Aaa for ssh users by a radius server, Network requirements, Configuration procedure – H3C Technologies H3C S5120 Series Switches User Manual
Page 435
1-29
[Switch-radius-rd] quit
# Create a local user named hello.
[Switch] local-user hello
[Switch-luser-hello] service-type telnet
[Switch-luser-hello] password simple hello
[Switch-luser-hello] authorization-attribute level 3
[Switch-luser-hello] quit
[Switch] domain default enable bbb
# Configure the AAA methods for the ISP domain.
[Switch] domain bbb
[Switch-isp-bbb] authentication login local
[Switch-isp-bbb] authorization login local
[Switch-isp-bbb] accounting login radius-scheme rd
[Switch-isp-bbb] quit
# Configure the default AAA methods for all types of users.
[Switch] domain bbb
[Switch-isp-bbb] authentication default local
[Switch-isp-bbb] authorization default local
[Switch-isp-bbb] accounting default radius-scheme rd
When telneting into the switch, a user enters username telnet@bbb for authentication using domain
bbb.
AAA for SSH Users by a RADIUS Server
Network requirements
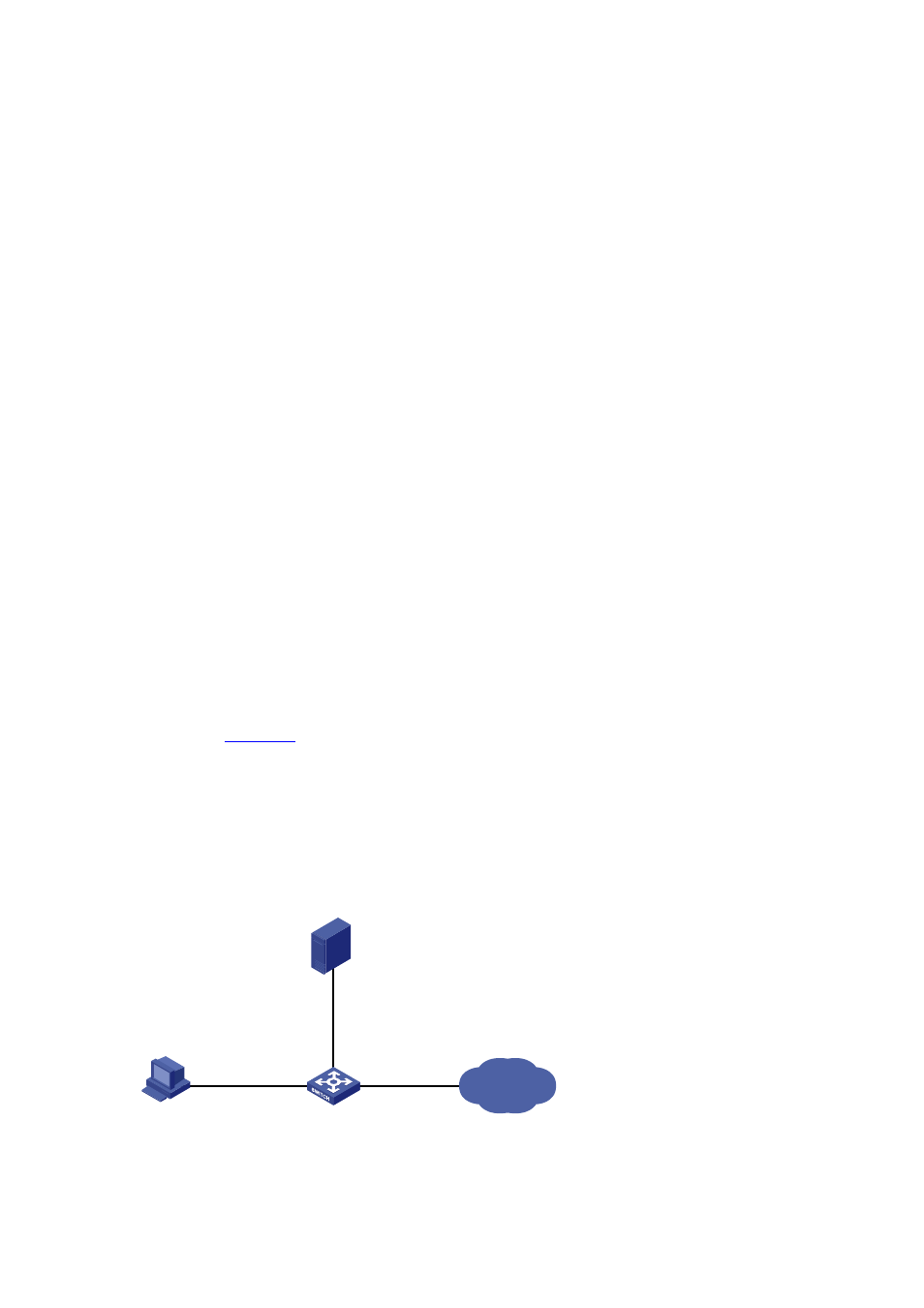
As shown in
z
Configure an iMC server to act as the RADIUS server to provide authentication, authorization, and
accounting services for SSH users. The IP address of the RADIUS server is 10.1.1.1/24.
z
Set both the shared keys for authentication and accounting packets exchanged with the RADIUS
server to expert; and specify that a username sent to the RADIUS server carries the domain name.
The RADIUS server provides different user services according to the domain names.
Figure 1-7 Configure AAA for SSH users by a RADIUS server
Internet
Switch
SSH user
RADIUS server
10.1.1.1/24
Vlan-int2
192.168.1.70/24
Vlan-int3
10.1.1.2/24
Configuration procedure
1) Configure the RADIUS server (iMC)