Querying policies by ip address, Interzone policy configuration examples, Network requirements – H3C Technologies H3C SecPath F1000-E User Manual
Page 81
71
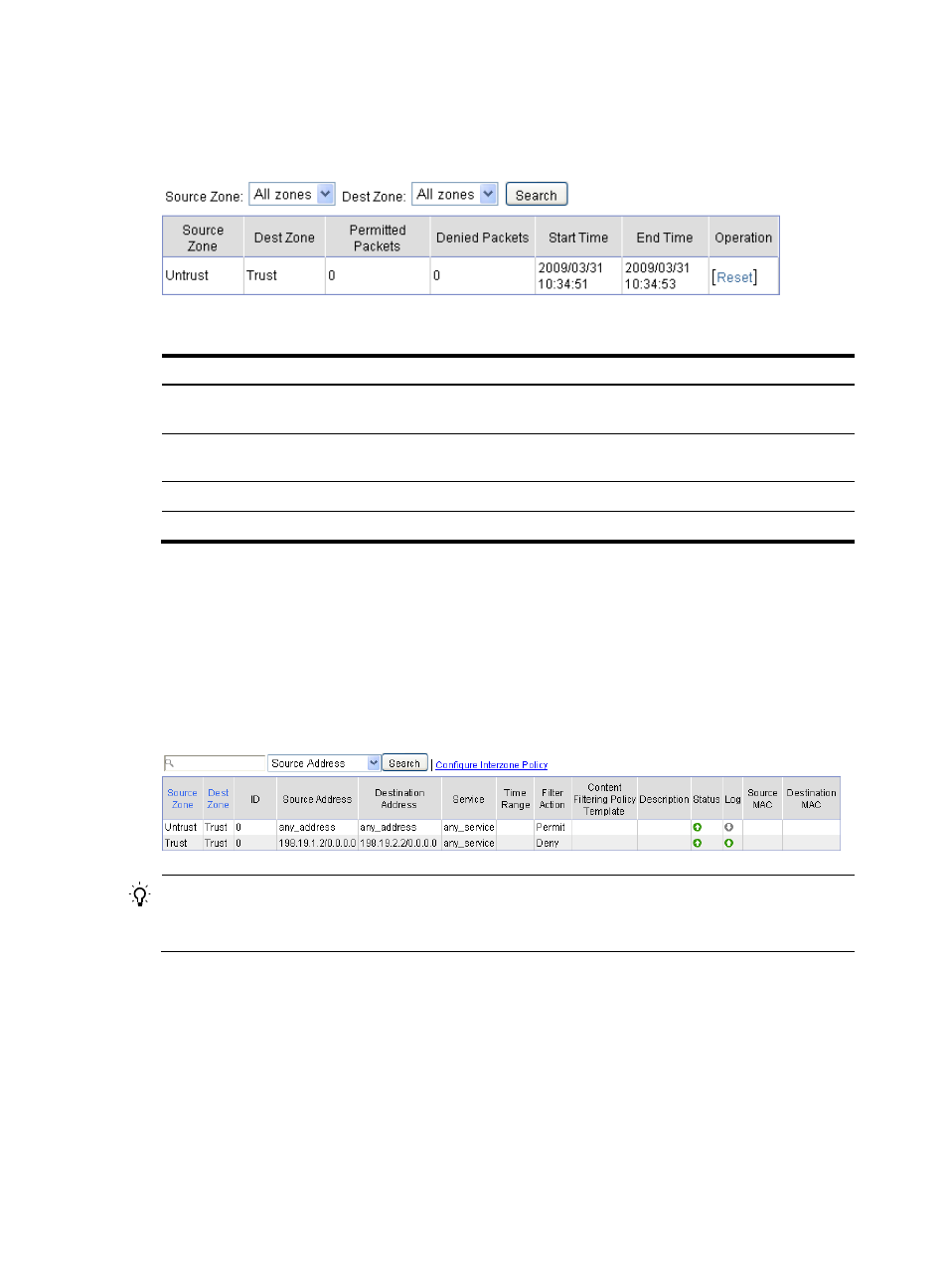
results matching the search conditions. Click Reset in the Operation column to clear the packets statistics
of the related interzone policy and at this time the system starts to perform statistics again.
Figure 71 Statistics of an interzone policy
Table 25 Field description
Item Description
Permitted Packets
Number of packets that match the interzone policy and are forwarded
during the statistics time
Denied Packets
Number of packets that match the interzone policy and are dropped
during the statistics time
Start Time
Start time of the statistics.
End Time
End time of the statistics.
Querying policies by IP address
Select Firewall > Security Policy > Policy Inverse Query from the navigation tree to enter the page as
shown in
. Type the IP address in the field, select whether you want to query by source or
destination IP address from the list, and then click Search. The page displays the policies with the source
or destination IP address.
Figure 72 Query policies by IP address
TIP:
Clicking the Configure Interzone Policy link goes to the interzone policy rule list page. You can also select
Firewall > Security Policy > Interzone Policy from the navigation tree to enter the page.
Interzone policy configuration examples
Network requirements
•
As shown in
, SecPath connects the corporate network to the Internet. The corporate
network belongs to zone Trust, and the external network belongs to zone Untrust.
•
Configure an interzone policy, allowing internal host Public to access the external network at any
time and denying all the other internal hosts’ access to the external network during working hours
(from 8:00 to 18:00) on working days (from Monday through Friday).