1 ipsec vpn manager overview, Ivm functions – H3C Technologies H3C Intelligent Management Center User Manual
Page 11
1
1 IPsec VPN Manager overview
IPsec VPN Manager (IVM) is IMC's service component for managing Layer 3 Virtual Private Networks
that are built using IPsec technologies. Except for MPLS VPNs, IVM classifies Layer 3 VPNs into the
following types for management:
•
IPsec VPN—Transmits IP packets over IPsec tunnels.
•
GRE over IPsec VPN—Transmits GRE IP packets over IPsec tunnels, in which IP, IPX, and routing
protocols are payloads for GRE encapsulation.
•
DVPN—Transmits IP packets over dynamic VPN tunnels that are established by using VAM and are
protected by IPsec.
MPLS VPNs are managed in MVM. For more information, see HP IMC MPLS VPN Manager
Administrator Guide.
IPsec protects traffic based on ACLs or routes. In IVM, you can configure IPsec security policies to
reference advanced ACLs (3000 to 3999) that define the traffic to protect, and bind the policies to the
physical ports of IPsec VPNs or GRE over IPsec VPNs. DVPN traffic can be protected based on routes.
You can configure an IPsec profile that includes IPsec security settings and apply the profile to tunnel
interfaces.
IVM functions
IVM provides the following management functions:
•
VPN domain management—To improve management efficiency, IVM allows operators to manage
tunnels in groups for IPsec VPNs. Most tunnels in the VPN domain have the same IPsec
configuration. IVM supports the following VPN domain types: IPsec VPN, GRE over IPsec, and
DVPN.
•
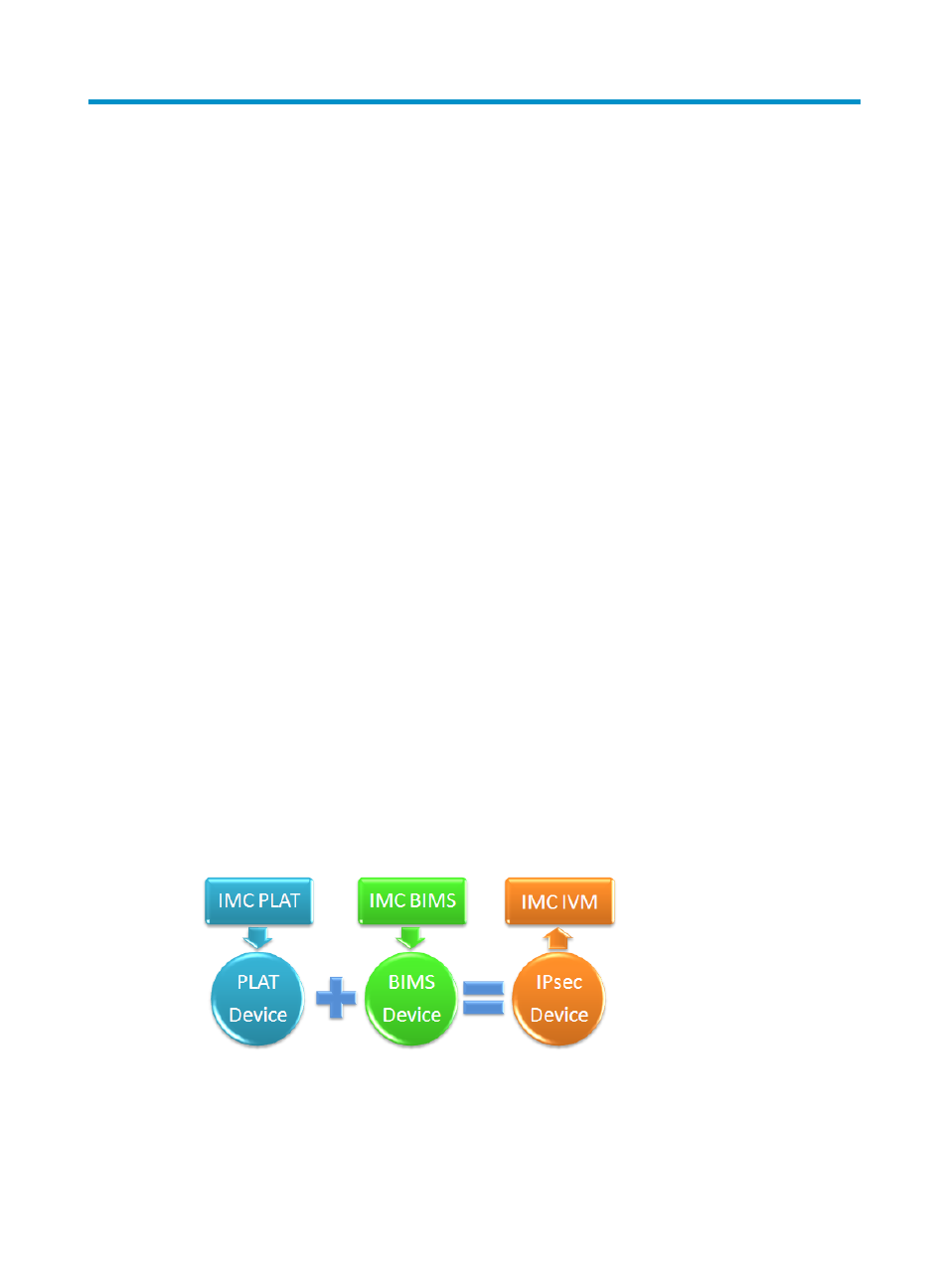
IPsec device management—To manage IPsec-capable devices, first import network devices to IVM
from the IMC Platform or IMC BIMS. IVM automatically filters out unsupported devices and
identifies IPsec devices by their sources: Platform devices or BIMS devices.
Figure 1 IPsec devices
•
IPsec tunnel management—Identifies tunnel configurations on IPsec devices and keeps the
connection records for tunnels. The tunnel configurations include IPsec, GRE over IPsec, and DVPN
tunnels, and can be deployed from IVM or manually configured at the CLI.