Configuring the primary vam server – H3C Technologies H3C SecPath F1000-E User Manual
Page 464
452
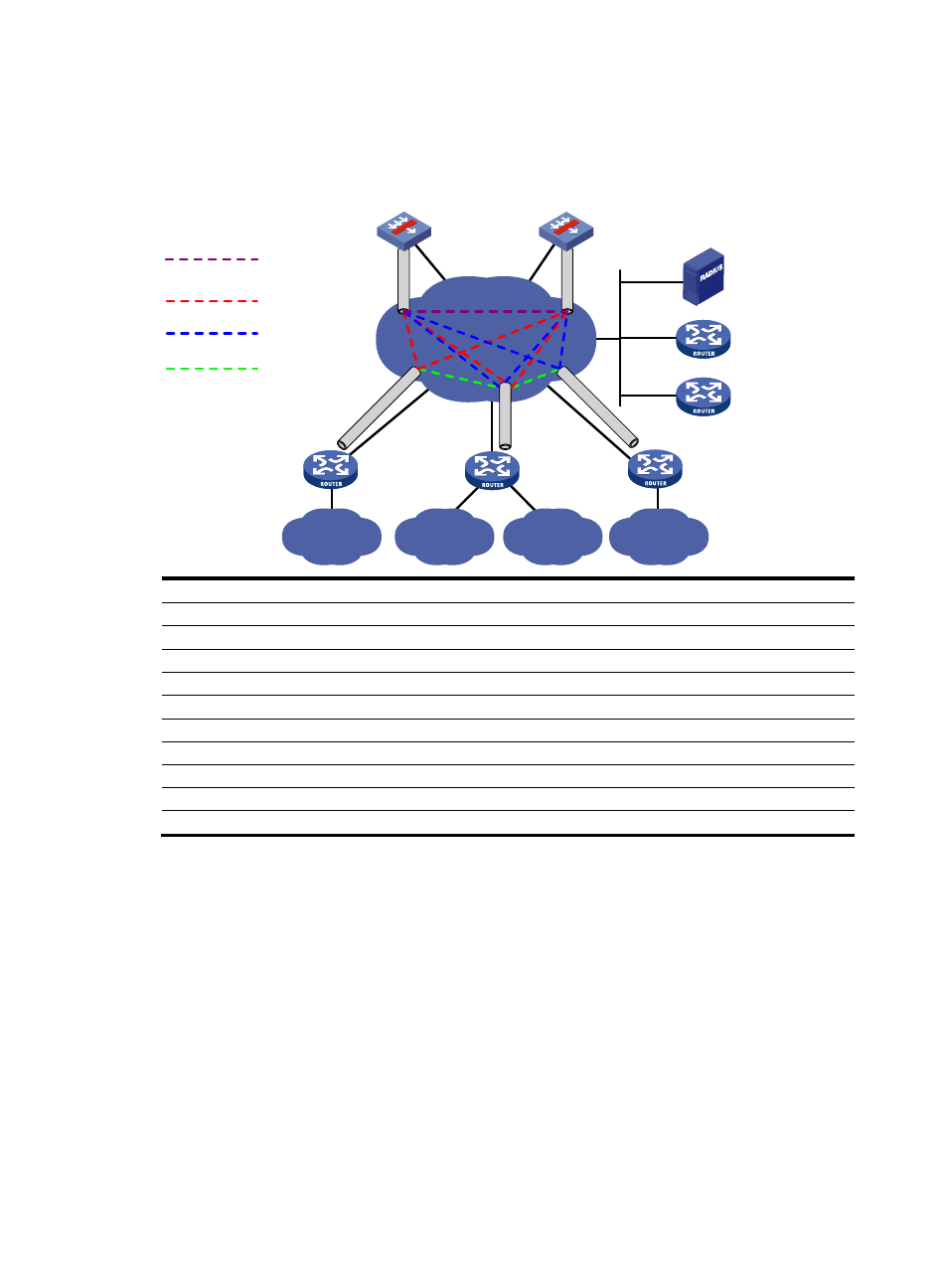
•
A permanent tunnel is established between each hub-spoke pair.
•
Spokes in the same VPN exchange data through dynamically established tunnels between them.
Figure 328 Network diagram
Device Interface
IP
address
Device
Interface IP
address
Hub 1
GE0/2
192.168.1.1/24
Spoke 1
Eth1/1 192.168.1.3/24
Tunnel1
10.0.1.1/24
Eth1/2
10.0.3.1/24
Tunnel2
10.0.2.1/24
Tunnel1 10.0.1.3/24
Hub 2
GE0/2
192.168.1.2/24
Spoke 2
Eth1/1 192.168.1.4/24
Tunnel1
10.0.1.2/24
Eth1/2
10.0.4.1/24
Tunnel2
10.0.2.2/24
Eth1/3 10.0.6.1/24
Spoke 3
Eth1/1
192.168.1.5/24
Tunnel1 10.0.1.4/24
Eth1/2
10.0.5.1/24
Tunnel2
10.0.2.4/24
Tunnel2
10.0.2.3/24
Primary server
Eth1/1 192.168.1.22/24
AAA server
192.168.1.11/24
Secondary server Eth1/1 192.168.1.33//24
Configuring the primary VAM server
1.
Configure IP addresses for the interfaces. (Details not shown.)
2.
Configure AAA:
<PrimaryServer> system-view
# Configure RADIUS scheme radsun.
[PrimaryServer] radius scheme radsun
[PrimaryServer-radius-radsun] primary authentication 192.168.1.11 1812
[PrimaryServer-radius-radsun] primary accounting 192.168.1.11 1813
[PrimaryServer-radius-radsun] key authentication expert
[PrimaryServer-radius-radsun] key accounting expert
[PrimaryServer-radius-radsun] server-type standard
[PrimaryServer-radius-radsun] user-name-format with-domain
[PrimaryServer-radius-radsun] quit
Hub 1
Hub 2
Spoke 1
Spoke 3
Site 1
Site 4
Spoke 2
Site 2
IP network
VPN 1 Hub-to-Spoke static tunnel
VPN 2 Hub-to-Spoke static tunnel
Spoke-to-Spoke dynamic tunnel
Primary VAM server
Secondary VAM server
GE0/2
GE0/2
Eth1/1
Eth1/1
Eth1/1
Tunnel1
Tunnel2
Tunnel1
Tunnel2
Tunnel1
Tunnel1
Tunnel2
Tunnel2
Eth1/1
Eth1/1
AAA server
Eth1/2
Eth1/2
Eth1/2
VPN 1 and VPN 2 Hub-to-Hub
static tunnel
Site 3
Eth1/3