PLANET VIP-191 User Manual
Page 117
The user first needs to enter a password that must be entered in both the wireless access point/router
and the WiFi phone. This password can be between 8 and 63 characters and can include special
characters and spaces. To initially connect the phone to the AP, the user has to enter and submit a
password that matches that of the AP. Once this first step of authentication is carried out, the Temporal
Key Integrity Protocol (TKIP) will take over and handle the subsequent encryption and automatic
rekeying.
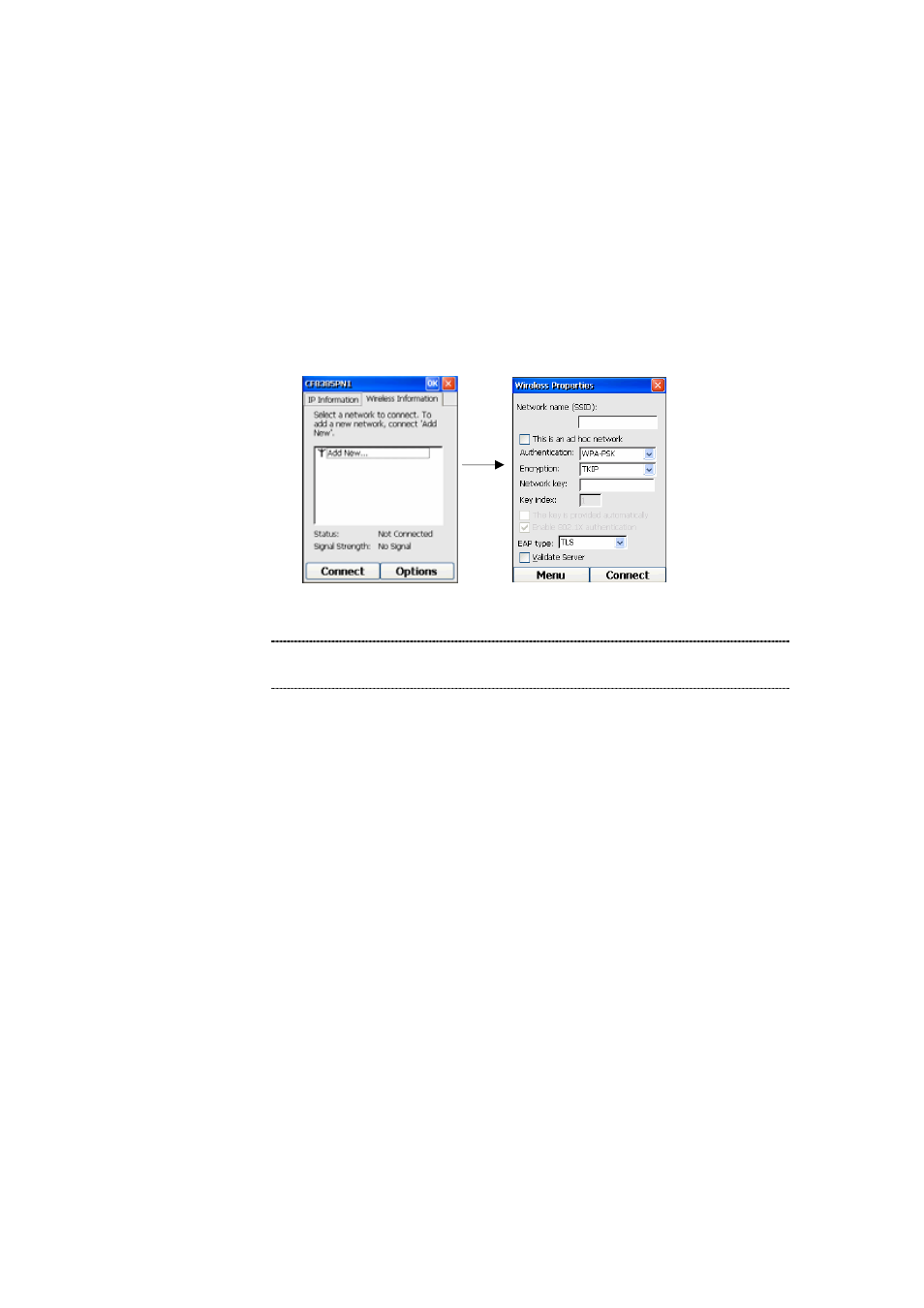
To set up the phone to connect to an AP that uses WPA-PSK, highlight and press the OK Key on “Add
New…” in the AP Connection screen, and choose TKIP for Encryption and WPA-PSK for authentication,
just as shown below:
Figure 206. WPA-PSK mode
L
Note
Since WPA-PSK does not require any certificates, you can
ignore the EAP type setting.
E n t e r p ri se M o d e
The following text is excerpted from the WiFi Alliance web site.
In order to maintain security of an enterprise, Enterprise Mode of WPA leverages the IEEE 802.1X
authentication framework which uses an Extensible Authentication Protocol (EAP) type with an
authentication server to provide strong mutual authentication between the WLAN phone and
authentication server via the access point. This helps to insure that only authorized users are granted
access to the network and that users only access authorized areas within the network.The
authentication server stores the list of the names and credentials of authorized users against which the
server verifies user authenticity. Typically, a Remote Authentication Dial-In User Service (RADIUS)
server is used.
WPA mutual authentication is initiated when a user associates with an access point. The AP blocks
access to the network until the user can be authenticated. The user provides credentials (usually in the
forms passwords and/or certificates) that are communicated to the authentication server. With EAP,
IEEE 802.1X creates a framework in which client workstations and the authentication server mutually
authenticate with one another via the AP. If the authentication server accepts the user’s credentials, the
117