Security – Casio Naurtech CETerm Ver.5.5 User Manual User Manual
Page 40
N
AURTECH
E
MULATORS
&
W
EB
B
ROWSER FOR
W
INDOWS
CE
/
W
INDOWS
M
OBILE
CETerm | CE3270 | CE5250 | CEVT220
Page 40
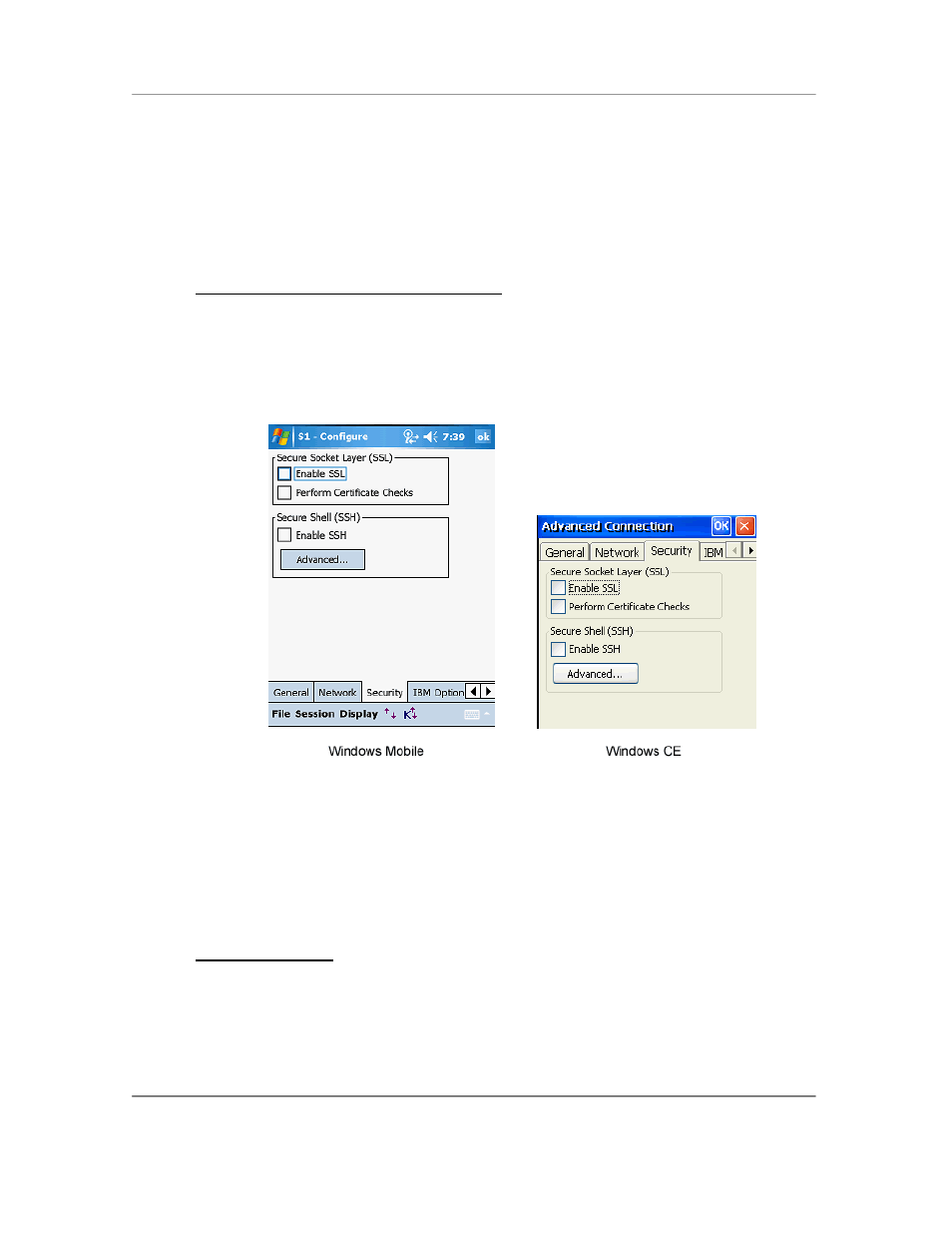
Security
This tab maintains all advanced connection configuration settings for data encryption and
security. Both Secure Shell (SSH) protocol and Secure Sockets Layer (SSL) encryption
are provided for all terminal emulations and web Browser sessions. Use https:
connections to provide SSL for HTML sessions.
Telnet over SSL (Secure Sockets Layer)
SSL or Secure Sockets Layer provides secure encryption of data between a handheld
terminal and the host. It is the underlying security protocol used by web browsers. With
SSL, they host system can also ask for a password to authenticate. This is sent over a
secure encrypted connection.
Enable SSL: Check this option to enable SSL data encryption. Once enabled, all
data sent to the host application is encrypted. All data received is decrypted
Perform Certificate Checks: Check this option if you want the client to perform
checks for valid certificate on the SSL server.
SSH Secure Shell
SSH, or Secure Shell, is a popular, powerful, software-based approach to network
security. Before data is sent by CETerm over a network, it is automatically encrypted
(scrambled) by SSH. The data is automatically decrypted (unscrambled) when it reaches
the host. The result is transparent encryption: users can work normally, unaware that
their communications are safely encrypted on the network. In addition, SSH uses