1x access control method, 1x timers – H3C Technologies H3C S5120 Series Switches User Manual
Page 387
1-9
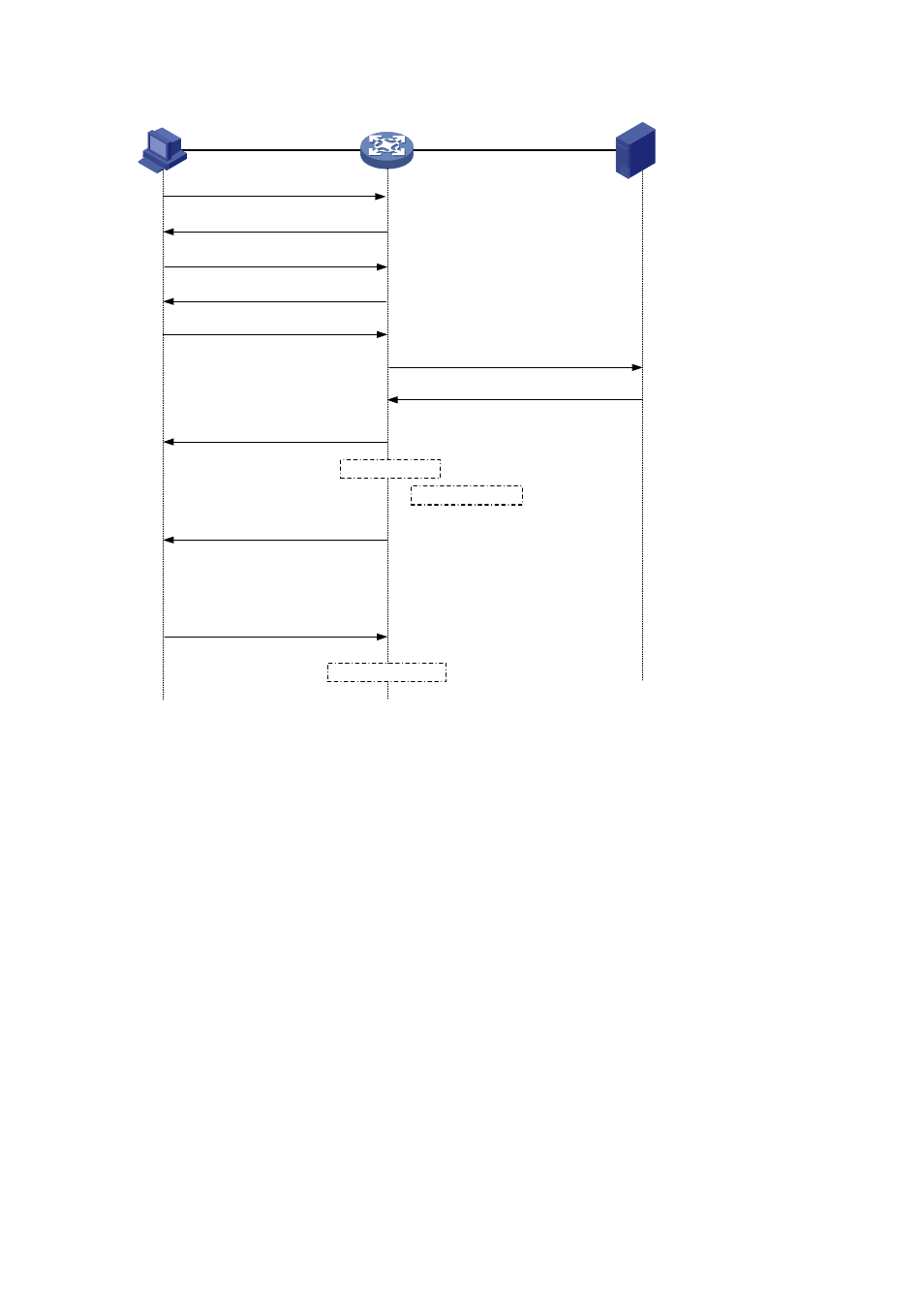
Figure 1-9 Message exchange in EAP termination mode
EAPOL
EAPOR
EAPOL-Start
EAP-Request / Identity
EAP-Response / Identity
EAP-Request / MD5 challenge
EAP-Success
EAP-Response / MD5 challenge
Handshake request
[ EAP-Request / Identity ]
Handshake response
[ EAP-Response / Identity ]
EAPOL-Logoff
......
Client
Device
Server
Port authorized
Handshake timer
Port unauthorized
RADIUS Access-Request
(CHAP-Response / MD5 challenge)
RADIUS Access-Accept
(CHAP-Success)
Different from the authentication process in EAP relay mode, it is the device that generates the random
challenge for encrypting the user password information in EAP termination authentication process.
Consequently, the device sends the challenge together with the username and encrypted password
information from the client to the RADIUS server for authentication.
802.1X Access Control Method
H3C devices not only implement the port-based access control method defined in the 802.1X protocol,
but also extend and optimize the protocol by supporting the MAC-based access control method.
z
Port-based access control: With this method configured on a port, after a user connected to the
port passes authentication, all subsequent users of the port can access network resources without
authentication. However, when the authenticated user logs off, the others are denied as well.
z
MAC-based access control: With this method configured on a port, all users of the port must be
authenticated separately, and when a user logs off, no other users are affected.
802.1X Timers
This section describes the timers used on an 802.1X device to guarantee that the client, the device, and
the RADIUS server can interact with each other in a reasonable manner.