Virtual fragment reassembly configuration example, Network requirements, Configuring the host – H3C Technologies H3C SecPath F1000-E User Manual
Page 110: Configuring the secpath
100
2.
Configure the parameters as described in
.
3.
Click Apply.
Table 40 Configuration items
Item Description
Security Zone
Specify a security zone to be configured with virtual fragment reassembly.
Enable Virtual Fragment
Reassembly
Select the box to enable the virtual fragment reassembly feature.
Specify max number of
concurrent reassemblies
Specify the maximum number of concurrent reassemblies. When this value is
reached, the firewall discards all subsequent packets and sends a syslog
message.
This option is available after the virtual fragment reassembly feature is enabled.
Specify max number of
fragments per reassembly
Specify the maximum number of fragments in each reassembly. When this
value is reached, the firewall discards all subsequent fragments of the
reassembly and sends a syslog.
This option is available after the virtual fragment reassembly feature is enabled.
Specify timeout value of the
datagram being
reassembled
Set the aging time for each reassembly. If the fragments of a datagram (in a
reassembly) are not reassembled within this time, all the fragments of the
datagram are discarded.
This option is available after the virtual fragment reassembly feature is enabled.
Drop all the incoming
fragments
Select the box to discard all incoming fragments.
This option is available after the virtual fragment reassembly feature is enabled.
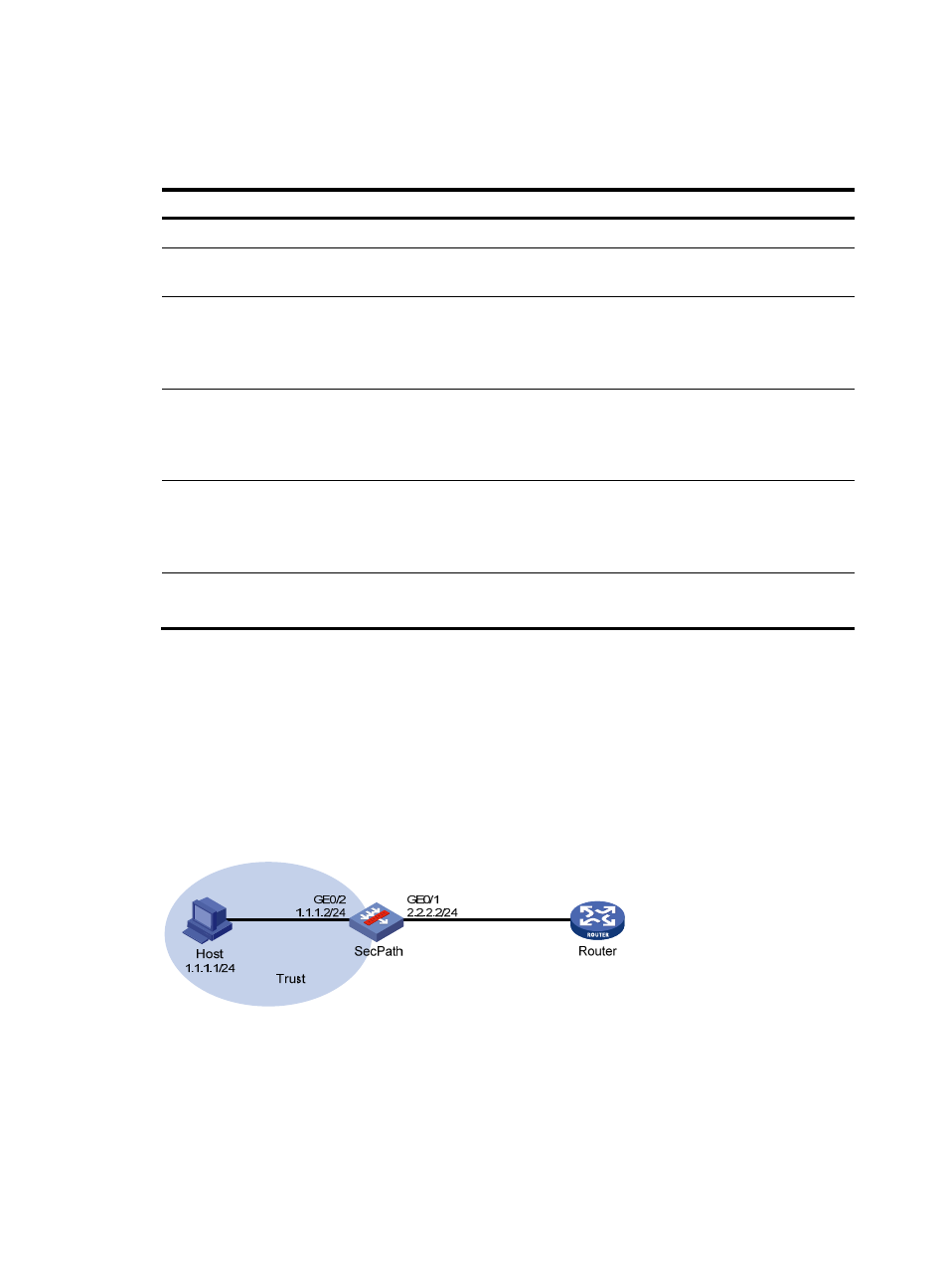
Virtual fragment reassembly configuration example
Network requirements
As shown in
, the host accesses the router through the SecPath, and NAT is enabled on interface
GigabitEthernet 0/1 of the SecPath. Enable virtual fragment reassembly for security zone Trust on the
SecPath to ensure secure and efficient NAT.
Figure 98 Network diagram
Configuring the host
Configure a static route to the router. (Details not shown.)
Configuring the SecPath.
1.
Assign IP addresses to the interfaces and assign the interfaces to the security zones. (Details not
shown.)