Introduction to nd detection – H3C Technologies H3C S3100 Series Switches User Manual
Page 912
1-9
z
Router Advertisement (RA)
z
Redirect
The ND protocol functions powerfully, but without any security mechanism, it is apt to be used by
attackers.
ND attacks usually come from users. Normally, when the device Switch is a Layer-2 access device, ND
multiple packets sent by users are broadcast on the VLAN, and ND unicast packets are forwarded on
Layer 2. Attackers can imitate other users and gateways to send forged ND packets and attack the
network.
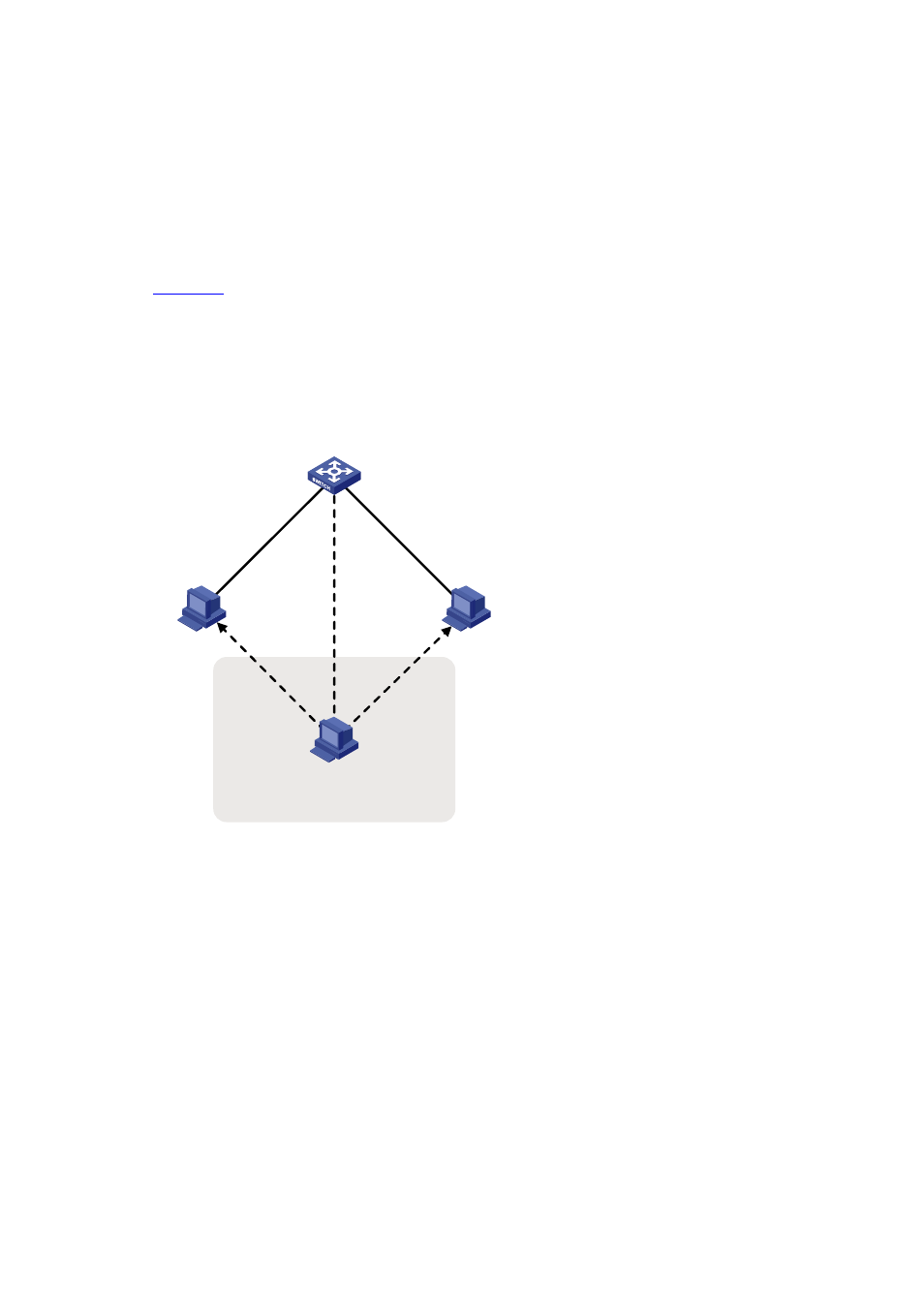
In
Figure 1-5
, Host A communicates with Host C through a switch. To intercept the traffic between Host
A and Host C, the hacker (Host B) forwards invalid ND packets to Host A and Host C respectively,
causing the two hosts to update the MAC address corresponding to the peer IPv6 address in their ND
entry with the MAC address of Host B. Then, the traffic between Host A and C will pass through Host B
which acts like a “man-in-the-middle” that may intercept and modify the communication information.
Figure 1-5 ND attack diagram
Switch
Host A
Host B
IP_A
MAC_A
IP_B
MAC_B
IP_C
MAC_C
Host C
Forged
ND packets
Forged
ND packets
A forged ND packet has the following features:
z
The source MAC address in the forged ND packet is inconsistent to that in the link layer address
option.
z
The mapping between the source IPv6 address and MAC address in the forged ND packet is not
real for legal users.
Introduction to ND Detection
The ND detection is mainly used in the access device to check users legality. Forward the ND packets
of legal users, otherwise, discard them directly to prevent the attack of imitated users and gateways.
The ND detection divides the ports on the access device into two types: ND trusted ports and untrusted
ports
z
For the trusted ports, the ND detection does not check the users legality;
z
For the untrusted ports, the received RA and RR messages are considered illegal and discarded
directly. If other types of ND packets are received, the ND detection checks their legality to prevent
the attack of imitated users.