6 the extension and optimization of 802.1x, 6 the extension and optimization of 802.1x -146 – PLANET WGSW-52040 User Manual
Page 367
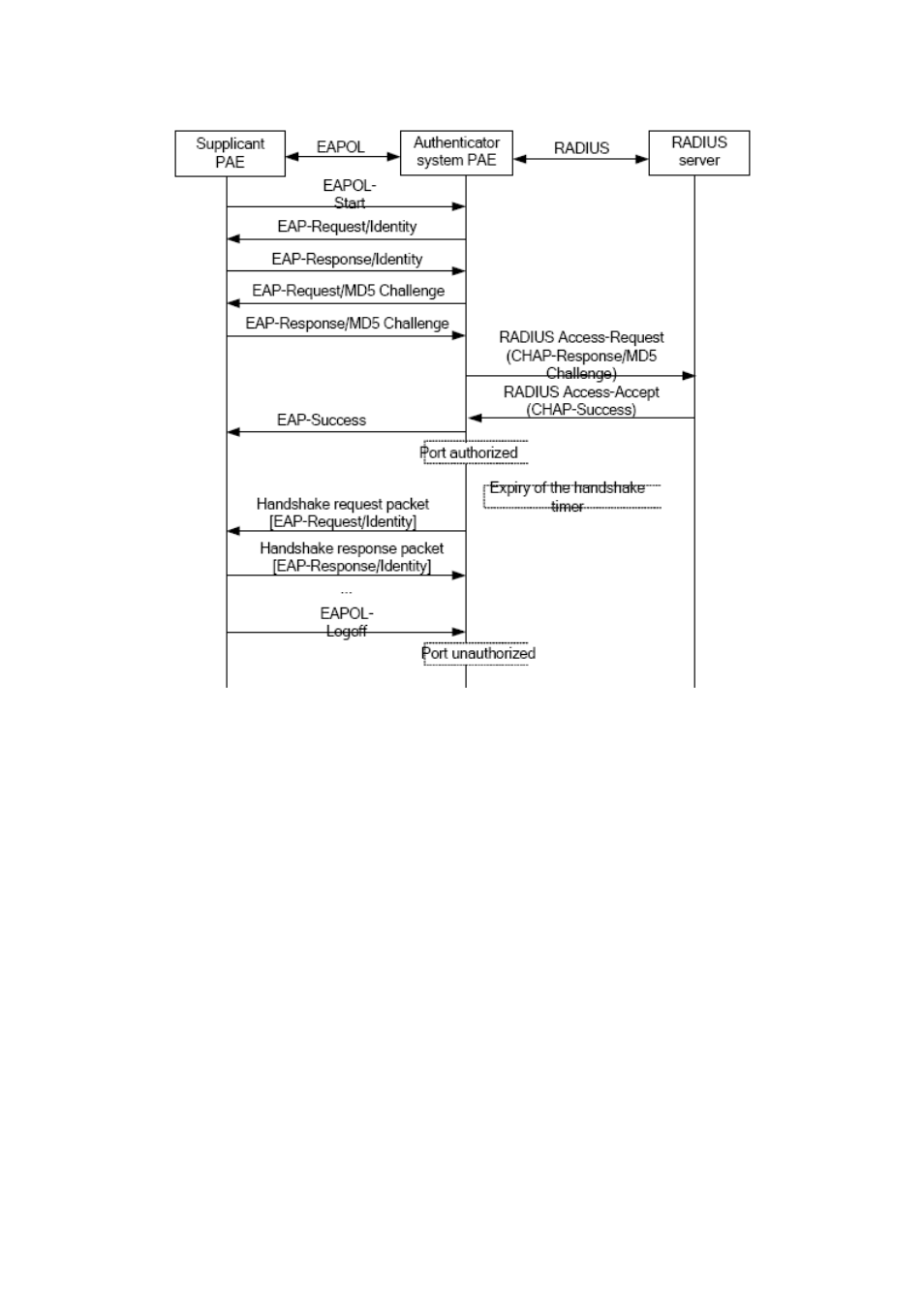
Figure 42-12: the Authentication Flow of 802.1x EAP Termination Mode
42.1.6 The Extension and Optimization of 802.1x
Besides supporting the port- based access authentication method specified by the protocol,
devices also extend and optimize it when implementing the EAP relay mode and EAP
termination mode of 802.1x.
Supports some applications in the case of which one physical port can have more than
one users
There are three access control methods (the methods to authenticate users): port-based,
MAC-based and user-based (IP address+ MAC address+ port).
When the port-based method is used, as long as the first user of this port passes the
authentication, all the other users can access the network resources without being
authenticated. However, once the first user is offline, the network won’t be available
to all the other users.
42-146