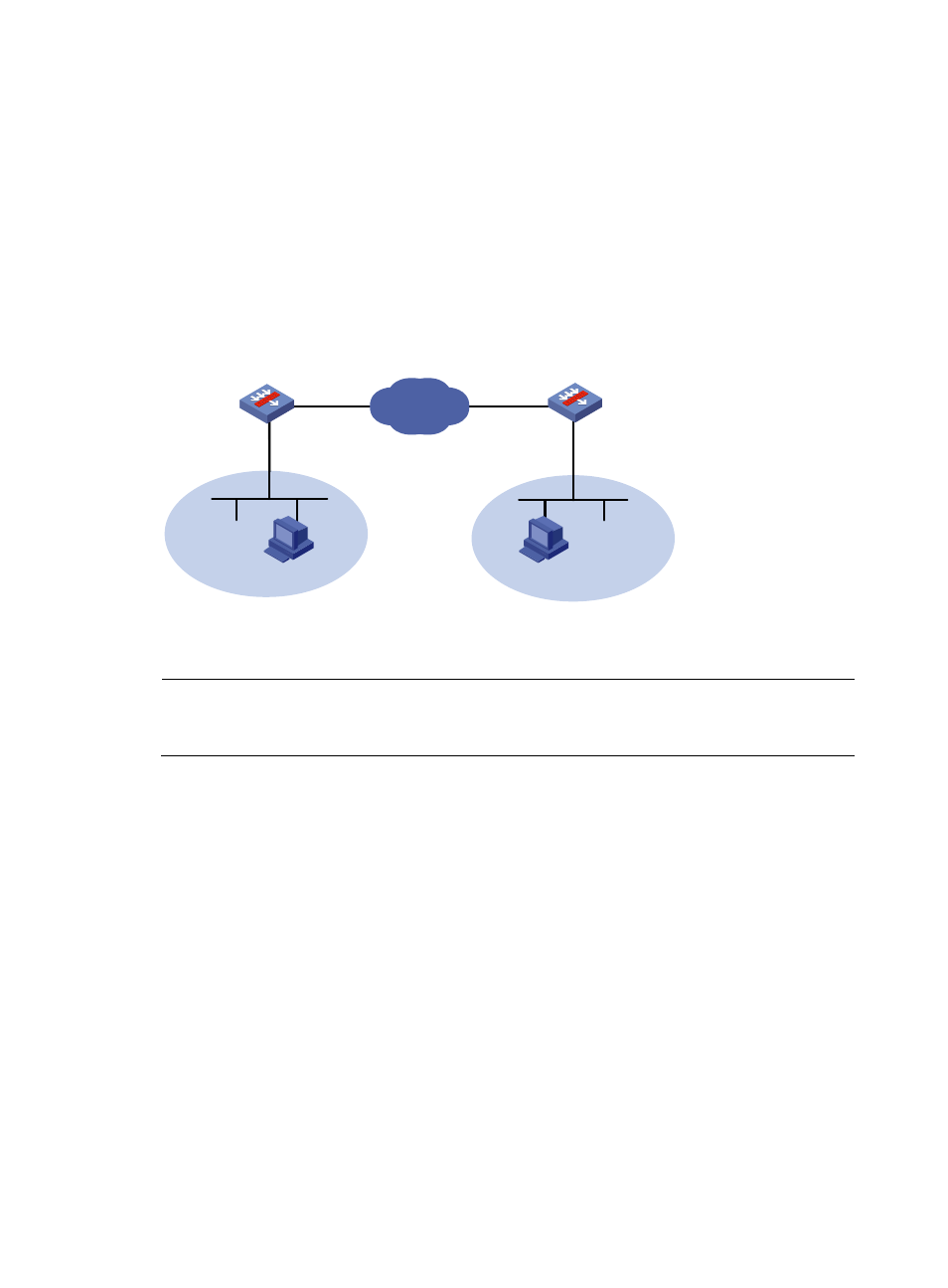
As shown in
, configure an IPsec tunnel between SecPath A and SecPath B to protect the traffic
between the headquarters and the branch. Configure the tunnel to use the security protocol ESP, the
encryption algorithm DES, and the authentication algorithm SHA1-HMAC-96. Use IKE for automatic SA
negotiation.
Configure IPsec RRI on SecPath A to automatically create a static route to the branch based on the
established IPsec SAs. Specify the next hop of the route as 1.1.1.2.
Figure 130 Network diagram
Configuring SecPath A
NOTE:
Assign IPv4 Address to the interfaces. Make sure that SecPath A and SecPath B have IP connectivity
between them.
# Configure ACL 3101 to identify traffic from subnet 10.4.4.0/24 to subnet 10.5.5.0/24.
<SecPathA> system-view
[SecPathA] acl number 3101
[SecPathA-acl-adv-3101] rule permit ip source 10.4.4.0 0.0.0.255 destination 10.5.5 0
0.0.0.255
[SecPathA-acl-adv-3101] quit
# Create IPsec proposal tran1.
[SecPathA] ipsec proposal tran1
# Set the packet encapsulation mode to tunnel.
[SecPathA-ipsec-proposal-tran1] encapsulation-mode tunnel
# Use ESP as the security protocol.
[SecPathA-ipsec-proposal-tran1] transform esp
# Use DES as the encryption algorithm and SHA1-HMAC-96 as the authentication algorithm.
[SecPathA-ipsec-proposal-tran1] esp encryption-algorithm des
[SecPathA-ipsec-proposal-tran1] esp authentication-algorithm sha1
[SecPathA-ipsec-proposal-tran1] quit
Headquarter
Branch
Internet
SecPath A
SecPath B
GE0/1
1.1.1.1/16
GE0/1
2.2.2.2/16
GE0/2
10.4.4.1/24
GE0/2
10.5.5.1/24
Host A
10.4.4.4/24
Host B
10.5.5.5/24