Introduction to hwtacacs – H3C Technologies H3C WX3000 Series Unified Switches User Manual
Page 250
25-7
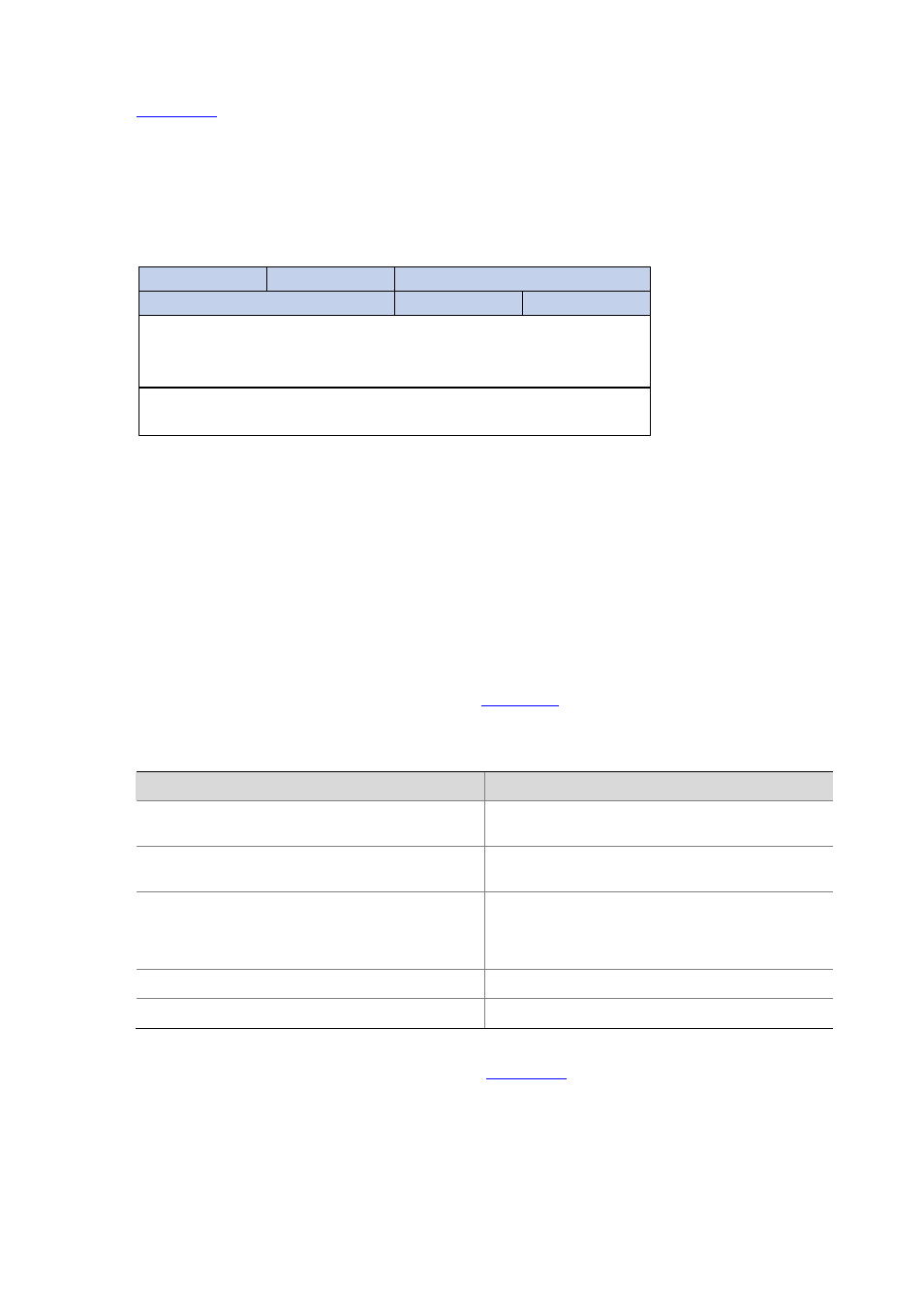
depicts the format of attribute 26. The Vendor-ID field used to identify a vendor occupies
four bytes, where the first byte is 0, and the other three bytes are defined in RFC 1700. Here, the vendor
can encapsulate multiple customized sub-attributes (containing vendor-specific Type, Length and Value)
to implement a RADIUS extension.
Figure 26-4
Vendor-specific attribute format
Type
……
Length
0
7
Vendor-ID
7
15
31
Vendor-ID
Type (specified)
Length (specified)
Specified attribute value……
Introduction to HWTACACS
What is HWTACACS
Huawei Terminal Access Controller Access Control System (HWTACACS) is an enhanced security
protocol based on TACACS (RFC 1492). Similar to the RADIUS protocol, it implements AAA for
different types of users (such as PPP, VPDN, and terminal users) through communicating with TACACS
server in client-server mode.
Compared with RADIUS, HWTACACS provides more reliable transmission and encryption, and
therefore is more suitable for security control.
lists the primary differences between
HWTACACS and RADIUS.
Table 26-3
Differences between HWTACACS and RADIUS
HWTACACS
RADIUS
Adopts TCP, providing more reliable network
transmission.
Adopts UDP.
Encrypts the entire message except the HWTACACS
header.
Encrypts only the password field in authentication
message.
Separates authentication from authorization. For
example, you can use one TACACS server for
authentication and another TACACS server for
authorization.
Combines authentication and authorization.
Is more suitable for security control.
Is more suitable for accounting.
Supports configuration command authorization.
Does not support.
In a typical HWTACACS application (as shown in
), a terminal user needs to log into the
device to perform some operations. As a HWTACACS client, the device sends the username and
password to the TACACS server for authentication. After passing authentication and being authorized,
the user successfully logs into the switching engine to perform operations.