Configuring rogue device detection, Recommended configure procedure, Configuring ap operating mode – H3C Technologies H3C WX3000E Series Wireless Switches User Manual
Page 487
471
4.
If there is no match, or no blacklist entries exist, the frame is considered valid and will be further
processed.
A static blacklist or white list configured on an AC applies to all APs connected to the AC, while a
dynamic blacklist applies to APs that receive attack frames.
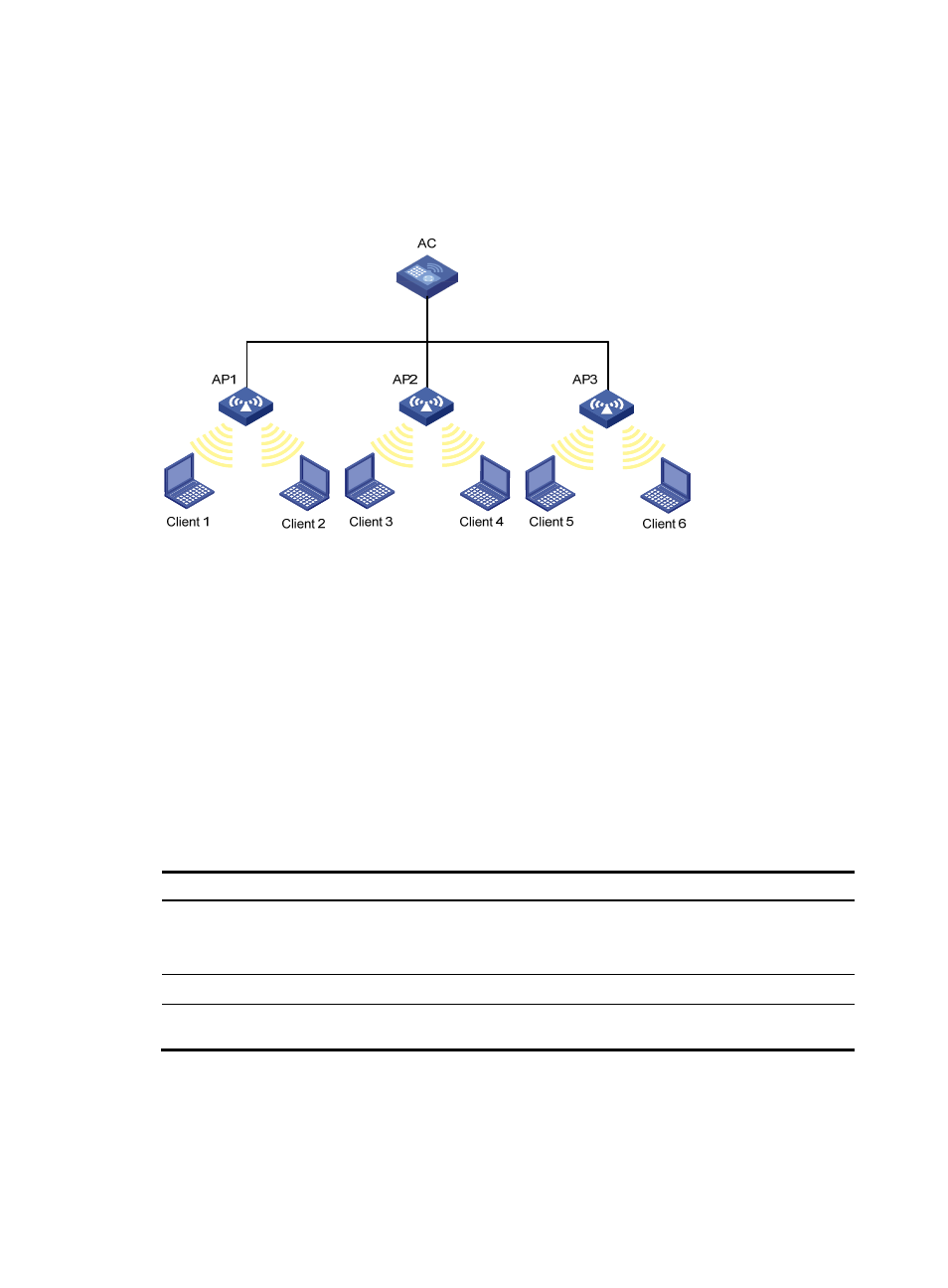
Figure 502 Network diagram for WLAN client access control
•
In the topology above, three APs are connected to an AC. Configure white list and static blacklist
entries on the AC, which will send all the entries to the APs. If the MAC address of a station, Client
1 for example, is present in the blacklist, it cannot access any of the APs. If only Client 1 is present
in the white list, it can access any of the APs, and other clients cannot access any of the APs.
•
Enable dynamic blacklist function on the AC. If AP 1 receives attack frames from Client 1, a dynamic
blacklist entry is generated in the blacklist, and Client 1 cannot associate with AP 1, but can
associate with AP 2 or AP 3. If AP 2 or AP 3 receives attack frames from Client 1, a new dynamic
blacklist entry is generated in the blacklist.
Configuring rogue device detection
Recommended configure procedure
Step Remarks
1. Configuring AP operating mode
Required.
By default, the AP operates in normal mode and only
provides WLAN data services.
2. Configuring detection rule lists
Required.
3. Enabling countermeasures and configuring
aging time for detected rogue devices
Optional.
Configuring AP operating mode
1.
Select Security > Rogue Detection
from the navigation tree.