Enabling arp source mac address consistency check, Arp attack defense configuration example i, Network requirements – H3C Technologies H3C S3100 Series Switches User Manual
Page 966: Network diagram, Configuration procedures
5
z
If they are not consistent, the ARP packet is considered invalid and the corresponding ARP entry is
not learned.
Enabling ARP Source MAC Address Consistency Check
To do…
Use the command…
Remarks
Enter system view
system-view
—
Enable ARP source MAC
address consistency check
arp anti-attack valid-check
enable
Required
Disabled by default.
ARP Attack Defense Configuration Example I
Network Requirements
Host A and Host B are connected to Gateway through an access switch (Switch). The IP and MAC
addresses of Gateway are 192.168.100.1/24 and 000D-88F8-528C. To prevent gateway spoofing
attacks from Host A and Host B, configure ARP packet filtering based on the gateway’s IP and MAC
addresses on Switch.
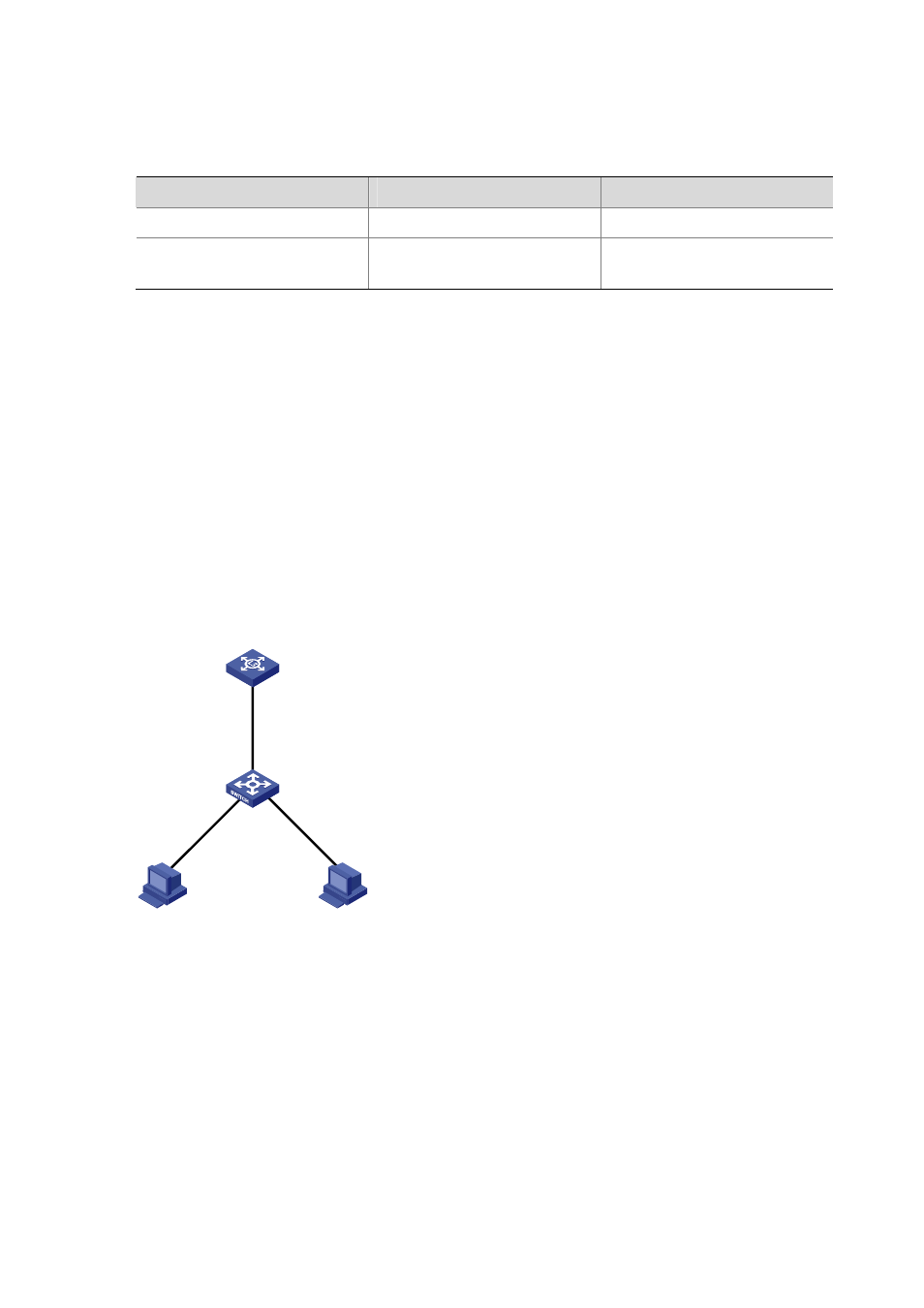
Network Diagram
Figure 1-2 Network diagram for ARP attack defense I
Eth1/0/1
Eth1/0/2
Eth1/0/3
Switch
Vlan-int 1
192.168.100.1/24
MAC:000D-88F8-528C
Gateway
Host A
Host B
Configuration Procedures
# Enter system view.
<Switch> system-view
# Configure ARP packet filtering based on the gateway’s IP and MAC addresses on Ethernet 1/0/1.
[Switch] interface Ethernet 1/0/1
[Switch-Ethernet1/0/1] arp filter binding 192.168.100.1 000d-88f8-528c
[Switch-Ethernet1/0/1] quit
# Configure ARP packet filtering based on the gateway’s IP address on Ethernet 1/0/2.