User keys – Casio Naurtech CETerm Ver.5.5 User Manual User Manual
Page 50
N
AURTECH
E
MULATORS
&
W
EB
B
ROWSER FOR
W
INDOWS
CE
/
W
INDOWS
M
OBILE
CETerm | CE3270 | CE5250 | CEVT220
Page 50
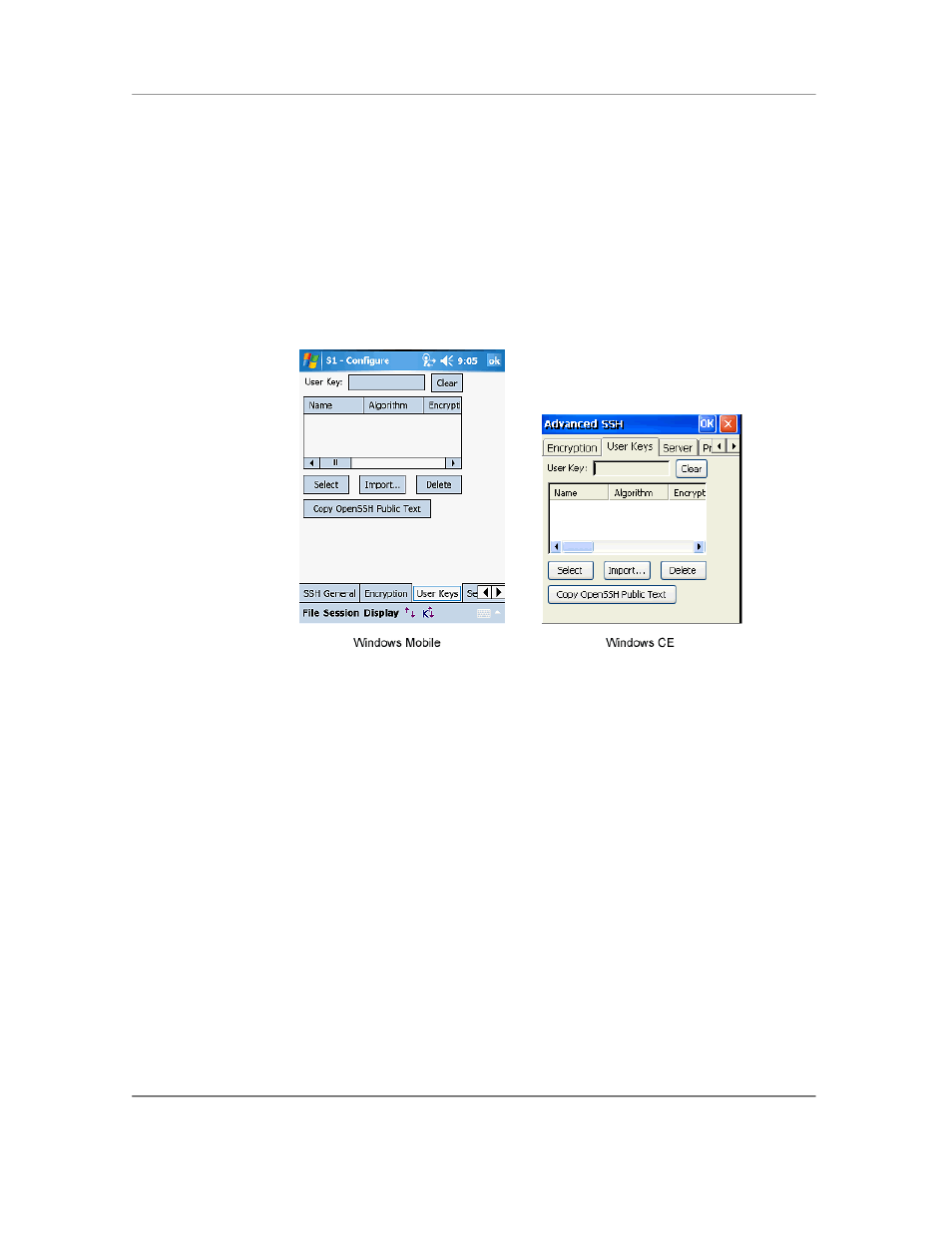
User Keys
This configuration tab manages the User Keys to be used for authentication with the SSH
server. User Keys are used for public key authentication. Public key authentication
requires a key-pair consisting of a public key and a private key. The public key can be
known be everybody whereas the private key is a closely held secret and is usually
encrypted with a corresponding passphrase.
The public key is copied to the server and the private key is imported into CETerm. The
private key is stored in CETerm in the encrypted form. The server and CETerm use the
keys to authenticate the login request.
User Key: This is the key which has been selected for use with the current
session. It can only be selected from the keys which have been imported into
CETerm.
Clear: This will remove any currently selected key for the session. Without a
key, the SSH connection will attempt to use password or other authentication
mechanisms.
Select: This button selects the highlighted key in the table to be used as the
User Key for this session.
Import: Tap this button to import a key into CETerm. CETerm can import keys
generated for OpenSSH and ssh.com servers and some SSH client tools.
Delete: Tapping this button will delete the highlighted key from the table and
remove it from CETerm settings.
Copy OpenSSH Public Text: Tapping this button will copy the public text for the
highlighted key into the device cut-and-paste clipboard and display the text in a
popup window. This text is commonly put in the ―authorized_keys‖ file in the
user‘s home directory on the server.