Verifying the configuration – H3C Technologies H3C SecPath F1000-E User Manual
Page 53
41
This makes the priority of this route lower than that of the static route of interface Tunnel0, making
sure that SecPath C prefers the tunnel between SecPath A and SecPath C for packet forwarding.
a.
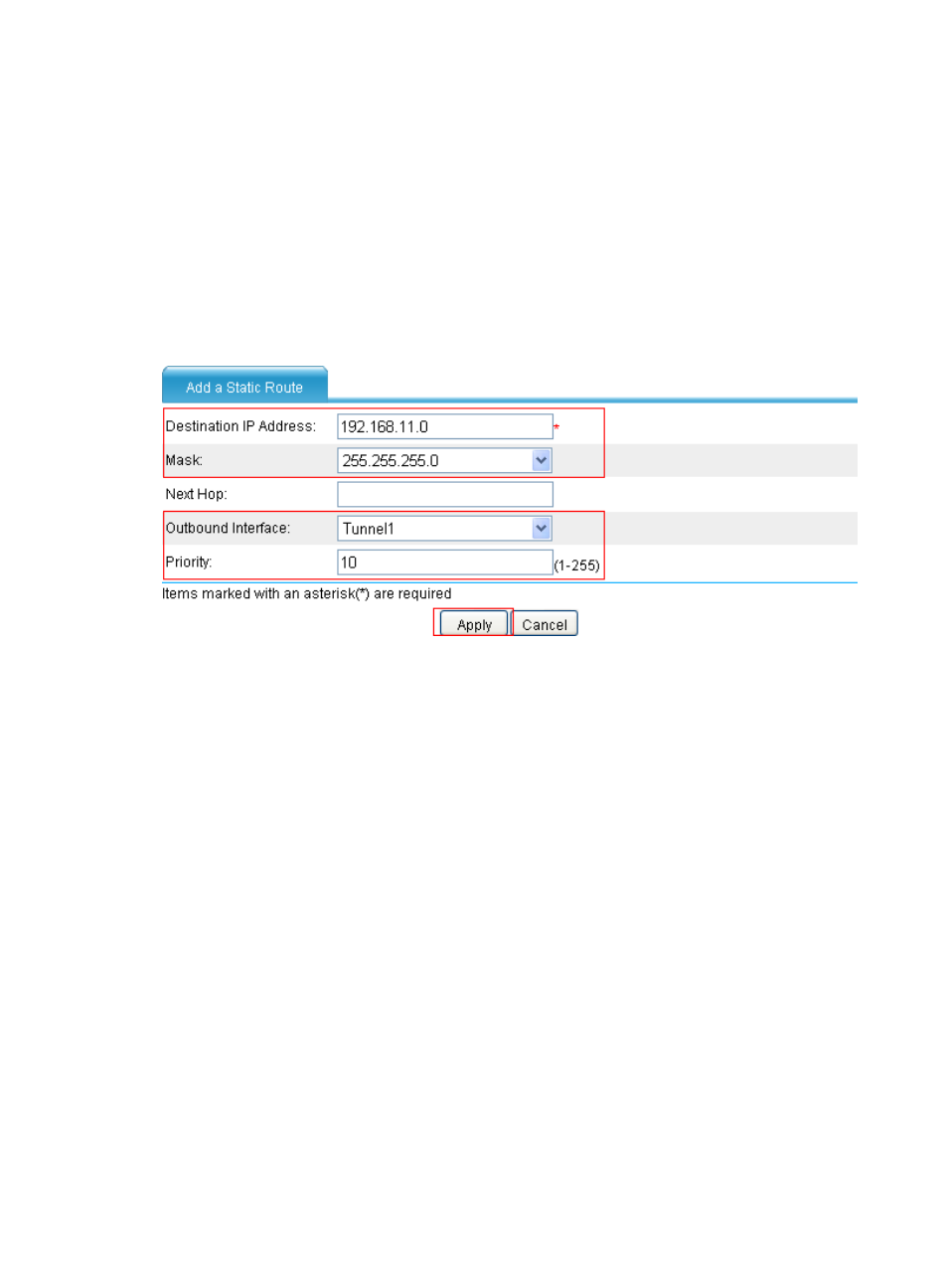
On the static route management page, click Add to perform the configurations shown in
b.
Enter 192.168.11.0 as the destination IP address.
c.
Select mask 255.255.255.0.
d.
Select Tunnel1 as the outbound interface.
e.
Enter priority 10.
f.
Click Apply.
Figure 40 Adding a static route from SecPath C through interface Tunnel 1 to the headquarters node
If the link between SecPath A and SecPath C goes down, SecPath C will sense the failure and try to send
packets to SecPath B, initiating the establishment of the tunnel between SecPath B and SecPath C. Only
then can SecPath B learn the tunnel entry.
If SecPath A and SecPath C are directly connected, configuring a static route on SecPath C can make
sure that SecPath C senses the failure of the link between SecPath A and SecPath C. If the two are not
directly connected, you need to use either of the following methods to achieve the effect:
•
Configure dynamic routing on SecPath A, SecPath B, and SecPath C.
•
On SecPath C, associate the static route with a track entry, so as to use the track entry to track the
status of the static route. For more information about a track entry, see High Availability
Configuration Guide.
Verifying the configuration
1.
Ping Host A from Host C. The ping operation succeeds.
2.
On SecPath A, select VPN > GRE > P2MP from the navigation tree and then click the Tunnel List
tab.
You can see information about the P2MP GRE tunnels established on SecPath A, as shown
in
. There is a tunnel entry to reach the branch network, and packets to the branch
network are forwarded through SecPath A.