Network requirements, Configuration procedure – H3C Technologies H3C S5120 Series Switches User Manual
Page 466
1-20
(Omitted)
You can also use some other display commands to view more information about the CA certificate. See
the display pki certificate ca domain command in PKI Commands.
Configuring a Certificate Attribute-Based Access Control Policy
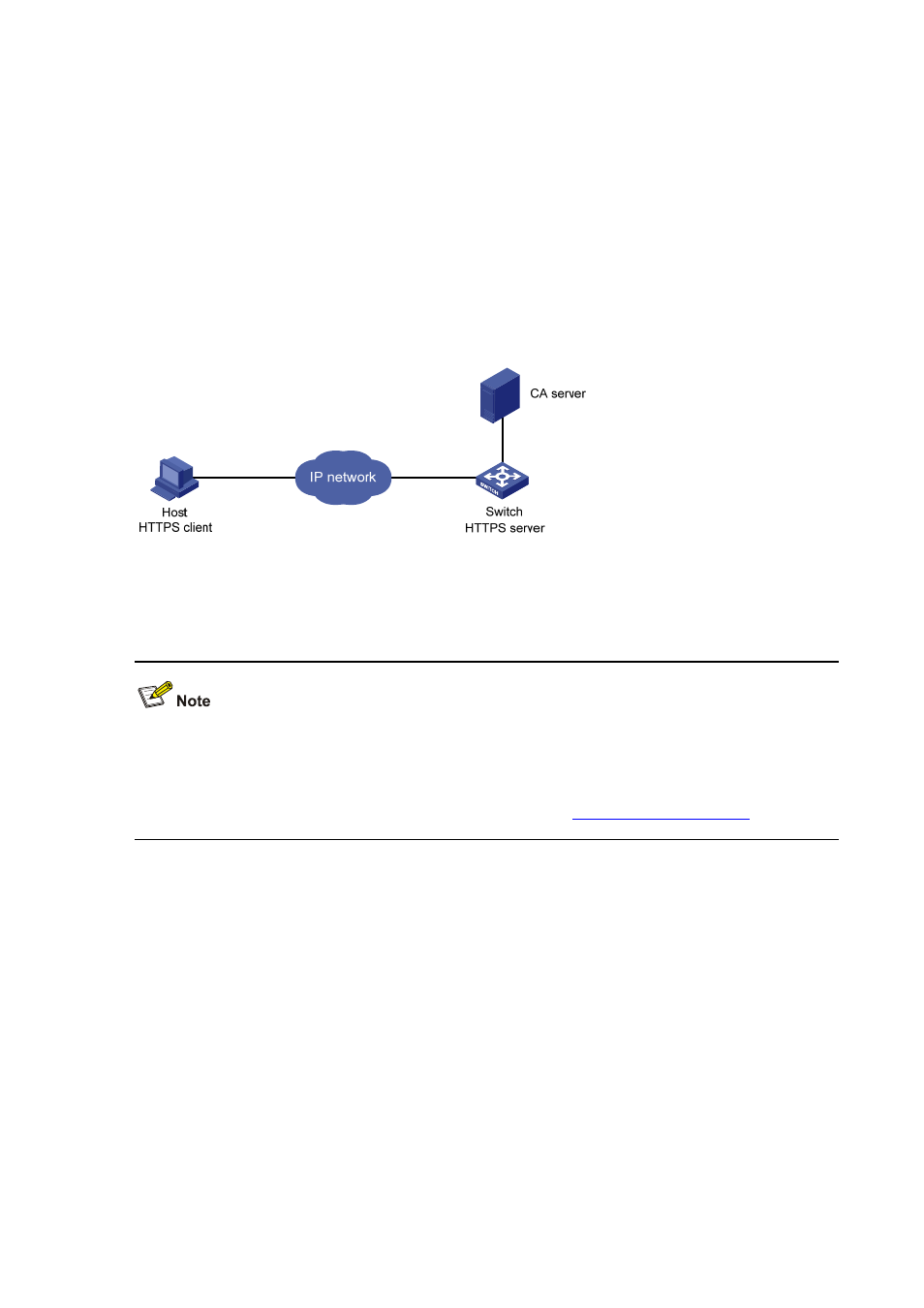
Network requirements
z
The client accesses the remote HTTP Security (HTTPS) server through the HTTPS protocol.
z
SSL is configured to ensure that only legal clients log into the HTTPS server.
z
Create a certificate attribute-based access control policy to control access to the HTTPS server.
Figure 1-4 Configure a certificate attribute-based access control policy
Configuration procedure
z
For more information about SSL configuration, see to SSL Configuration.
z
For more information about HTTPS configuration, see to HTTP Configuration.
z
The PKI domain to be referenced by the SSL policy must be created in advance. For more
information about the configuration of the PKI domain, see
.
1) Configure the HTTPS server
# Configure the SSL policy for the HTTPS server to use.
<Switch> system-view
[Switch] ssl server-policy myssl
[Switch-ssl-server-policy-myssl] pki-domain 1
[Switch-ssl-server-policy-myssl] client-verify enable
[Switch-ssl-server-policy-myssl] quit
2) Configure the certificate attribute group
# Create certificate attribute group mygroup1 and add two attribute rules. The first rule defines that the
DN of the subject name includes the string aabbcc, and the second rule defines that the IP address of
the certificate issuer is 10.0.0.1.
[Switch] pki certificate attribute-group mygroup1
[Switch-pki-cert-attribute-group-mygroup1] attribute 1 subject-name dn ctn aabbcc
[Switch-pki-cert-attribute-group-mygroup1] attribute 2 issuer-name ip equ 10.0.0.1