PLANET XGS3-24040 User Manual
Page 467
Chapter 47 802.1x Configuration
47-7
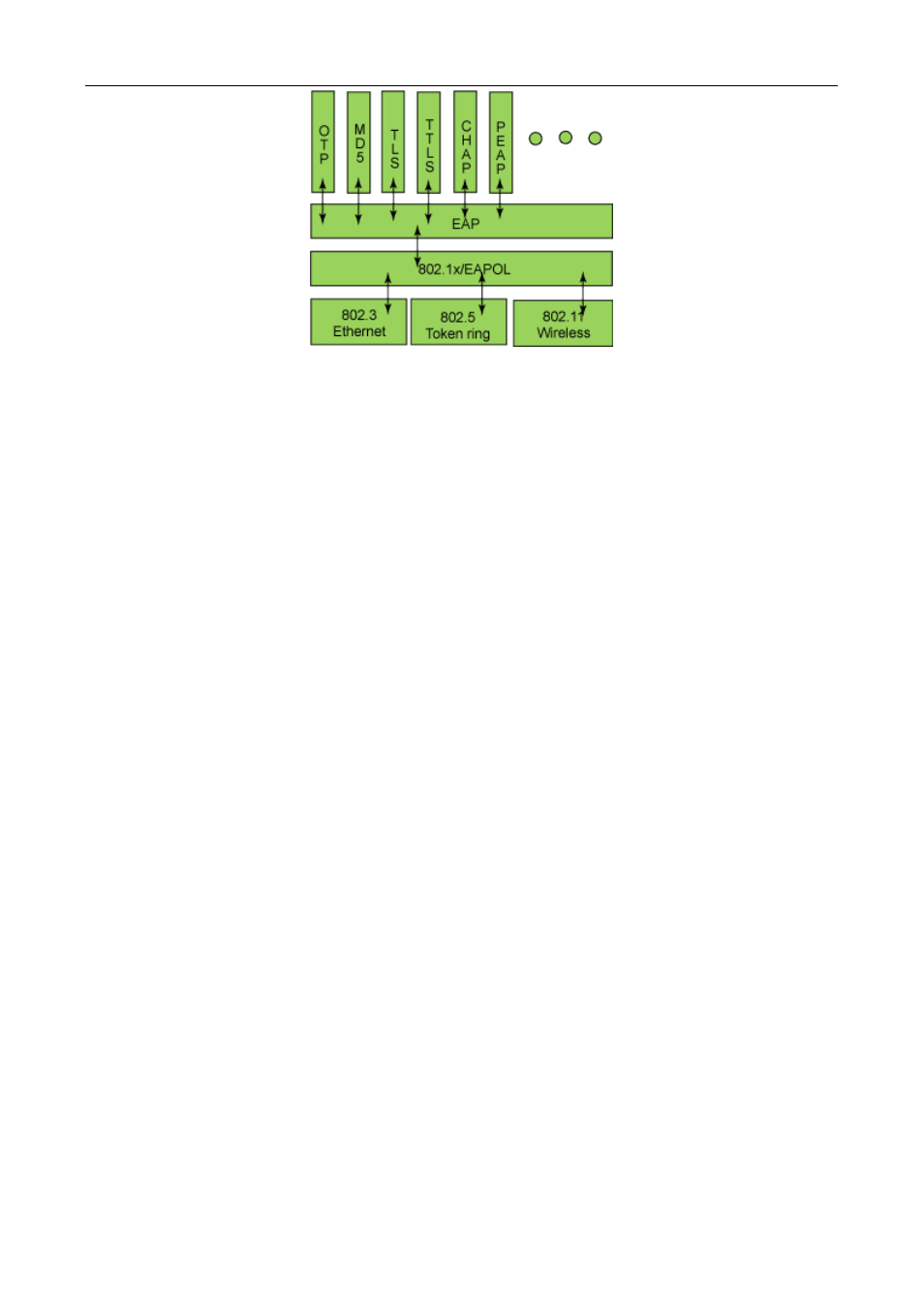
Figure
2-8 the Protocol Stack of EAP Authentication Method
By now, there are more than 50 EAP authentication methods has been developed, the differences among
which are those in the authentication mechanism and the management of keys. The 4 most common EAP
authentication methods are listed as follows:
EAP-MD5
EAP-TLS(Transport Layer Security)
EAP-TTLS(Tunneled Transport Layer Security)
PEAP(Protected Extensible Authentication Protocol)
They will be described in detail in the following part.
Attention:
The switch, as the access controlling unit of Pass-through, will not check the content of a particular
EAP method, so can support all the EAP methods above and all the EAP authentication methods
that may be extended in the future.
In EAP relay, if any authentication method in EAP-MD5, EAP-TLS, EAP-TTLS and PEAP is
adopted, the authentication methods of the supplicant system and the RADIUS server should be
the same.
1. EAP-MD5 Authentication Method
EAP-MD5 is an IETF open standard which providing the least security, since MD5 Hash function is vulnerable
to dictionary attacks.
The following figure illustrated the basic operation flow of the EAP-MD5 authentication method.