66 ssl configuration, Ssl overview, Ssl configuration – H3C Technologies H3C WX6000 Series Access Controllers User Manual
Page 637
66-1
66
SSL Configuration
When configuring SSL, go to these sections for information you are interested in:
z
z
z
Displaying and Maintaining SSL
z
The term switch in this document refers to a switch in a generic sense or an access controller
configured with the switching function unless otherwise specified.
SSL Overview
Secure Sockets Layer (SSL) is a security protocol providing secure connection service for TCP-based
application layer protocols, for example, HTTP protocol. It is widely used in E-business and online bank
fields to provide secure data transmission over the Internet.
SSL provides these security services:
z
Confidentiality: SSL encrypts data using a symmetric encryption algorithm and the key generated
during the handshake phase.
z
Authentication: SSL supports authenticating both the server and the client through certificates, with
the authentication of the client being optional.
z
Reliability: SSL uses key-based message authentication code (MAC) to verify message integrity.
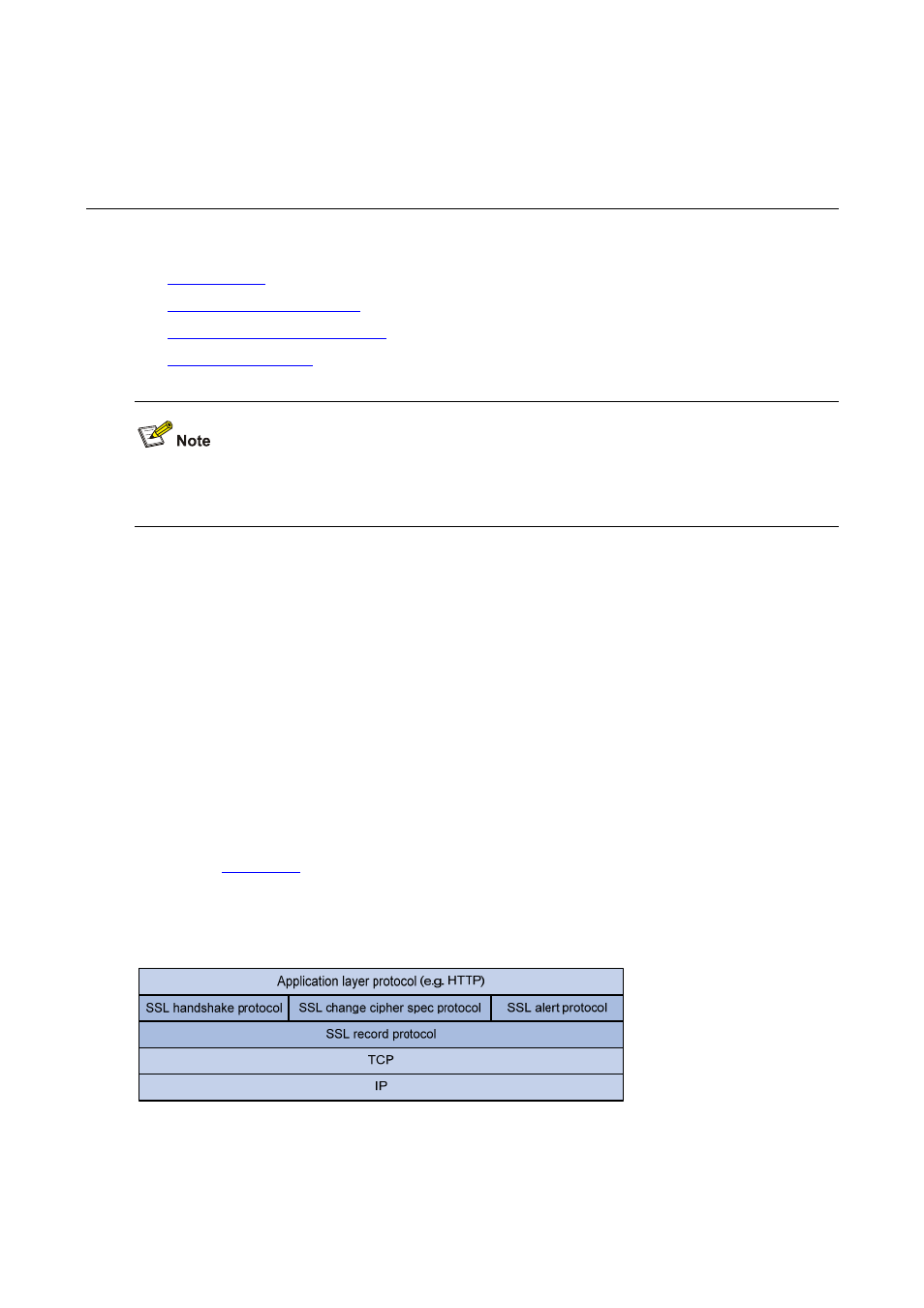
As shown in
, the SSL protocol consists of two layers of protocols: the SSL record protocol at
the lower layer and the SSL handshake protocol, change cipher spec protocol, and alert protocol at the
upper layer.
Figure 66-1
SSL protocol stack
z
SSL handshake protocol: Responsible for establishing a session between a client and the server. A
session consists of a set of parameters such as the session ID, peer certificate, cipher suite
(including key exchange algorithm, data encryption algorithm and MAC algorithm), compression