Asymmetric key algorithm, Ssh operating process, 2 ssh operating process – H3C Technologies H3C WX6000 Series Access Controllers User Manual
Page 607
64-2
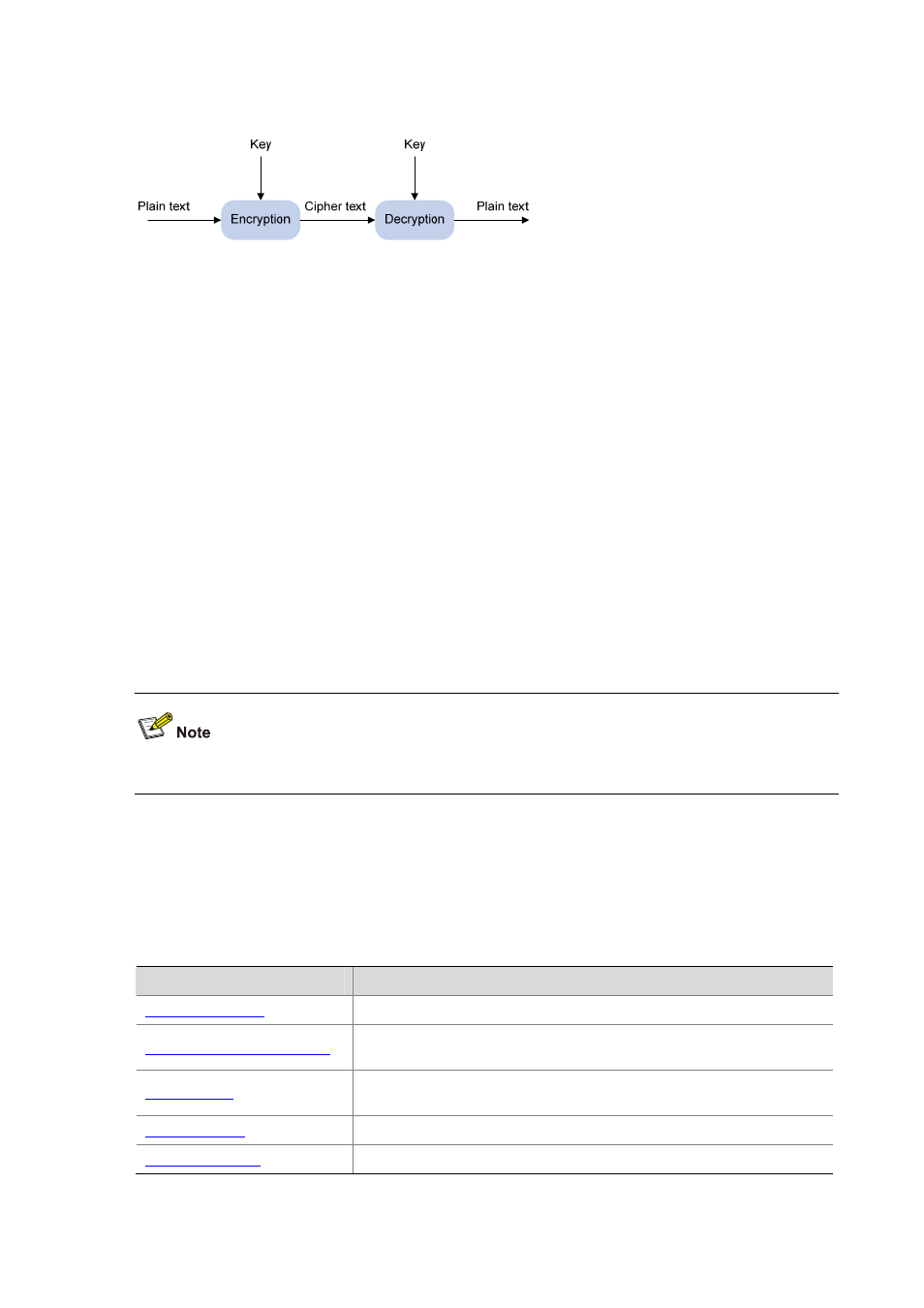
Figure 64-1
Encryption and decryption
Key-based algorithm is usually classified into symmetric key algorithm and asymmetric key algorithm.
Asymmetric Key Algorithm
Asymmetric key algorithm means that a key pair exists at both ends. The key pair consists of a private
key and a public key. The public key is effective for both ends, while the private key is effective only for
the local end.
Asymmetric key algorithm encrypts data using the public key and decrypts the data using the private
key, thus ensuring data security.
You can also use the asymmetric key algorithm for digital signature. For example, user 1 adds his
signature to the data using the private key, and then sends the data to user 2. User 2 verifies the
signature using the public key of user 1. If the signature is correct, this means that the data originates
from user 1.
Revest-Shamir-Adleman Algorithm (RSA) and Digital Signature Algorithm (DSA) are both asymmetric
key algorithms. RSA can be used for data encryption and signature, whereas DSA is used for
signatures only.
Currently, SSH2 supports both RSA and DSA.
SSH Operating Process
The session establishment between an SSH client and the SSH server involves the following five
stages:
Table 64-1
Stages in establishing a session between the SSH client and the server
Stages
Description
SSH1 and SSH2 are supported. The two parties negotiate a version to use.
SSH supports multiple algorithms. The two parties negotiate an algorithm
for communication.
The SSH server authenticates the client in response to the client’s
authentication request.
This client sends a session request to the server.
The client and the server start to communicate with each other.