Network requirements, Configuration considerations – H3C Technologies H3C SecPath F1000-E User Manual
Page 157
145
dest addr: 10.1.2.0/255.255.255.0 port: 0 protocol: IP
[inbound ESP SAs]
spi: 1030568546 (0x3d6d3a62)
proposal: ESP-ENCRYPT-DES ESP-AUTH-SHA1
sa duration (kilobytes/sec): 1843200/3600
sa remaining duration (kilobytes/sec): 1843199/3590
max received sequence-number: 4
anti-replay check enable: Y
anti-replay window size: 32
udp encapsulation used for nat traversal: N
[outbound ESP SAs]
spi: 89389742 (0x553faae)
proposal: ESP-ENCRYPT-DES ESP-AUTH-SHA1
sa duration (kilobytes/sec): 1843200/3600
sa remaining duration (kilobytes/sec): 1843199/3590
max received sequence-number: 5
udp encapsulation used for nat traversal: N
Aggressive mode IKE with NAT traversal configuration
example
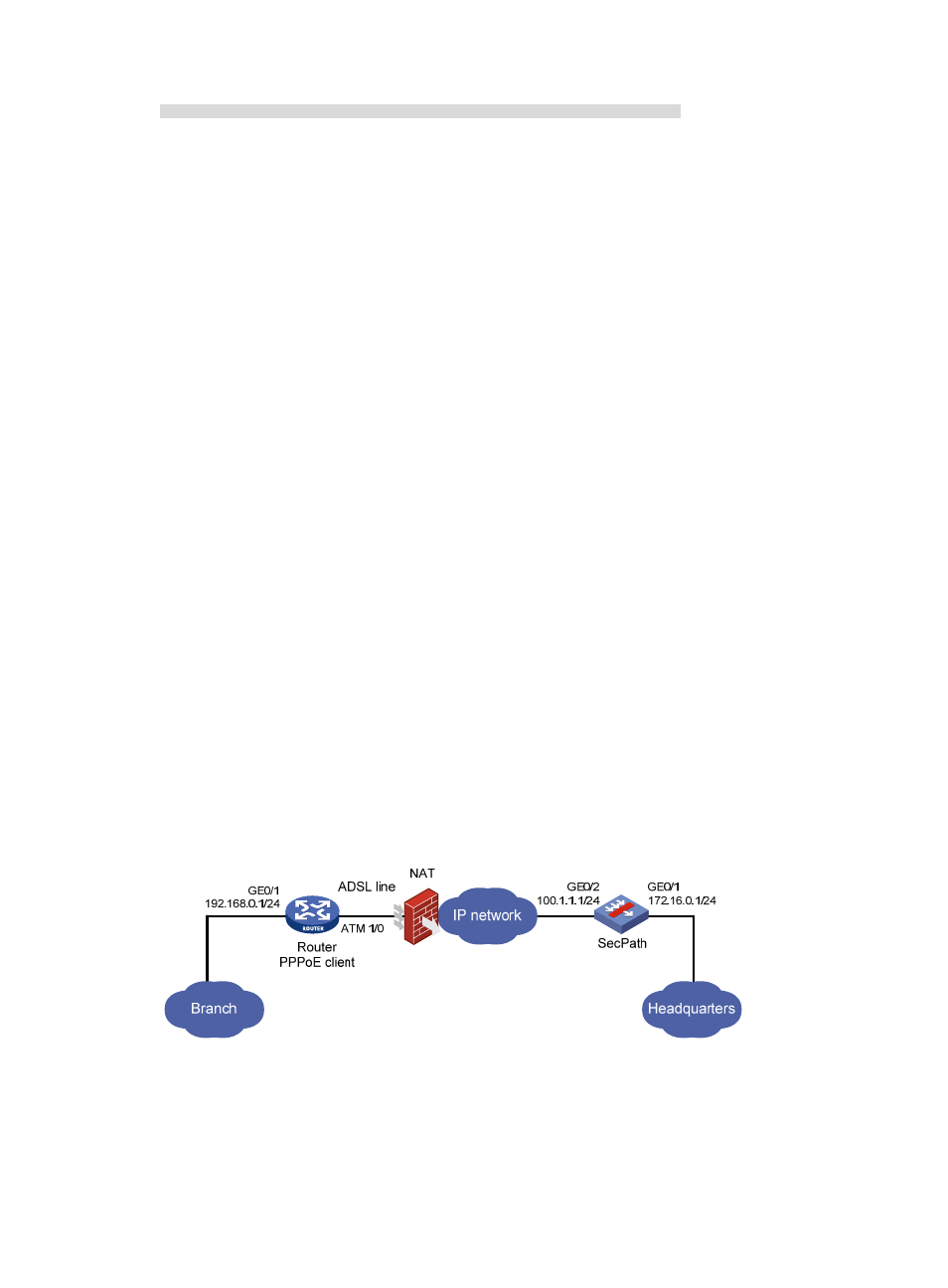
Network requirements
As shown in
, the branch and the headquarters connect to an ATM network through a router
and a SecPath firewall, respectively. The router connects to the public network through an ADSL line and
acts as the PPPoE client. The interface connecting to the public network uses a private address
dynamically assigned by the ISP. The SecPath uses a fixed public IP address for the interface connected
to the public network.
Configure IPsec tunnels between the router and SecPath to protect traffic between the branch and its
headquarters. Use IKE to establish the IPsec tunnels.
Figure 94 Network diagram
Configuration considerations
•
The IKE negotiation mode must be aggressive because Router uses a dynamic IP address.
•
Configure NAT traversal at both ends of the IPsec tunnel because one end of the tunnel uses a public
IP address but the other end uses a private IP address.