2 eap termination mode – PLANET WGSW-52040 User Manual
Page 366
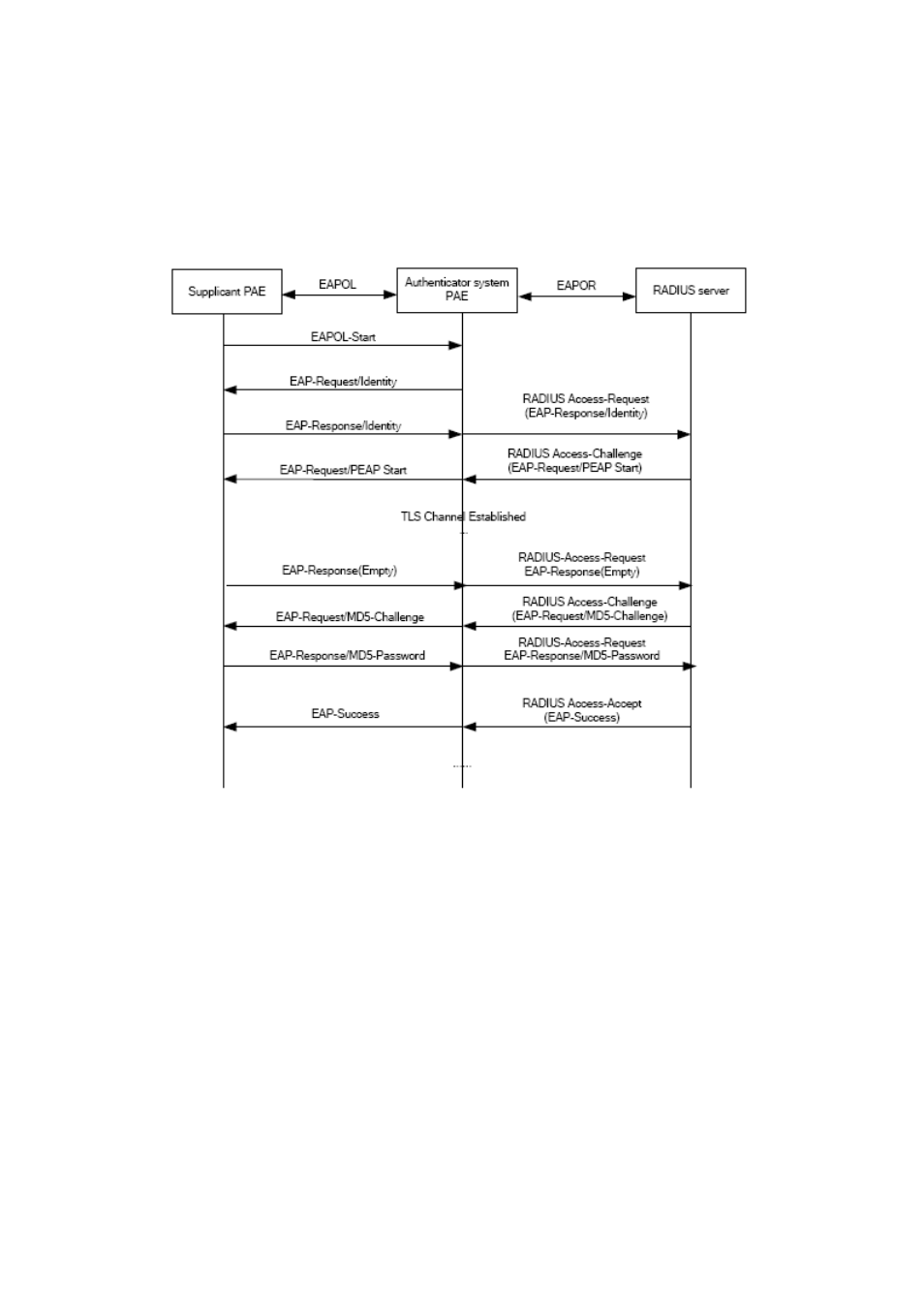
EAP-PEAP is brought up by Cisco, Microsoft and RAS Security as a recommended open
standard. It has long been utilized in products and provides very good security. Its design of
protocol and security is similar to that of EAP-TTLS, using a server’s PKI certificate to
establish a safe TLS tunnel in order to protect user authentication.
The following figure illustrates the basic operation flow of PEAP authentication method.
Figure 42-11: the Authentication Flow of 802.1x PEAP
42.1.5.2 EAP Termination Mode
In this mode, EAP messages will be terminated in the access control unit and mapped into
RADIUS messages, which is used to implement the authentication, authorization and
fee-counting. The basic operation flow is illustrated in the next figure.
In EAP termination mode, the access control unit and the RADIUS server can use PAP or
CHAP authentication method. The following figure will demonstrate the basic operation flow
using CHAP authentication method.
42-145