Encryption – Casio Naurtech CETerm Ver.5.5 User Manual User Manual
Page 48
N
AURTECH
E
MULATORS
&
W
EB
B
ROWSER FOR
W
INDOWS
CE
/
W
INDOWS
M
OBILE
CETerm | CE3270 | CE5250 | CEVT220
Page 48
Encryption
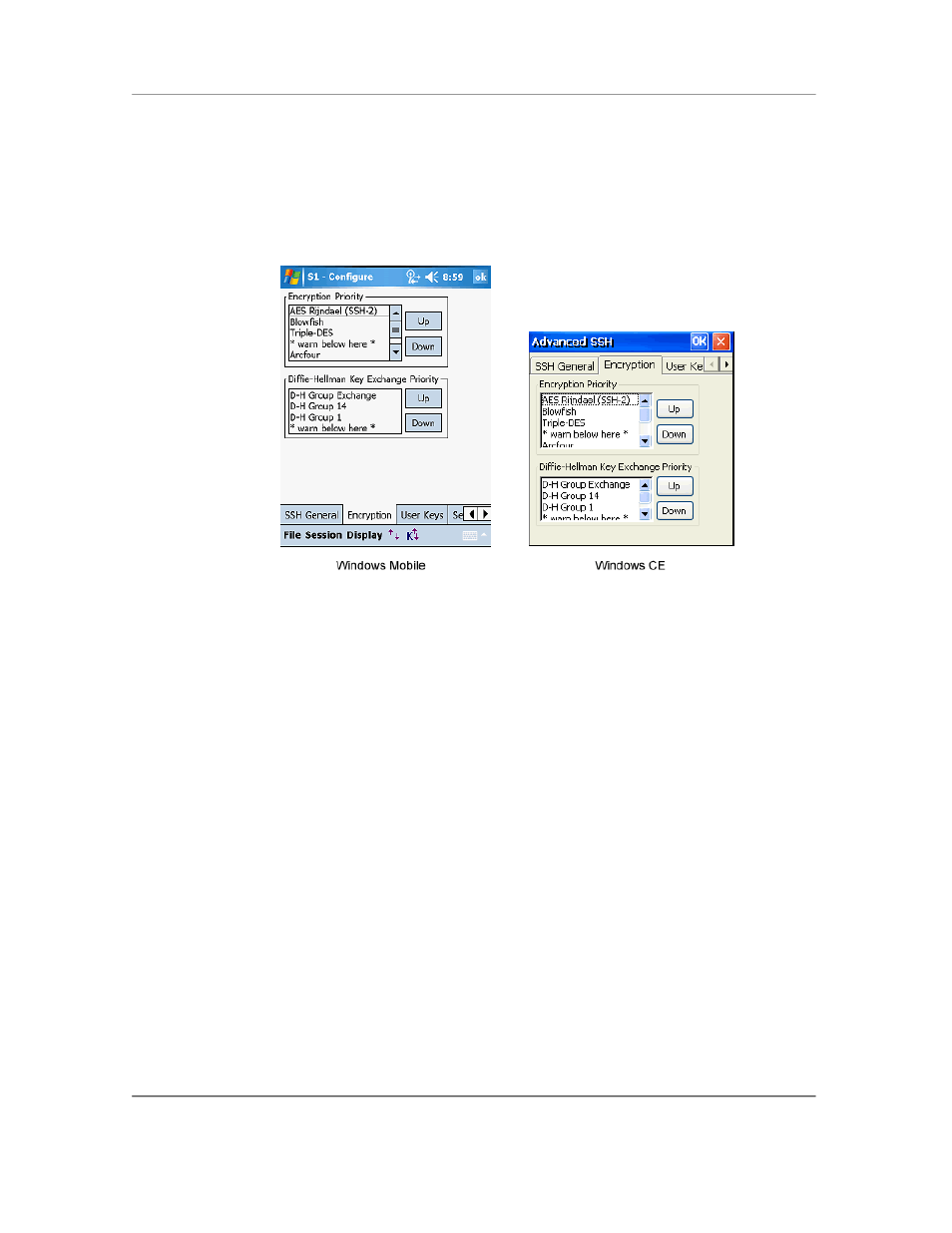
CETerm supports a variety of different encryption algorithms, and allows you to prioritize
which one you prefer to use. Use this configuration tab to set a priority preference for the
SSH encryption algorithms.
Encryption Priority: Highlight the preferred encryption algorithm and use the up
and down buttons to position it in the list box to specify a priority preference
order. When you make an SSH connection, CETerm will search down the list
from the top until it finds an algorithm supported by the server, and then use that.
By default, CETerm list the following encryption algorithms in priority order:
-
AES Rijndael (SSH-2)
-
Blowfish
-
Triple-DES
-
* warn below here *
-
Arcfour
-
* ignore following *
-
DES
If the encryption algorithm which CETerm finds is below the ‗warn below here‘
line, you will see a warning box when you make the connection:
The first cipher supported by the server
is single-DES, which is below the configured
warning threshold.
Do you want to continue with this connection?
This warns you that the first available encryption is not a very secure one.
Typically you would put the ―* warn below here *‖ line between the encryptions
you consider secure and the ones you consider substandard. By default,